ASoC and GitLab
Use AppScan on Cloud with GitLab to run static analysis security testing (SAST) against the files in your repository on every merge request, thus preventing vulnerabilities from reaching the main branch. Results are stored in AppScan on Cloud.
Register
If you don't have an account, register on HCL AppScan on Cloud (ASoC) to generate your API key and API secret.
Setup
- Generate your ASoC API key and API
secret on the API page.
The API key and API secret map to the
ASOC_KEYandASOC_SECRETparameters for this action. Make note of the key and secret. - Create the application in ASoC.
Applications act as a container to store all scans that are related to the same project.
-
Copy the application ID. Select and then click Copy next to Application ID under Application details.
The application ID in ASoC maps to
APP_IDfor this integration.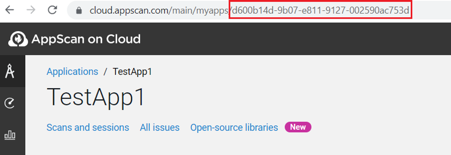
- Create three variables in GitLab. Select , and set the variables as follows:
Variable Value APP_IDApplication ID from ASoC ASOC_KEYAPI key from ASoC ASOC_SECRETAPI secret from ASoC 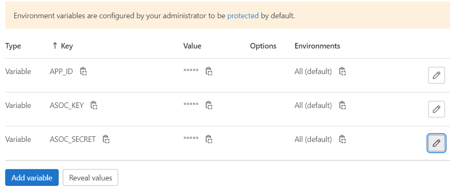
- Copy .gitlab-ci.yaml and Dockerfile into your GitLab repository root.
- Build your own runner. Select and follow the steps under Specific Runners.
- On the system on which you are setting up the GitLab runner, log in and clone your GitLab repository if one does not already exist. Ensure that a Docker engine is installed on that machine.
- Build a new Docker image called saclient from the Dockerfile. Change
directory to the root of the repository and run the following command to build
the Docker
image:
docker build -t saclient .Important: The period at the end indicates the current directory. - In GitLab, to prevent merges if the scan fails, enable Pipelines must succeed at .
- Verify a new scan job is initiated when new merge requests are created at .
Example
- Download the binary for your
system:
sudo curl -L --output /usr/local/bin/gitlab-runner https://gitlab-runner-downloads.s3.amazonaws.com/latest/binaries/gitlab-runner-linux-amd64 - Set permission to execute:
sudo chmod +x /usr/local/bin/gitlab-runner - Create a GitLab Runner user:
sudo useradd --comment 'GitLab Runner' --create-home gitlab-runner --shell /bin/bash - Install and run as a service:
sudo gitlab-runner install --user=gitlab-runner --working-directory=/home/gitlab-runner sudo gitlab-runner start - Register the runner:
sudo gitlab-runner register --url https://gitlab.com/ --registration-token $REGISTRATION_TOKEN
Additional Information
The current yaml script contains a
sample of a security policy check that fails the scan if the number of allowed
security issues exceeds a certain threshold. The sample has
maxIssuesAllowed set to 200.