IVR Dashboard
The Integrated Vulnerability Remediation (IVR) Dashboard is your central hub for managing security risks. It displays vulnerability data automatically fetched from external scanners (such as Tenable). The system checks for new data sources every 10 minutes and refreshes data for existing data sources every 12 hours. This consolidated view supports the correlation of external scanner data with BigFix content, enabling you to efficiently process the remediation flow.
IVR Dashboard Layout
The IVR Dashboard comprises two primary areas: the Header section and the main Workspace. The Header section establishes the context and contains the Action Buttons for global controls. The main Workspace serves as the primary display area for vulnerability data.
The layout of this workspace adapts dynamically based on your datasource configuration:
-
New Users: The dashboard loads the Datasource Configuration page, focusing on a single action to get you started.
-
Existing Users: The dashboard loads the vulnerability data in List view by default but can be toggled to Overview for visual summaries.
For new users, the dashboard is streamlined to facilitate initial setup.
-
Header: The page title – "Integrated Vulnerability Remediation".
-
Action Buttons: A primary button, Create Datasource, is displayed in the top right. You must configure a data source first to view the vulnerability-related data. For more information about adding a data source, see Creating New Datasource.
-
Workspace: The main content area displays a "No Data Available" status until a datasource is configured.
Once a datasource is configured, the dashboard provides two distinct views: List View (Default) and Overview.
-
By default, the Main Workspace displays the List View. This interface presents a comprehensive table of imported vulnerabilities, enabling you to sort and filter data, export records, and select specific items to initiate the remediation process.
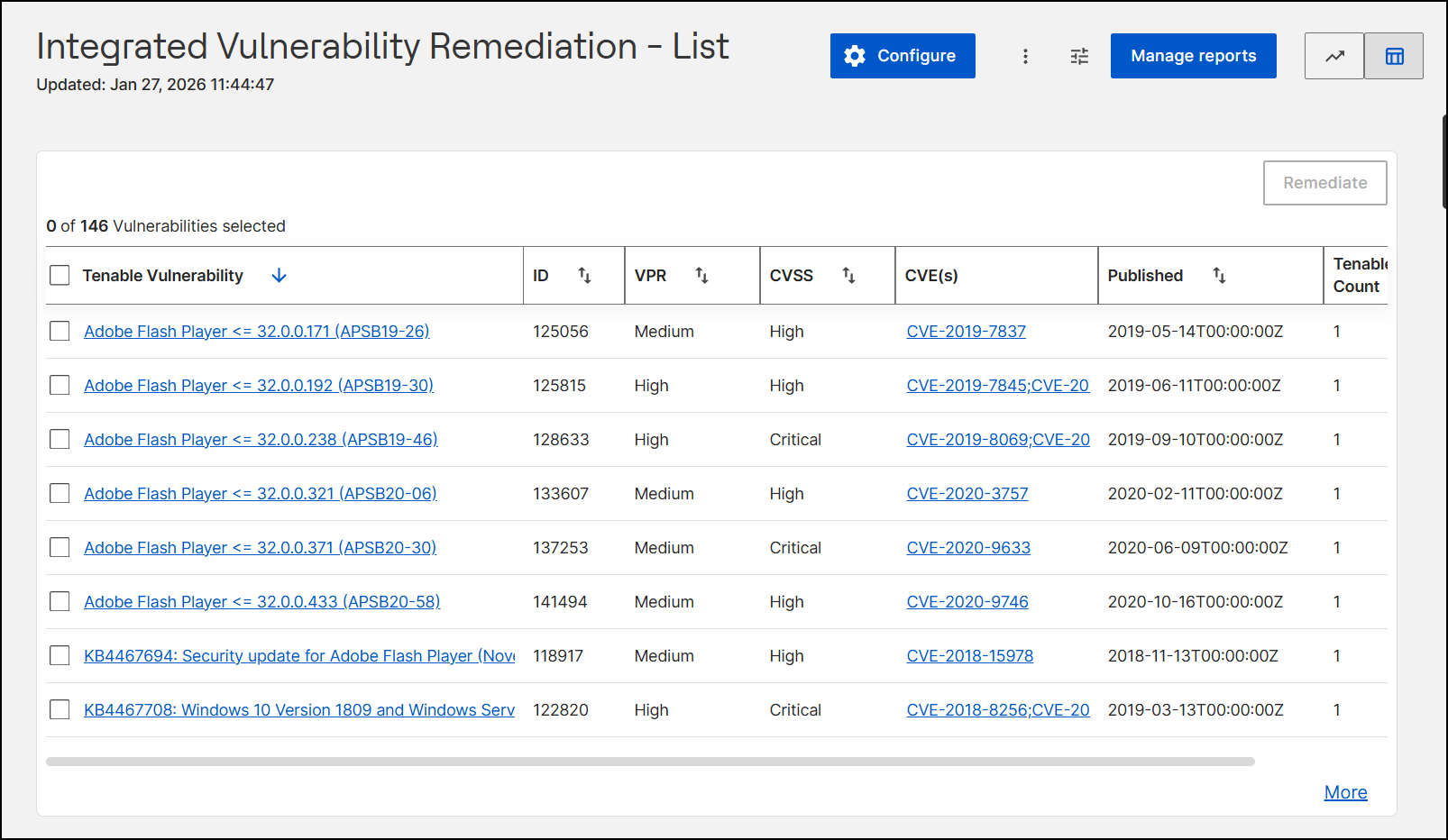
- Header Section: The header section in List view
displays:
- Page Title: "Integrated Vulnerability Remediation - List"
- Updated: Located below the title, this timestamp indicates the start time of your current session in your local timezone (for example, Jan 27, 2026 11:44:47).
-
Configure: Select Configure to open the Configure Datasource page, where you can manage datasource integrations.
-
Export: Select the (Vertical Ellipsis icon) to download vulnerability data as a CSV or Excel file.
-
Filter: Select the (Sliders icon) to refine the grid data based on specific criteria (e.g., ID, CVE ID, published date).
-
Manage Reports: Select Manage Reports to open the reporting interface.
-
View Toggles: Select the Graph or Table icon to switch between the Overview (graphical) and List (tabular) views.
- Workspace: The workspace displays a data grid divided into
two parts:
- Remediate: Select a record in the data grid to enable the Remediate button. Select Remediate to open the remediation workflow. See IVR Remediate flow page for more details.
- Data Grid: This table represents a list of
detected vulnerabilities, allowing you to review and
manage individual vulnerability instances in a structured
and actionable format.
The following table describes the columns available in the Tenable Vulnerability data grid:
Table 1. Column Name Description Data Type (Selection Checkbox) A control that allows you to select one or multiple rows to perform actions (like Remediate). A master checkbox at the table header enables bulk selection. Interactive Checkbox Tenable Vulnerability The descriptive name of the security vulnerability as identified by the vulnerability scanner (Tenable). This text is hyperlinked, leading to more details about the specific vulnerability displayed under the following tabs: - Vulnerability Information: This includes a brief summary, a detailed description, and a solution for the specific vulnerability. You can also fix the vulnerability from here by clicking Remediate and following the steps given in the IVR Remediate flow page.
- Contents: It shows the Fixlets that are related to this specific vulnerability. Select a Content Name to open more details about a specific Fixlet on the Fixlet details page.
- Devices: It shows the devices that the specific Fixlet can be applied to. Click on Devices to go to Device Details page.
- Deployment: It shows the deployment data. To learn how to deploy the Fixlet, go to Deploying Fixlets page.
Text Link (Hyperlink) ID A unique numeric identifier assigned to the specific vulnerability instance within the system for tracking and reference purposes. Numeric VPR Vulnerability Priority Rating. A dynamic rating (e.g., Low, Medium, High) that helps prioritize remediation by combining technical severity with threat intelligence (specific to Tenable's scoring). Categorical Text CVSS Common Vulnerability Scoring System. An industry-standard score (e.g., Critical, High) that reflects the intrinsic severity of the vulnerability based on its technical characteristics. Categorical Text CVE(s) Common Vulnerabilities and Exposures. A list of standardized identifiers (e.g., CVE-2019-7837) that reference the vulnerability in the public National Vulnerability Database (NVD). These are hyperlinked for external reference. Alphanumeric Link Published The date and time (in ISO 8601 format) when the vulnerability was publicly disclosed or added to the database. Date/Time (Timestamp) Tenable Count Displays the number of vulnerable devices identified by Tenable. Numeric
- Header Section: The header section in List view
displays:
- Overview
When you toggle to the Overview, the interface shifts to visual analytics.
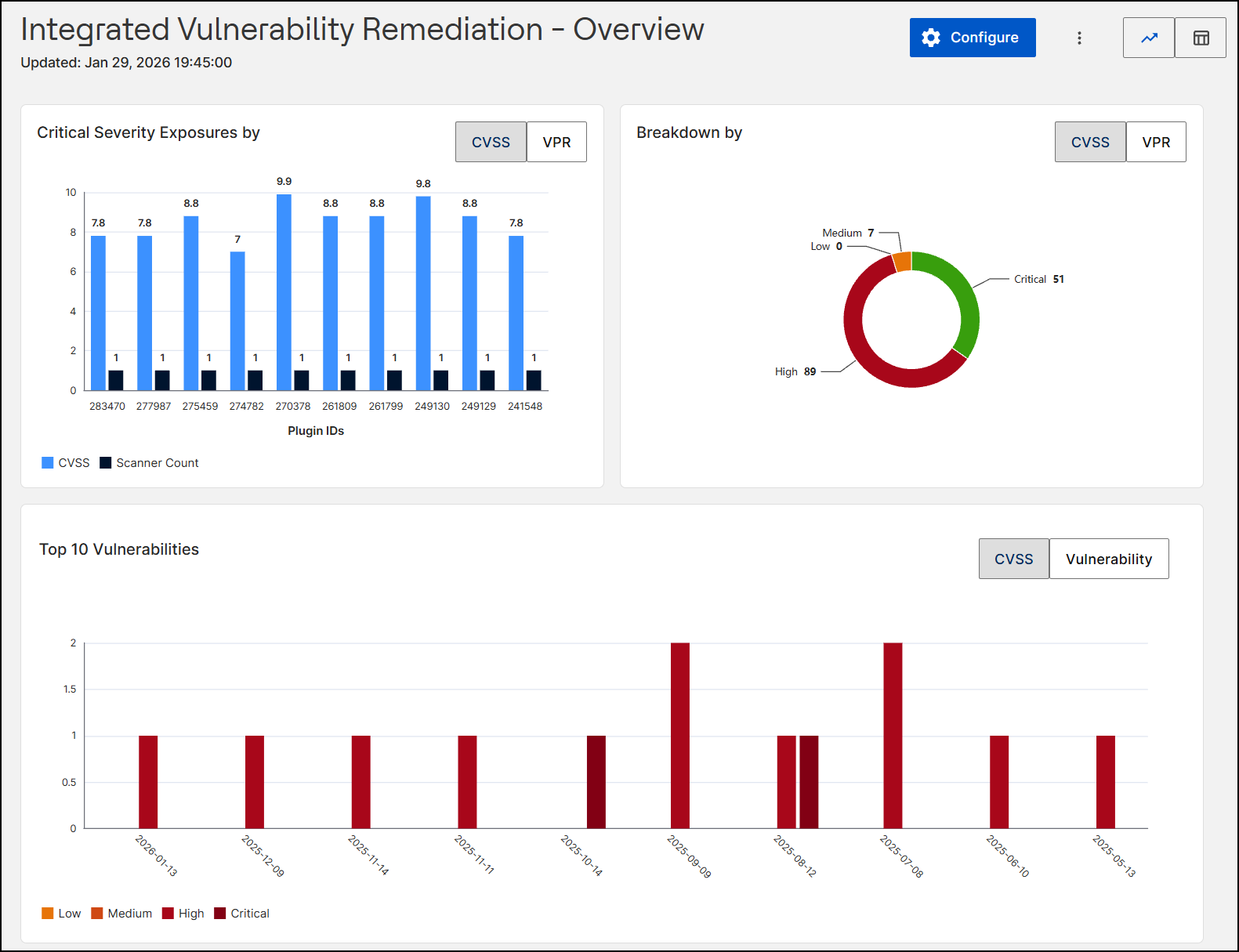
-
Header Section: The header in the Overview view displays the following elements:
-
Page Title: "Integrated Vulnerability Remediation - Overview".
- Updated: Located below the title, this timestamp indicates the start time of your current session in your local timezone (for example, Jan 27, 2026 11:44:47).
- Configure: Select Configure to open the Configure Datasource page, where you can manage datasource integrations.
- Export: Select the Vertical Ellipsis icon to download graphical reports as a JPEG, PNG, or PDF file.
- View Toggles: Select the Graph or Table icon to switch between the Overview (graphical) and List (tabular) views.
Note: The Filter (Sliders icon) and Manage Reports button are hidden in this view. -
-
Workspace: The workspace presents vulnerability trends using interactive charts:
-
Critical Severity Exposures by: This clustered bar chart visualizes vulnerabilities based on their Plugin IDs. For each ID, it plots the Severity Score (Light Blue) and Scanner Count (Dark Blue) side-by-side, allowing you to correlate the risk level with its detection frequency. You can toggle the view to base the analysis on either CVSS or VPR scoring models.
-
Breakdown by: A donut chart that shows the distribution of vulnerabilities by severity level (for example, Critical vs. High). You can toggle the view by CVSS or VPR.
-
Top 10 Vulnerabilities: This timeline bar chart visualizes the most significant security risks in your environment. It plots vulnerability counts against publication dates using a bar chart color-coded by severity (from Low to Critical). The timeline focuses exclusively on the dates associated with the ten highest-ranked risks (based on severity and frequency). You can toggle the view between CVSS and Vulnerability to analyze the distribution by severity score or specific threat.
-
-