CodeSweep Github Action
The HCL AppScan CodeSweep for GitHub action enables you to check your code on every pull request. The action identifies vulnerabilities in changed code with every update. But more than just identifying issues, the HCL AppScan CodeSweep for GitHub extension tells you what you need to know to mitigate issues — before they make it to the main branch.
Tutorial
Register
Register on HCL AppScan on Cloud (ASoC) to generate your API key/secret.
Setup
- After logging into ASoC, go to
the API page to generate your API key/secret
pair. These must be used in the
asoc_keyandasoc_secretparameters for the action. Store these parameters as secrets in your repository.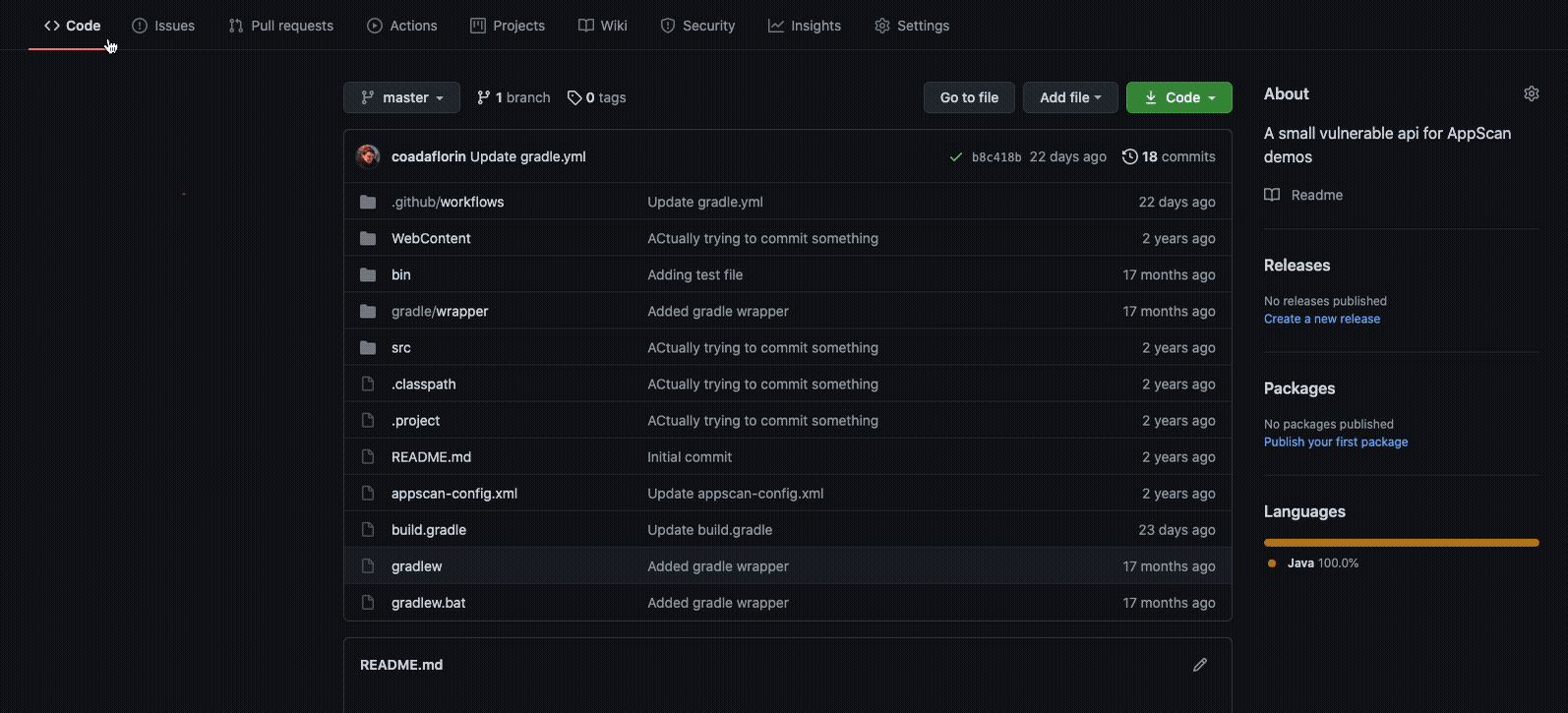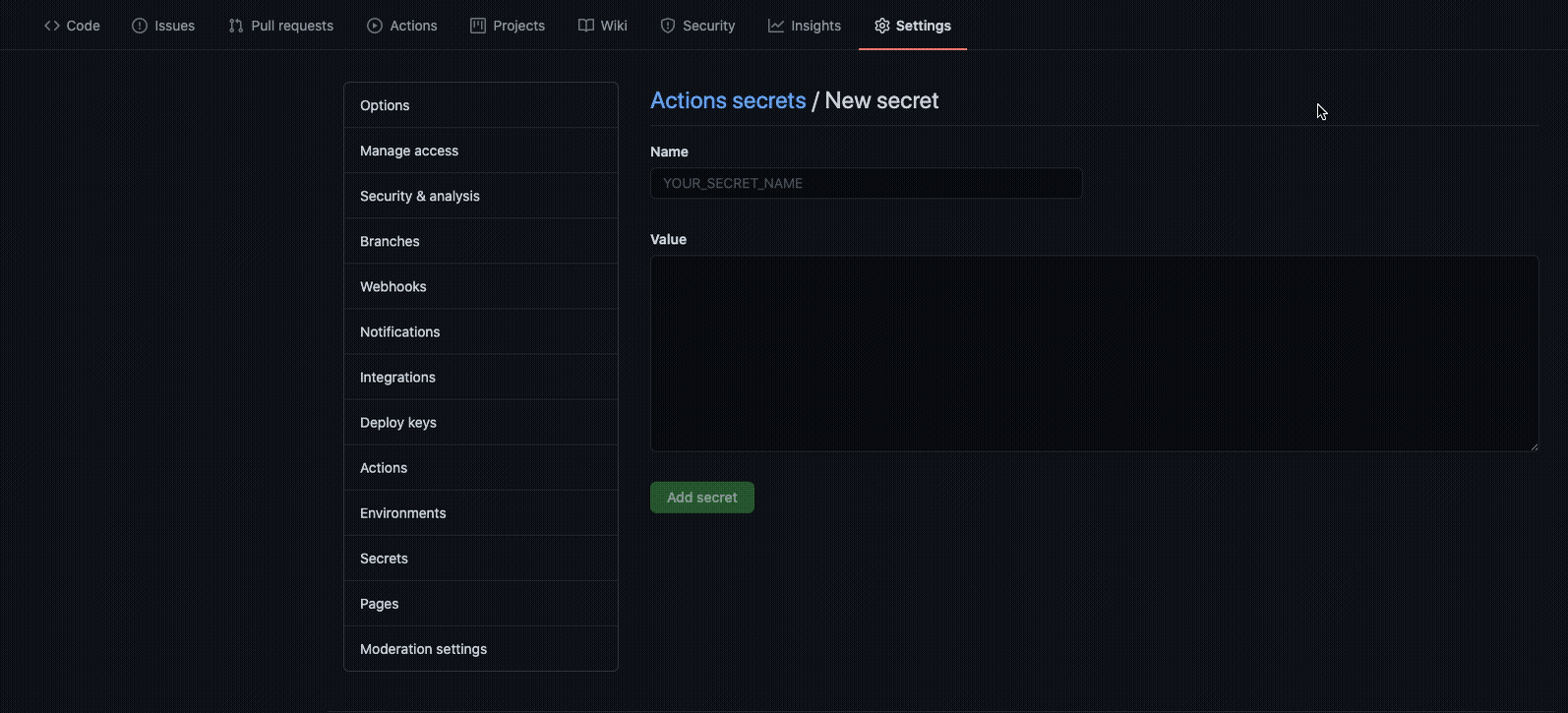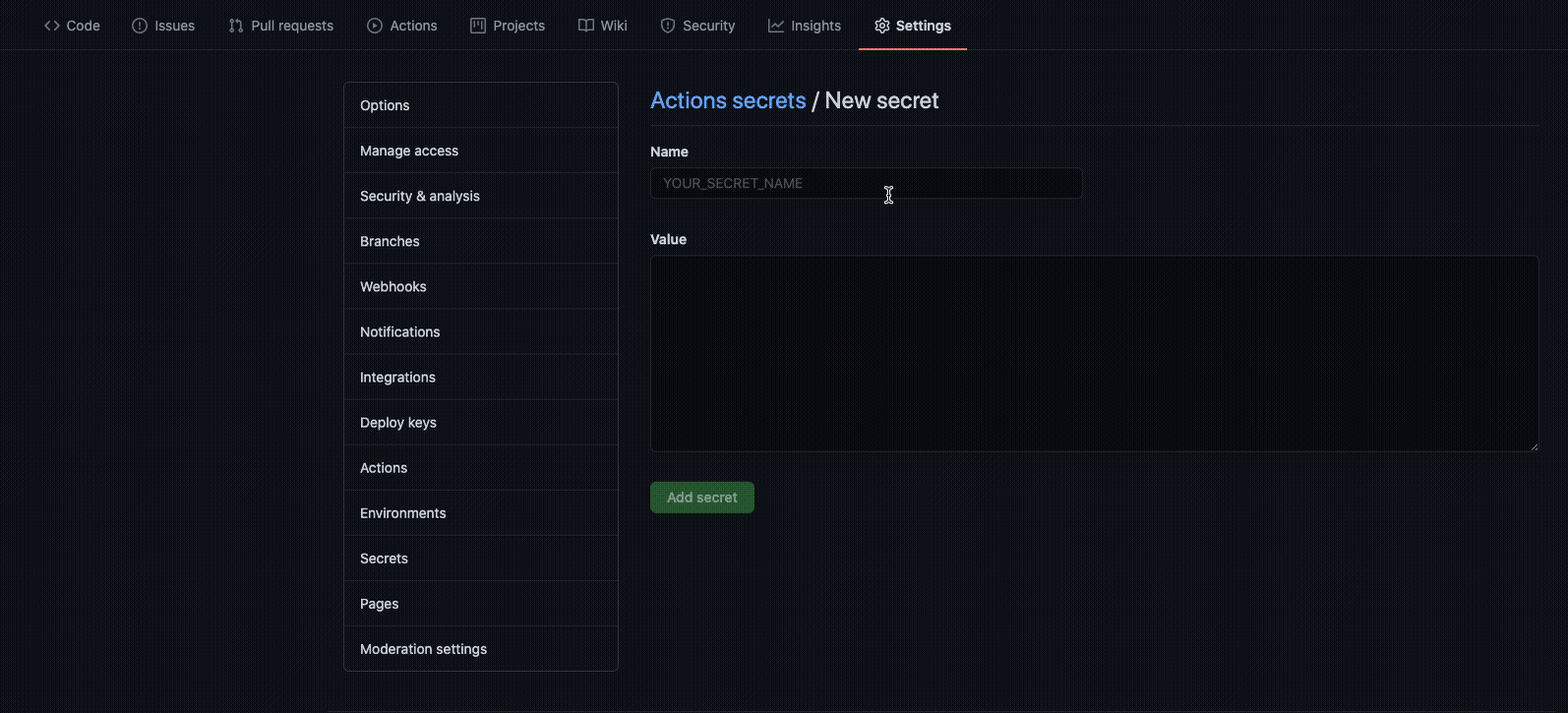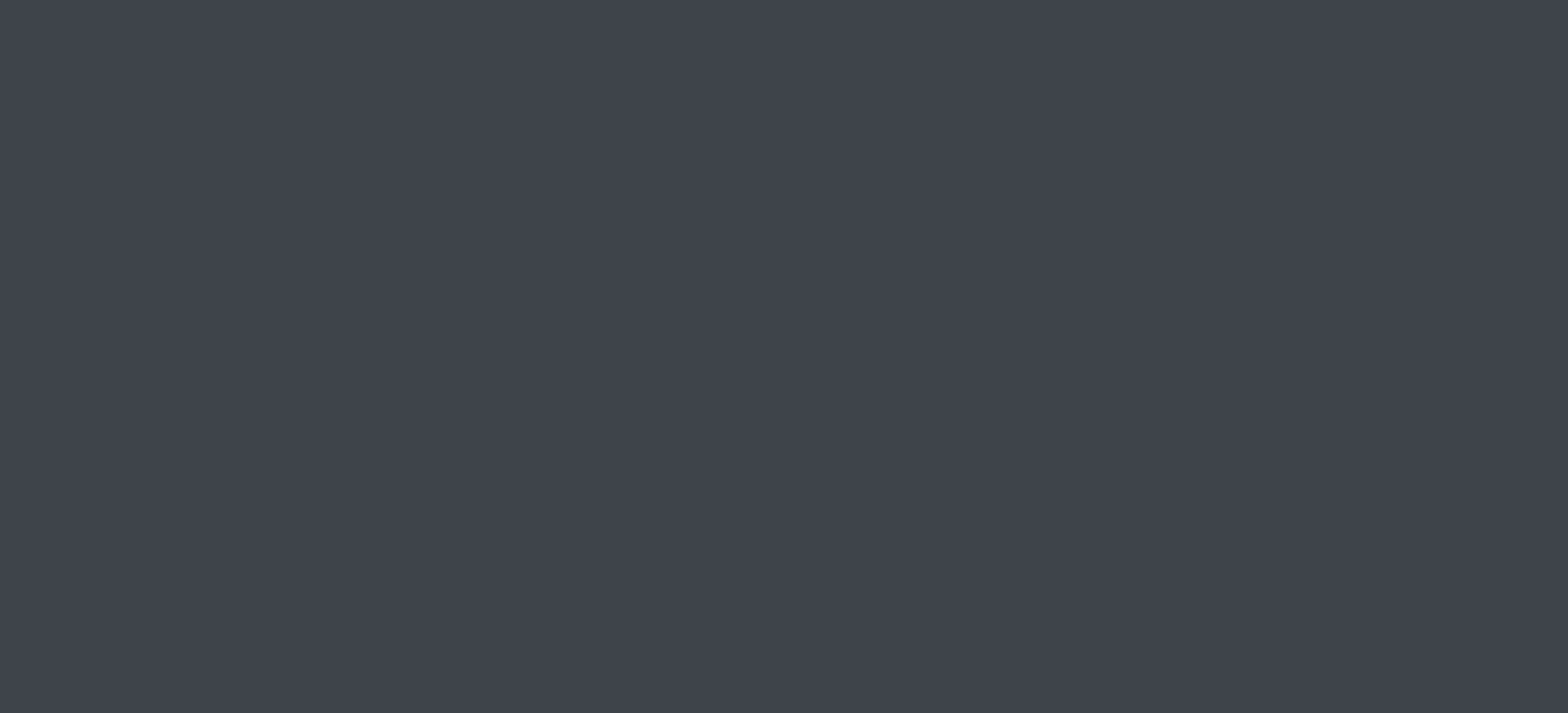
- Ensure that the Workflow permissions for your repository are set to Read and write permissions. This allows CodeSweep to scan your files and create checkruns and annotations for the issues it finds. Access these settings at .
- To scan code changes when a pull request is opened, add the following file
to your repository under
.github/workflows/codesweep.ymlor update an existing workflow file:name: "HCL AppScan CodeSweep" on: pull_request: types: [opened,synchronize] jobs: scan: runs-on: ubuntu-latest steps: - name: Checkout uses: actions/checkout@v4 with: fetch-depth: 0 - name: Run AppScan CodeSweep uses: HCL-TECH-SOFTWARE/appscan-codesweep-action@v2.1 env: GITHUB_TOKEN: ${{secrets.GITHUB_TOKEN}}Note: If you use checkout@v2 or later you must set fetch-depth to 0. For example:uses: actions/checkout@v2 with: fetch-depth: 0 - To publish security issues to ASoC when a pull
request is merged, add the following file to your repository under
.github/workflows/codesweep_publish.ymlor update an existing workflow file:name: "HCL AppScan CodeSweep" on: pull_request: types: [closed] jobs: publish: runs-on: ubuntu-latest steps: - name: Publish issues to ASoC uses: HCL-TECH-SOFTWARE/appscan-codesweep-action@v2.1 with: asoc_key: ${{secrets.ASOC_KEY}} asoc_secret: ${{secrets.ASOC_SECRET}} publish_on_merge: true application_id: <your ASoC application ID> env: GITHUB_TOKEN: ${{secrets.GITHUB_TOKEN}}
Optional parameters for scanning
| Parameter | Description | Values | Default |
|---|---|---|---|
status |
The status of the checks if any security issues are found. |
|
neutral |
service_url |
The URL of your AppScan 360° instance. Required for connections to AppScan 360°. | AppScan 360° service URL as defined during install. | AppScan on Cloud service URL (cloud.appscan.com) |
acceptssl |
Allow connections to an AppScan service with an untrusted certificate. Recommended for testing purposes only. |
with:
status: failureOptional parameter for publishing issues to AppScan on Cloud
| Parameter | Description | Values | Default |
|---|---|---|---|
service_url |
The URL of your AppScan 360° instance. Required for connections to AppScan 360°. | AppScan 360° service URL as defined during install. | AppScan on Cloud service URL (cloud.appscan.com) |
issue_status |
The status of issues that are published to ASoC. |
|
open |
scan_base_name |
ASoC | A timestamp is appended to the given base name. | GitHub_CodeSweep |
personal_scan |
ASoC |
|
true |
with:
publish_on_merge: true
application_id: 6c058381-17ca-e711-8de5-002590ac753d
issue_status: "inprogress"
scan_base_name: "CodeSweep"
personal_scan: trueExample
Annotations are added to the diff view, showing any vulnerable lines of code and a
checkrun is added to provide additional details, including good and bad code samples
and mitigation information.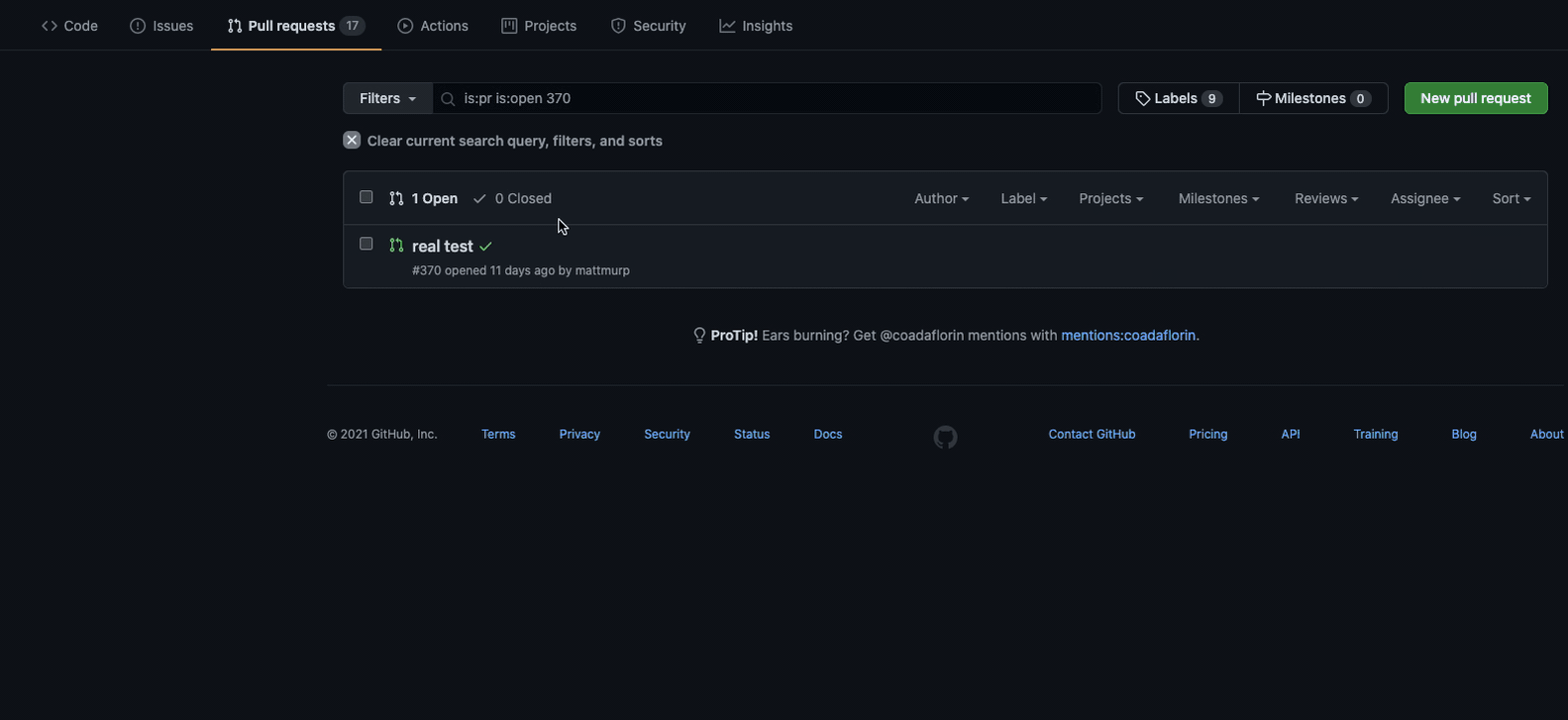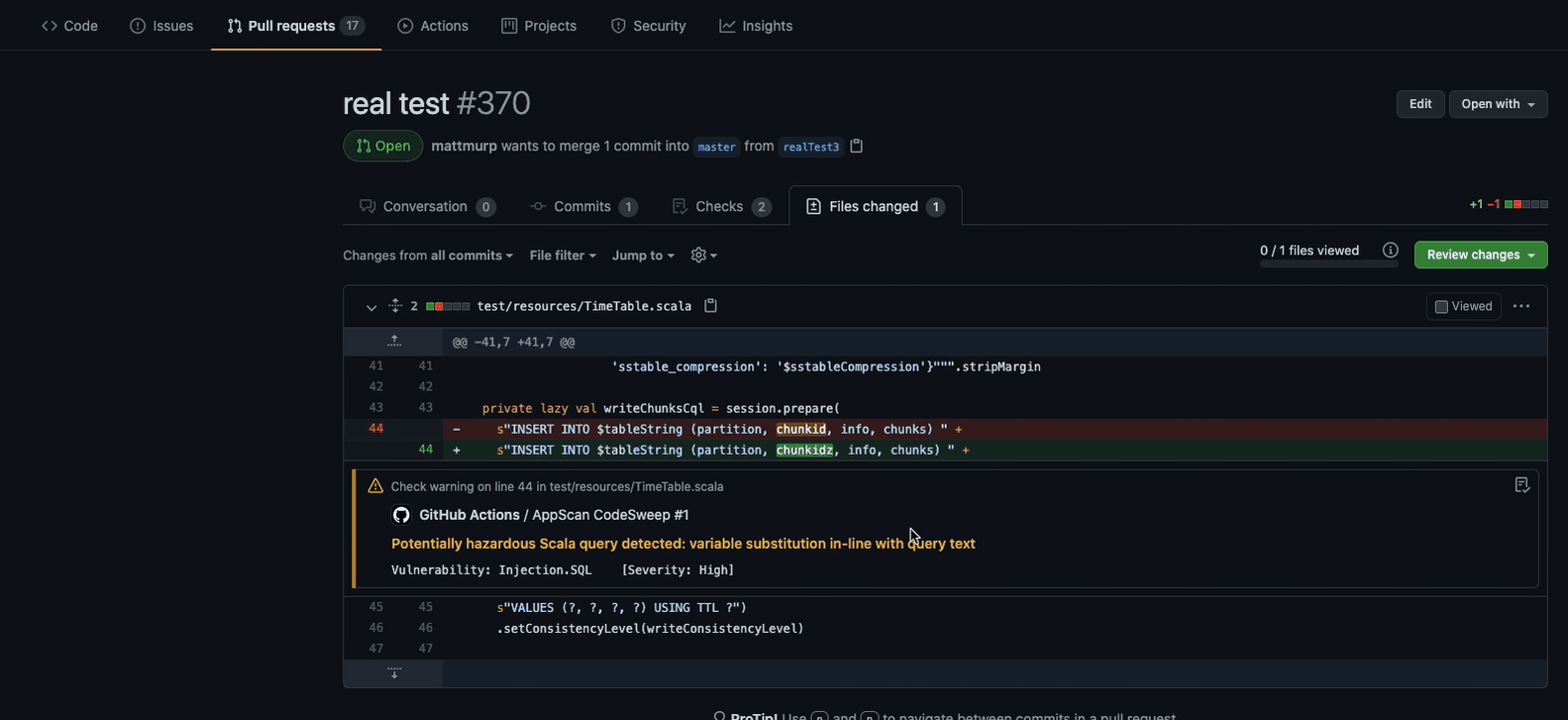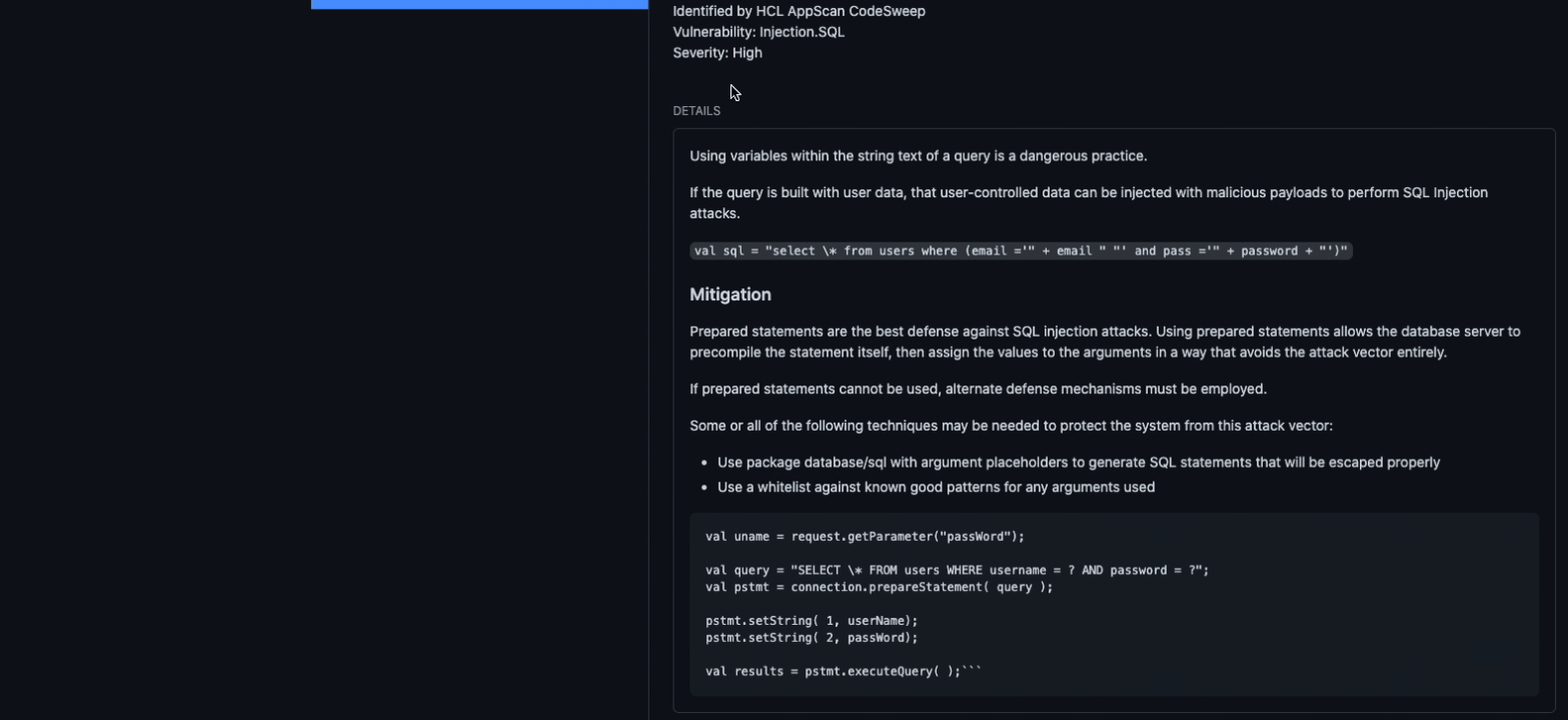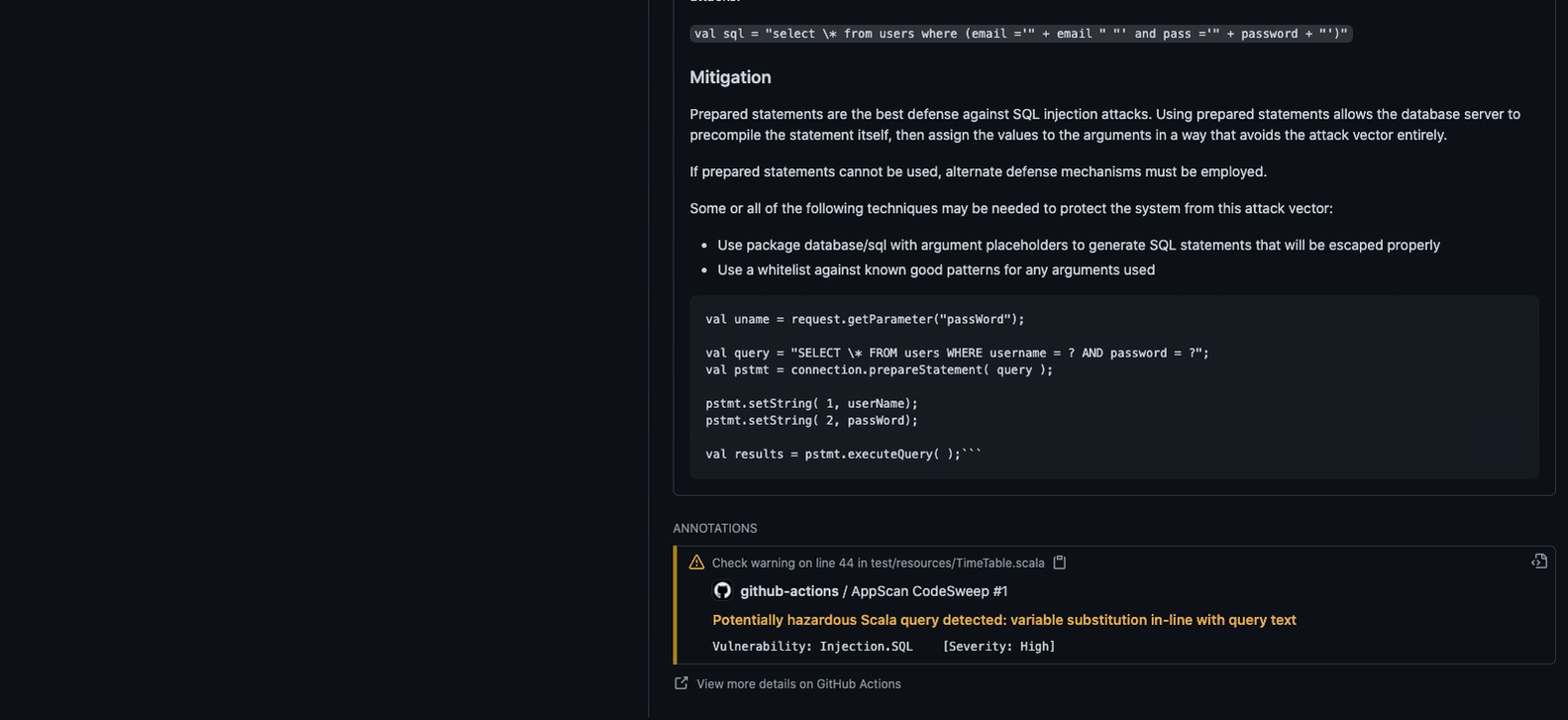
Supported languages
| Languages | |||
|---|---|---|---|
| Android-Java | Groovy | NodeJS | Ruby |
| Angular | IaC (Docker, K8s, Terraform) | Objective-C/Objective-C++ | Scala |
| Apex | Ionic | PHP | Swift |
| C/C++ | Java | PL/SQL | T-SQL |
| Cobol | JavaScript | Perl | TypeScript |
| ColdFusion | JQuery | Python | VueJS |
| Dart | Kotlin | React | .Net (C#, VB.NET, ASP.Net) |
| GoLang | Mootools | React Native | Xamarin |
Troubleshooting
Problem: The security scan runs, but no checkruns or annotations are created for the security issues that are found. The workflow log contains the error:
Error: Failed creating checkrun: HttpError: Resource not accessible by
integration
Resolution: This error indicates that the workflow does not have write permission to the repository, so CodeSweep is unable to create the checkruns and annotations. To fix this, go to and set Workflow permissions to Read and write permissions.
Join the community
Use the CodeSweep slack channel to report any feedback or ask general questions about the HCL AppScan CodeSweep action.