HTTPS across BigFix applications
This topic describes how the SSL/HTTPS communication works in BigFix applications and links the tasks on how to configure it.
By default, BigFix applications provide self-signed certificates (a certificate that is issued by the server itself). Self-signed certificates do not provide means to verify the origin of the certificate through a trusted certificate authority. For this reason they are not intended for production environments.
If you want to reuse a CA signed certificate for a BigFix application, ensure that it follows the key pair requirements of the application:
Key pair requirements of BigFix applications
| BigFix application | Private key format | Recommended key strength value | Container format of certificate and private key | Private key password protected | Wildcard domain support |
|---|---|---|---|---|---|
| Web Reports | RSA | 4096 bits | PEM-encoded | No | No |
| Explorer | RSA | 4096 bits | PEM-encoded | No | No |
| Remote Control | RSA | 4096 bits | PEM-encoded, PKCS12 | Yes | No |
| Rest API | RSA | 4096 bits | PEM-encoded | No | No |
| Inventory | RSA, DSA | 2048 bits | PEM-encoded | No | No |
| WebUI | RSA | 2048 bits | PEM-encoded | No | No |
| Security Compliance Analytics | RSA, DSA | 2048 bits | PEM-encoded | Yes | Yes |
| Server Automation REST API | RSA | 2048 bits | PEM-encoded | No | No |
What SSL is and how it works
HTTPS consists of communication over Hypertext Transfer Protocol (HTTP) within a connection encrypted by Transport Layer Security (TLS) or Secure Sockets Layer (SSL). It is a secure communication channel you can use to exchange information between a client server application, for example a web browser and a web server.
- A public key that is contained in a digital certificate and is used to encrypt the information
- An associated private key that is used to decrypt the information
The digital certificate states that the public key is correctly associated to a server. Therefore the certificate is generally issued by an external Certificate Authority that digitally signs it. BigFix applications provide self-signed certificates (a certificate that is issued by the server itself), and you cannot verify the origin of these certificates through a trusted certificate authority. For this reason they are not intended for production environments.
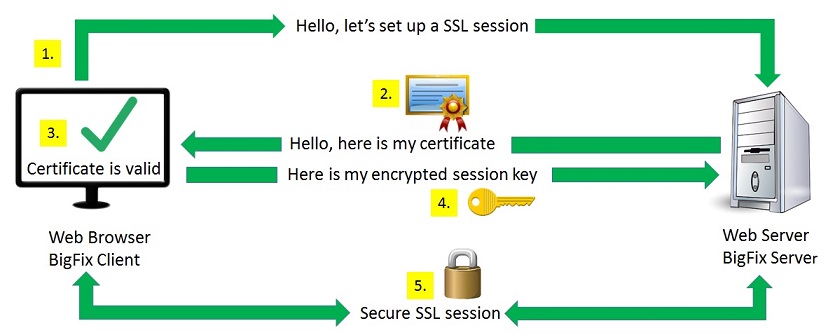
After enabling SSL communication, anyone who connects to your BigFix server receives a certificate that contains your public key. If the client is a web browser, it has a list of trusted certificate authorities and checks that the certificate was issued by one of them. If it is valid, the web browser uses the public key that was contained in the certificate to encrypt a proposed shared key and sends the encrypted key over the web server where it decodes the shared key using its private key. Now both client and server have a copy of the same symmetric key which they use to encrypt all future communications. The following figure summarizes the steps for establishing a secure communication:
Advantages of using SSL
The main advantage of using HTTPS is authentication of the visited website and associated web server and protection of the privacy and integrity of the exchanged data.
The primary reason why SSL is used is to keep sensitive information sent across the Internet encrypted with an SSL certificate so that only the intended recipient can understand it. When an SSL certificate is used, the information becomes unreadable to everyone except for the server you are sending the information to. In this process, the data traverses multiple computers before it reaches the recipient. On the way, the data could be accessed by unauthorized third parties. However, SSL encrypts the original data so that the data is protected from hackers and identity thieves.
By adopting SSL you create trust in your communication over internet. Given the benefits, going through the authorization process necessary to obtain a trusted SSL certificate is worth the effort.