Configuring cloud plugins
Cloud plugins are installed with a base configuration that can be updated later on, primarily through the BigFix WebUI.
VMware cloud plugin secure connection
Starting from BigFix Version 11.0.4, you can install the vCenter certificates, on the system where you intend to install the VMware cloud plugin, in order to automatically open secure connections, by performing the following steps:
- Download the trusted root certificates from the vCenter Server system or vCenter Server Appliance. You can set the URL to <vCenter URL>/certs/download.zip
- The extension of the downloaded file must be .zip (The file is a ZIP file containing all certificates in the TRUSTED_ROOTS store, which is the site of the vCenter Server system or vCenter Server Appliance you are connecting to.
- Extract the ZIP file.
- The extracted folder includes files with the extension .0. .1, and so on, which are certificates, and files with the extension .r0, r1, and so on, which are Certificate Revocation List (CRL) files associated with the certificates.
- The full path of the trusted root certificate must be specified in the Fixlet 5424 -
Install BigFix Plugin for VMware Discovery in the Certificate full path field.
The full path format to be inserted is
<fullPath>/<file.extension>, an example of full path to insert is: C:/Users/Administrator/Desktop/certificate/1763543783.0
For more details about the certificates download and installation, see Download and install vCenter Server root certificates to avoid web browser certificate warning.
For more details about the managed trusted certificates, see Manage Trusted Root Certificates.
AWS cloud plugin FIPS mode connection
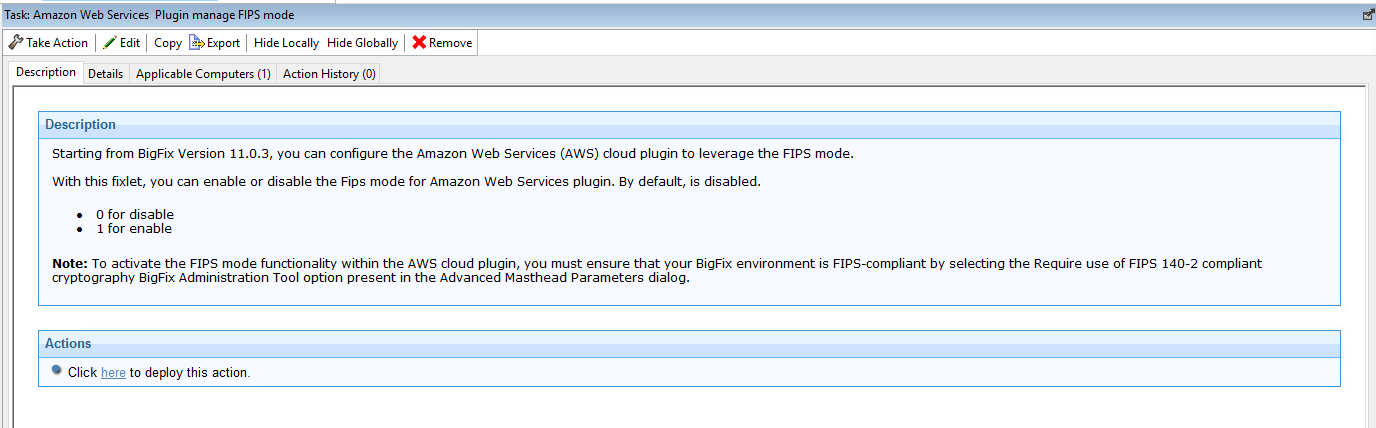
Starting from BigFix Version 11.0.3, you can configure the Amazon Web Services (AWS) cloud plugin to leverage the FIPS mode connection.
The Federal Information Processing Standard (FIPS) 140-3 publication is a US and Canadian government standard that defines security requirements for the encryption of modules that protect sensitive information.
- us-east-1
- us-east-2
- us-west-1
- us-west-2
- us-gov-east-1
- us-gov-west-1
- ca-central-1
- ca-west-1
To activate the FIPS connection functionality within the AWS cloud plugin, you must ensure that your BigFix environment is FIPS-compliant by selecting the Require use of FIPS 140-2 compliant cryptography BigFix Administration Tool option present in the Advanced Masthead Parameters dialog.
After selecting this option, it allows the adoption of FIPS encryption standards across all BigFix components.
The Plugin Portal is configured to use the FIPS encryption, and this configuration is then passed to the AWS cloud plugin.
The FIPS connection can be enabled by using the Discovery_UseFipsMode setting, in the PluginStore.db configuration file stored in the plugin portal installation folder.
The default setting value is 0 (disabled). You can enable the setting value by running the Amazon Web Services Plugin manage FIPS mode Task and specifying 1 as value.
Azure cloud plugin environment
parameter "myLabel" = "<my label>"
plugin store "AzureAssetDiscoveryPlugin" set "Environment_{parameter "myLabel"}"
value "<myEnv>" on "{parameter "action issue date" of action}"where <myEnv> is one of the admitted environments by Azure, targeting the Plugin Portal where the Azure cloud plugin is installed.
az cloud list --output tableDiscovery frequency
It is the frequency with which a cloud plugin runs the discovery of the related cloud resources. Cloud plugins are installed with a default discovery frequency of 120 minutes.
The discovery frequency can be updated from the Plugin Management section of the BigFix WebUI. There are also BES Support tasks that allow updating the discovery frequency of cloud plugins.
Discovery optimization
Starting from BigFix Version 11.0.2, the total discovery duration of time was optimized by using the multi-threading solution present in the cloud plugins.
- _<PluginName>_Discovery_MaxConcurrentRoutinesForCredentials (available for
all plugins)
- This setting specifies the maximum amount of concurrent routines that you can use for a given cloud plugin credentials.
- The allowed value range is: 1 (minimum value) - 200.000 (maximum value).
- The default value is 10.
- _<PluginName>AssetDiscoveryPlugin_Discovery_MaxConcurrentRoutinesForScans
(available for VMware and Amazon Web Services plugins)
- This setting specifies the maximum amount of concurrent routines for a given cloud plugin discovery.
- The allowed value range is: 1 (minimum value) - 200.000 (maximum value).
- The default value is 10.
These settings can be specified using the Fixlet under BES Support named <PluginName>multithreading discovery settings.
Remove data for Deleted Devices
This option, available starting from BigFix Version 10.0.8, consists of a setting on the Plugins that can be changed from the WebUI. When the Plugin Portal sends a deletion request to the BigFix Server, and this setting is enabled, the BigFix Server performs a physical deletion. It means that it physically removes the devices and all associated data from the database. If this setting is disabled (it is disabled by default), the BigFix Server performs a logical deletion. It means that the devices are marked as deleted but they are still contained in the BigFix Database.
For details about this feature, see Discovering cloud resources.
Remove Correlated Instances
This option, available starting from BigFix Version 10.0.8, consists of a setting on the Plugins that can be changed from the WebUI. When the Plugin Portal sends a deletion request to the BigFix Server, and this setting is enabled, the BigFix Server deletes also the native instances associated to the Proxied ones, coming from the Plugin Portal deletion request. This setting is disabled by default.
For details about this feature, see Discovering cloud resources.
Logs
Cloud plugins are installed with a standard log level, and the following default log path:
- Windows: C:\Program Files (x86)\BigFix Enterprise\BES Plugin Portal\Plugins\Plugin_name\Logs\log.txt
- Linux: /var/opt/BESPluginPortal/Plugins/Plugin_name/Logs/log.txt
The log file rotates when it reaches the size of 10 MB. The latest 10 rotated logs are available in the log directory.
You can update the log path and verbosity in the Plugin Management section of the BigFix WebUI.
Support of multiple sets of credentials
A cloud plugin might be configured to use multiple sets of credentials. The first set is specified at installation time, further sets can be added at any time from the Plugin Management section of the BigFix WebUI.
At each discovery, the cloud plugin goes through all available credential sets, and retrieves the cloud resources that are available to each set. If a credential set reaches the maximum number of failed discovery attempts, it is no longer taken into account during the next discoveries.
Maximum number of failed discovery attempts
It is the maximum number of consecutive discovery failures for a credential set before it is skipped. Not all kind of discovery failures would increase the counter, only those related to failed login attempts due to incorrect or expired passwords. Successful discovery attempts reset the counter. Restarting the plugin portal would reset the counter as well.
Skipping a failing credential set after three consecutive failures helps reducing the chance of having it affected by possible account lockout policies in place on the cloud platform side.
When a credential set reaches the maximum number of failed attempts, the following message is written in the standard log:
[error] Refresh all: user 'Account Label' reached the maximum attempts (3)
and it will be skippedWhen this happens, the operator should take advantage of the BigFix WebUI to update the password. The updated credential set is taken into account again starting from the next discovery.
Proxy support
The AWS and the Microsoft Azure plugins must be able to access related cloud services using HTTPS over the Internet. In both cases, it is possible to use a proxy to do that, although the supported proxy configuration differs.
How to configure a proxy for AWS plugin
When installing the AWS plugin, you can configure it to run discoveries through a proxy by filling in the appropriate fields of the installation Fixlet or of the Install Cloud Plugin page on the BigFix WebUI. The WebUI also allows you to specify the proxy at a later time by editing the configuration of an installed plugin.
In case of an HTTPS proxy, it is possible to configure the AWS plugin to validate the SSL certificate of the proxy using a custom CA certificate file. A BES Support task allows you to carry out this configuration.
How to configure a proxy for Microsoft Azure plugin
- Windows
- The proxy must be set at system level using the http_proxy and https_proxy environment variables.
- Linux
- The following key/value pairs must be specified in the
/etc/opt/BESPluginPortal/custom.config file (create this file manually if it
does not already exist):
- https_proxy=http://proxyHost:proxyPort/
- http_proxy=http://proxyHost:proxyPort/
On both Windows and Linux, restart the BigFix Plugin Portal service to make the proxy configuration effective.
_Enterprise
Server_ClientRegister_Proxy<attributename>, generally used to set up a proxy
connection on a Relay and with the parent Relay included in the related exception list
setting. For more details, see Server/Relay.