Manage Data Sources
This section describes how to specify the data source and how the data is processed for automation and analysis in an organization.
To create a data source, perform the following steps:
- Log in with Organization Admin user.
- On the main menu bar, click Configuration 🡪 Manage Data Sources.
- On the Manage Data Sources screen, click
 .
.Figure 1. Data Sources 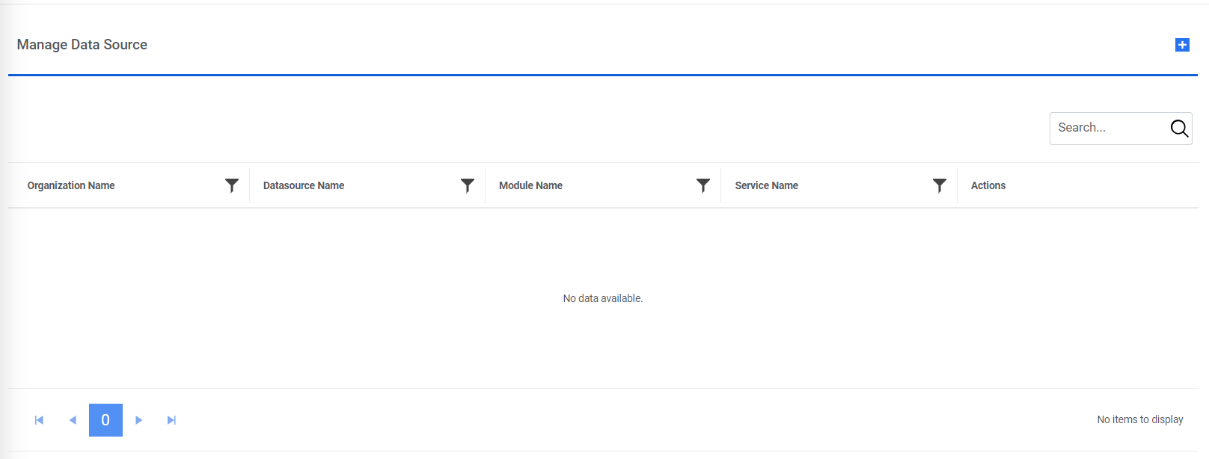
- The Manage Data Source page appears with the following tabs:
- Organization
- Data Source
- Fetch Data Configuration
- Release Rules Configuration
Figure 2. Organization Details 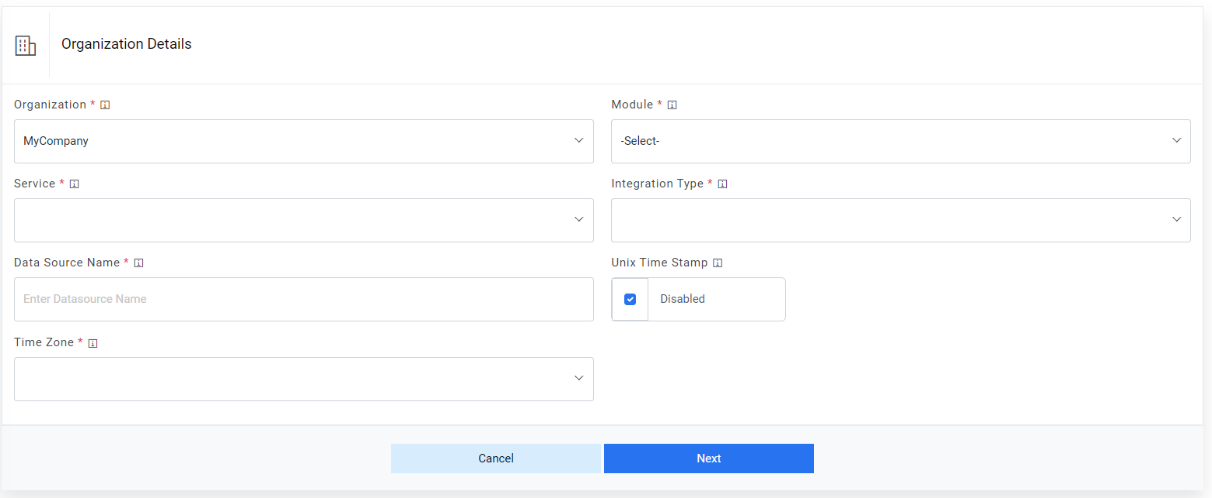 Note:Release Rules Configuration is only applicable for the following Module types- Incident Management, Change Request Task and Service Request Task. This tab will not be activated for other module types.
Note:Release Rules Configuration is only applicable for the following Module types- Incident Management, Change Request Task and Service Request Task. This tab will not be activated for other module types.
Organization
Users can set up an organization, for which the data source will be created, by performing the following steps:
- On the Organization tab, select the organization for which user wants
to create the data source from the Organization
Name field.Note:The organizations listed in the drop-down list are created through Manage Organizations.
- Select a module, where the organization brings the data from the data source in iAutomate, from the Module field.
- Upon selection of the Module, the following two additional input parameters will
be populated. Select the appropriate option
- Closure: Check this option if you want product to manage the ticket closure updates instead of the RBA tool. In this scenario, an additional tab “Close Rules Configuration” will be activated for providing further details, steps for which are mentioned later.
- InProgress: Check this option if you want product to manage the tickets in
progress status updates instead of the RBA tool. In this scenario, an additional tab
“InProgress Rules Configuration” will be activated for providing further
details, steps for which are mentioned later.
Figure 3. Select Organization Details 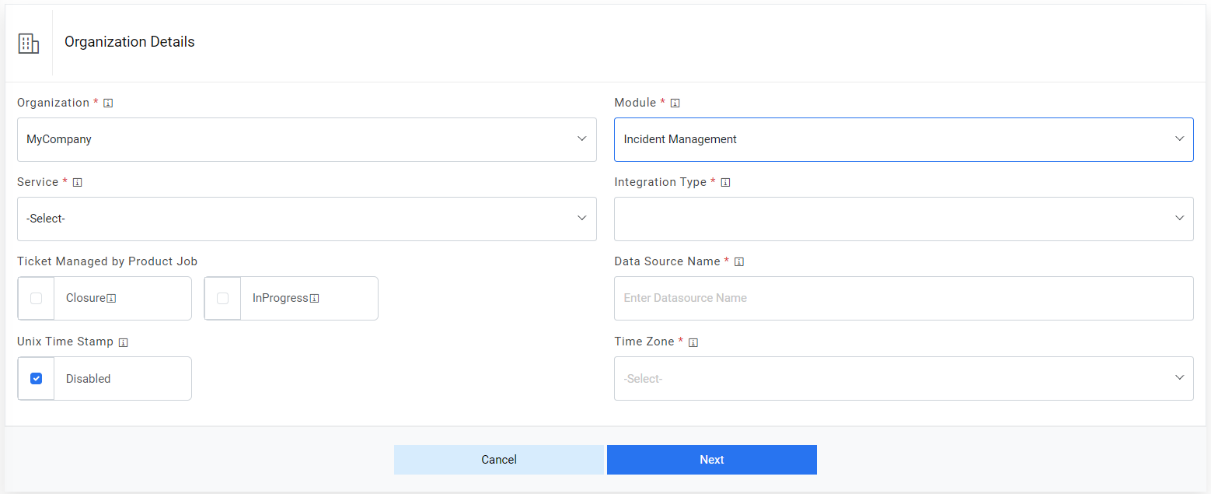
- Select a service, with which iAutomate is integrated and pulls data for automation, from
the Service field.Note:Multiple source types are available.
- Select the integration method to integrate between iAutomate and the selected service type from the Integration Type field.
- Provide the data source name.
- Select the time zone in which ITSM tool API return data.
- Unix Time Stamp: By default, its disabled but if ITSM provides response in different time format such as UNIX then this needs to be unchecked.
- Click Next to update the data source details.
Figure 4. Select Organization Details (cont.) 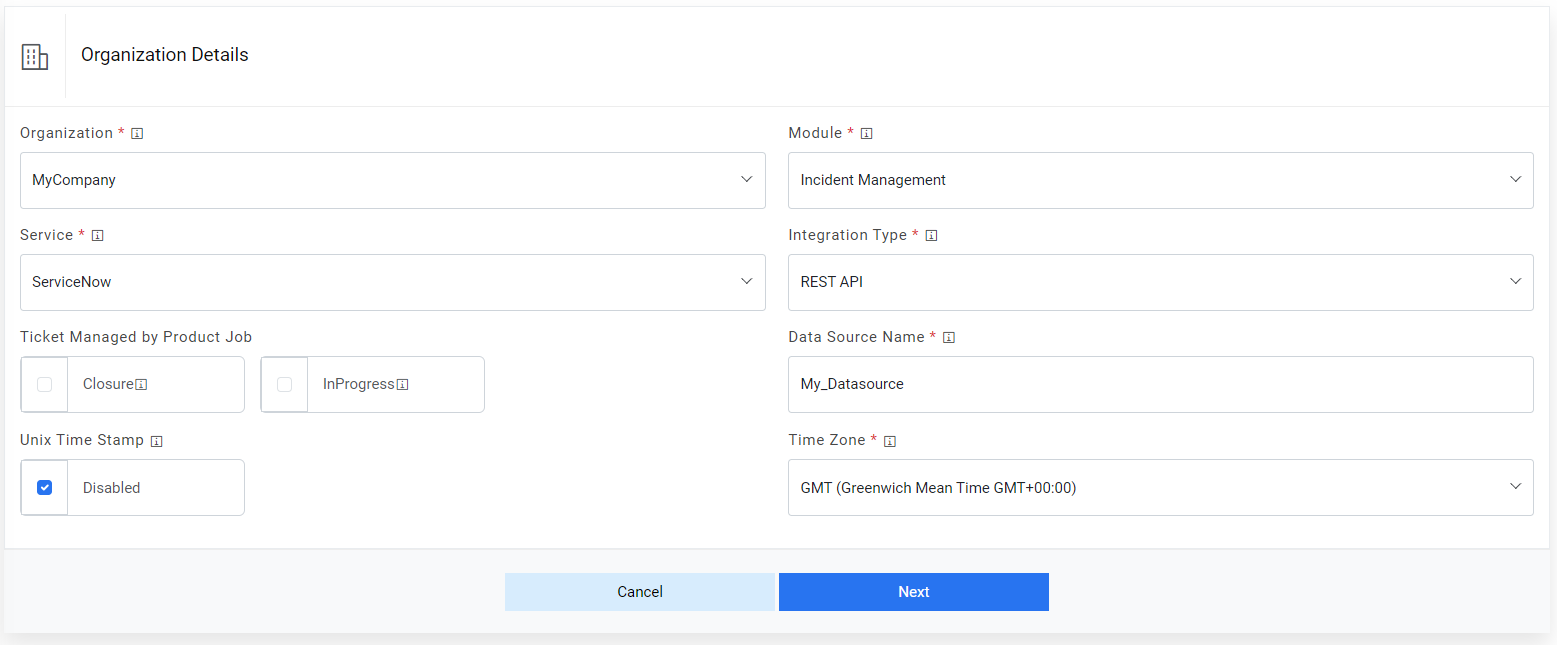 Note:All fields marked with an asterisk (*) are mandatory.
Note:All fields marked with an asterisk (*) are mandatory.
Fetch Data Configuration
Users can configure a method for fetching data from the data source by using the following steps:
- On the Fetch Data Configuration page, type the URL of the selected service type in the URL field to fetch data.
- This URL contains the placeholders that display the parameters based on the applied
clause such as the number of records to be fetched, query type, date on which the data is
fetched, and the order by and so on. It depends on the URL or API provided by the
tool.
Figure 5. Fetch Data Configuration 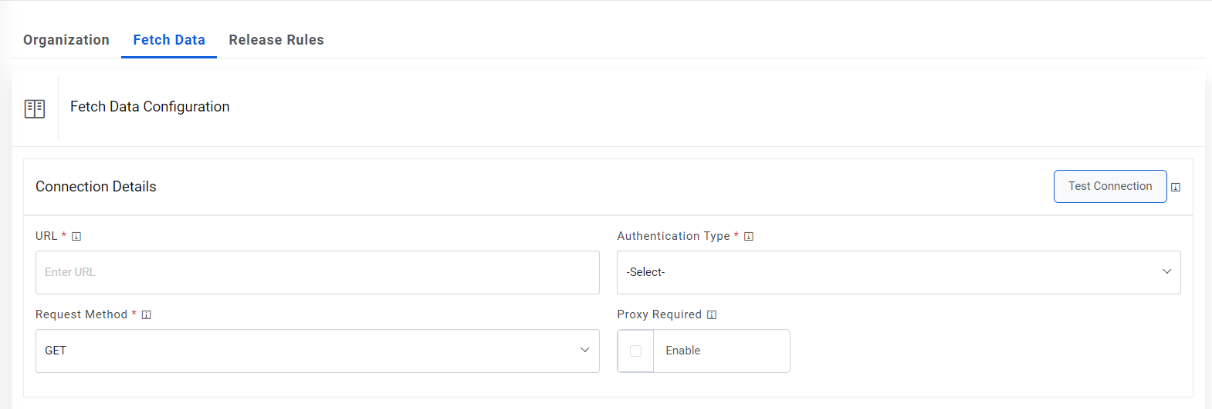 Note:The user can apply multiple clauses into the URL to display only the required parameter into the placeholder. Once you hit the URL, only the placeholders with a hashtag will be displayed with the associated parameters in the URL Path Parameters column. Whenever a user wants to change the data to be filtered, always change the logic in the URL to get the specific parameters.
Note:The user can apply multiple clauses into the URL to display only the required parameter into the placeholder. Once you hit the URL, only the placeholders with a hashtag will be displayed with the associated parameters in the URL Path Parameters column. Whenever a user wants to change the data to be filtered, always change the logic in the URL to get the specific parameters. - Select the Authentication Type. iAutomate supports the following types of
authentications:
- WindowsAuth
- OAuth2
- BasicAuth
- Certificate Based Auth
Figure 6. Authentication Types 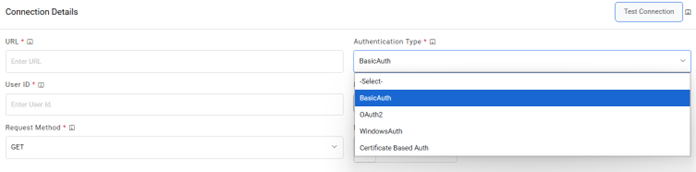
- Selection of Windows / Basic Authentication requires only Username and
Password.
Figure 7. Authentication Type (Windows / Basic) 
- Selection of Certificate based Auth requires CRT file location and Key file location of
the certificate.
Figure 8. Authentication Type (CRT / Key file location) 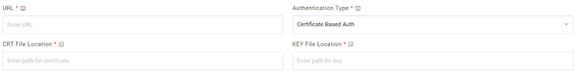
- Selection of OAuth2 authentication type, users needs to provide the below
details:
- Type the Authentication URL.
- Type the Username and Password.
- For password, click on Add Password button next to it. If the password is available in
plaintext, then select Input type as Input Text and enter the password in Value field.
Else if it is available in Azure Key Vault then select Input Type as Azure Key Vault and
then select any of the configured details from the value field. Else if it is available in
any Key Vault such as CyberArk or Secret Manager then select Input Type as CyberArk or
Secret Manager and then select any of the configured details from the value field.
Figure 9. Password in Plaintext .jpg)
Figure 10. Password from Key Vault (CyberArk) .jpg)
Figure 11. Password from Secret Manager .png)
Figure 12. Password from Azure Key Vault .jpg)
Figure 13. Authentication Type (OAuth2) 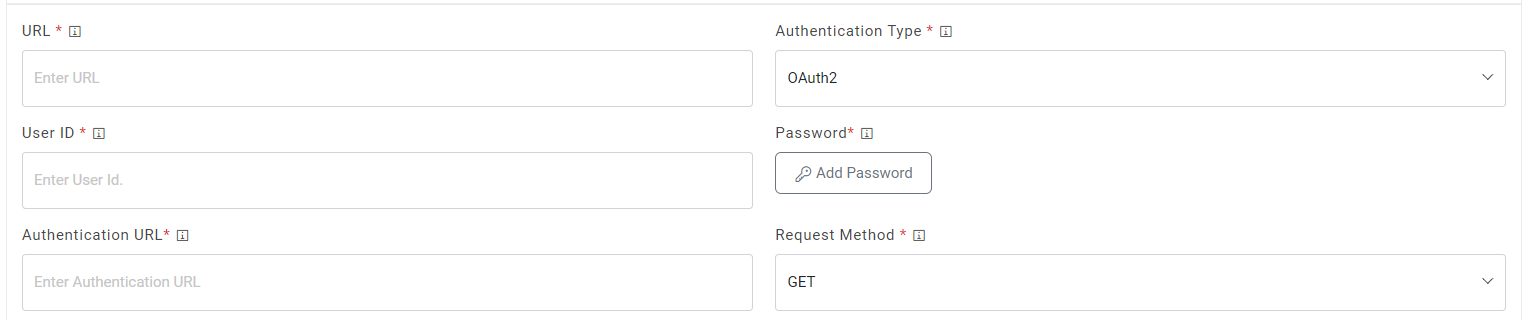
- Select Request Method as GET, PUT, POST or PATCH.
- Select Proxy Required if the environment needs access to content from data sources outside the firewall.
- Click on Test Connection to check accessibility of URL from service. Testing the connection is not mandatory, you can still create Data source.
- To test connection, the URL of ITSM should be whitelisted else it will throw alert stating ‘Use only WhiteListed URL ‘. To whitelist the URL kindly, refer ‘ HCL iAutomate KRS Guide’ .
- If the user has additional parameters, click Add Authentication Parameters under the
Request Authentication Parameters tab.
Figure 14. Add Authentication Parameters 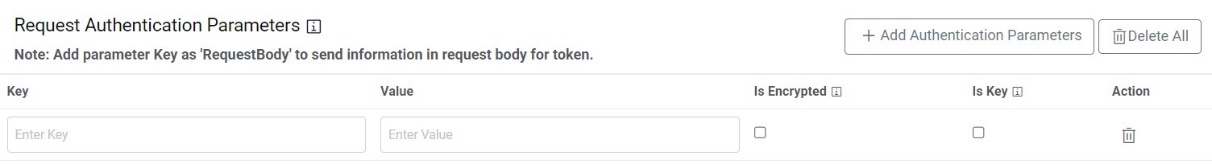
- Type the ‘Request Header Parameter’.
Figure 15. Request Header Parameter 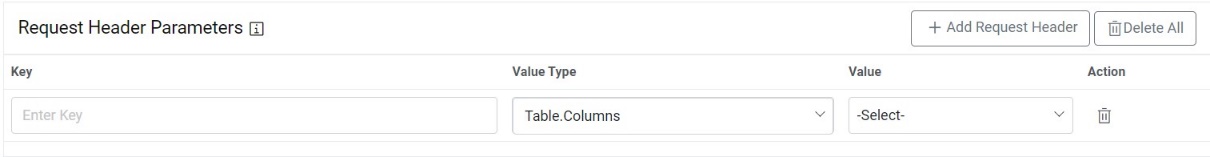
- Type the Request Body in JSON format.
- Type the Response Body in JSON format.
- Click Extract Keys . It adds the parameter and lists to the Mandatory page.
- Click Add the Response Parameter if you want to add a new parameter to the
Mandatory page.
Figure 16. Add response Parameter 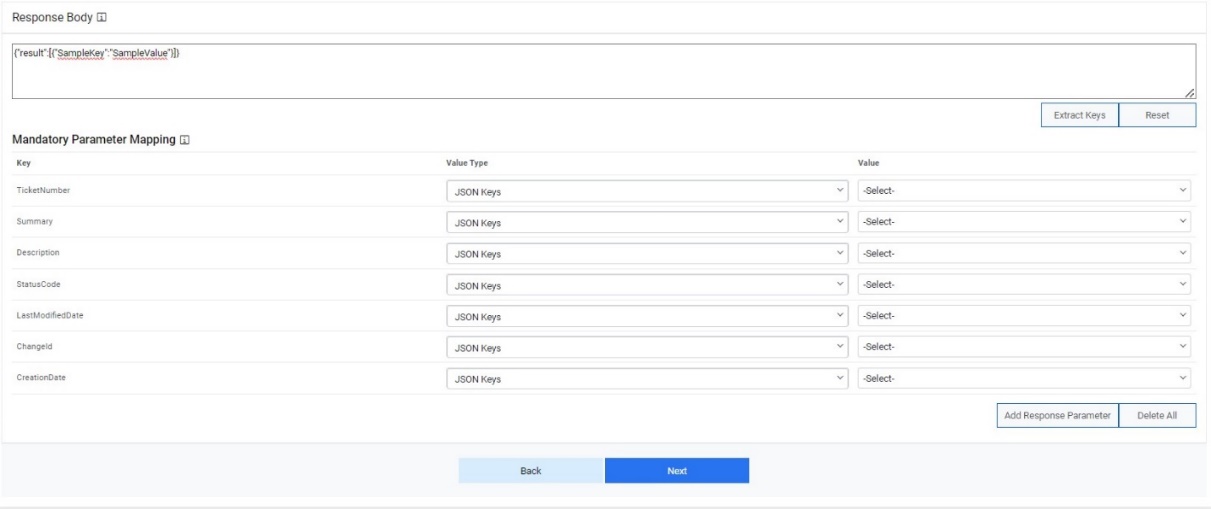
Release Rules Configuration
User can configure a method for releasing the ticket from iAutomate queue by performing the following steps.
- On the Release Rules Configuration page, type the URL of the selected service type in the URL field to release data.
- This URL contains the placeholders that display the
parameters based on the applied clause. It is dependent on the URL or API provided by the
tool.
Figure 17. Release Rule Configuration 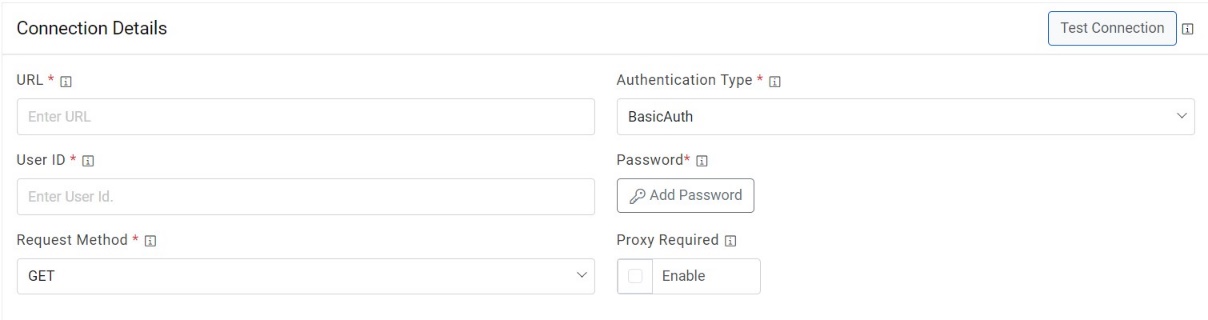 Note:User can apply multiple clauses into the URL to display only the required parameter into the placeholder. Once you hit the URL, only the placeholders with a hashtag will be displayed with the associated parameters in the URL Path Parameters column. Whenever user wants to change the data to be filtered, always change the logic in the URL to get the specific parameters.
Note:User can apply multiple clauses into the URL to display only the required parameter into the placeholder. Once you hit the URL, only the placeholders with a hashtag will be displayed with the associated parameters in the URL Path Parameters column. Whenever user wants to change the data to be filtered, always change the logic in the URL to get the specific parameters. - Select the Authentication Type. iAutomate supports the following types of
authentications:
- WindowsAuth
- OAuth2
- BasicAuth
- Certificate Based Auth
Figure 18. Authentication Types 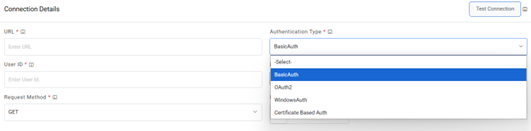
- Selection of Windows / Basic authentication requires only Username and
Password.
Figure 19. Authentication Type (Windows / Basic) .jpeg)
- Selection of Certificate based Auth requires CRT file location and Key file location
of the certificate..
Figure 20. Authentication Type (CRT and Key file location ) 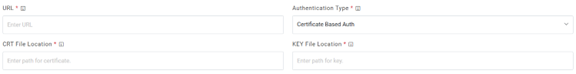
- Selection of OAuth2 authentication type, users needs to provide the below
details.
- Type the Authentication URL.
-
Type the Username and Password.
- For password, click on Add Password button next to it. If the password is available
in plaintext, then select Input type as Input Text and enter the password in
Value field. Else if it is available in Azure Key Vault then select Input
Type as Azure Key Vault and then select any of the configured details from the value
field. Else if it is available in any Key Vault such as CyberArk or Secret Manager
then select Input Type as CyberArk or Secret Manager respectively and then select any
of the configured details from the value field.
Figure 21. Password in Plaintext .jpg)
Figure 22. Password from Key Vault (CyberArk) .jpg)
Figure 23. Password from Secret Manager .png)
Figure 24. Password from Azure Key Vault .jpg)
Figure 25. Authentication Type (OAuth2) 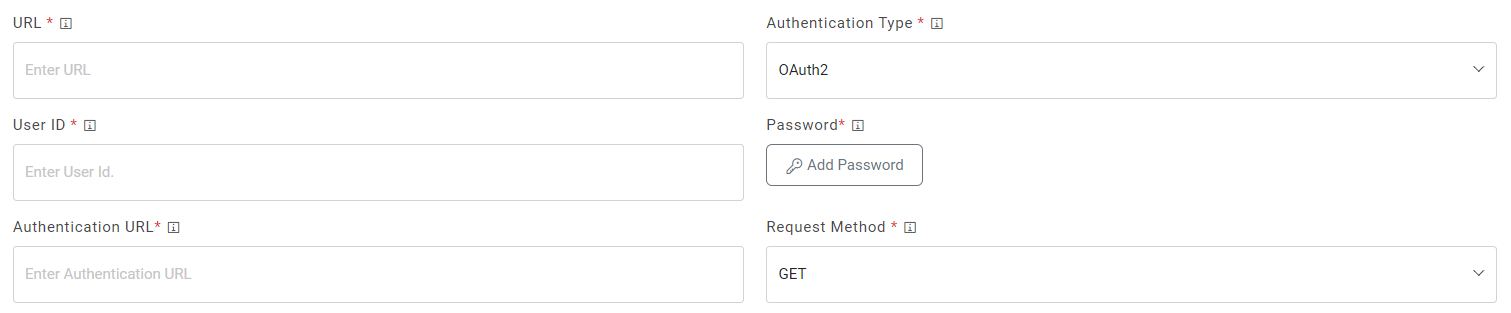
- Select Request Method as GET, PUT, POST or PATCH.
- Select Proxy Required if the environment needs access to content from data sources outside the firewall.
- Click on Test Connection to check accessibility of URL from service. Testing the connection is not mandatory, you can still create Data source.
- To test connection, the URL of ITSM should be whitelisted else it will throw alert stating ‘Use only WhiteListed URL ‘. To whitelist the URL kindly refer ‘ HCL iAutomate KRS Guide’ .
- If the user has additional parameters, click Add Authentication Parameters under the
Request Authentication Parameters tab.
Figure 26. Authentication Type (Windows / Basic) .jpeg)
- Type the Request Header Parameter.
Figure 27. Request Header Parameter .jpeg)
- Type the Request Body in JSON format.
Figure 28. Request Body 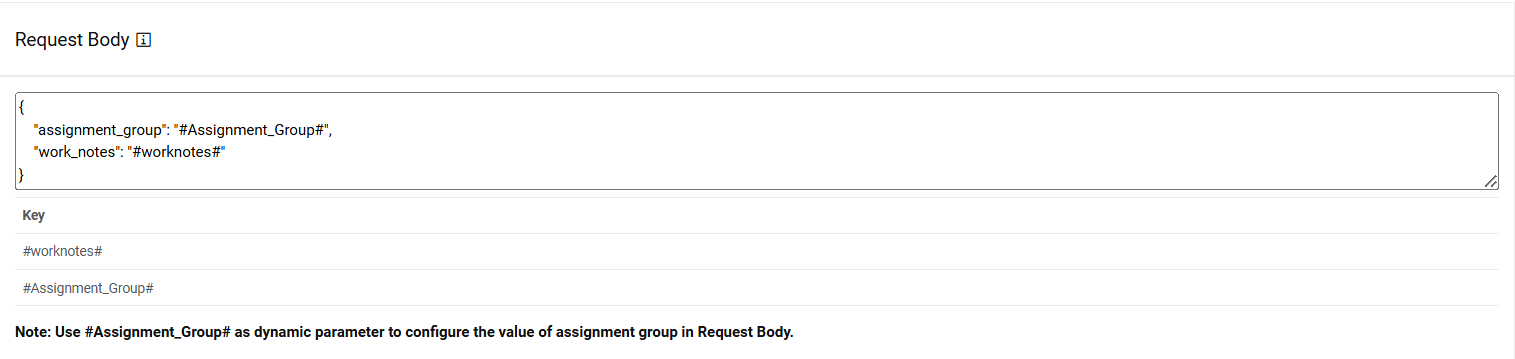 Note:
Note:The values for the parameters will be set in the Mange Rules section.
- Type the Response Body in JSON format.
Figure 29. Response Body 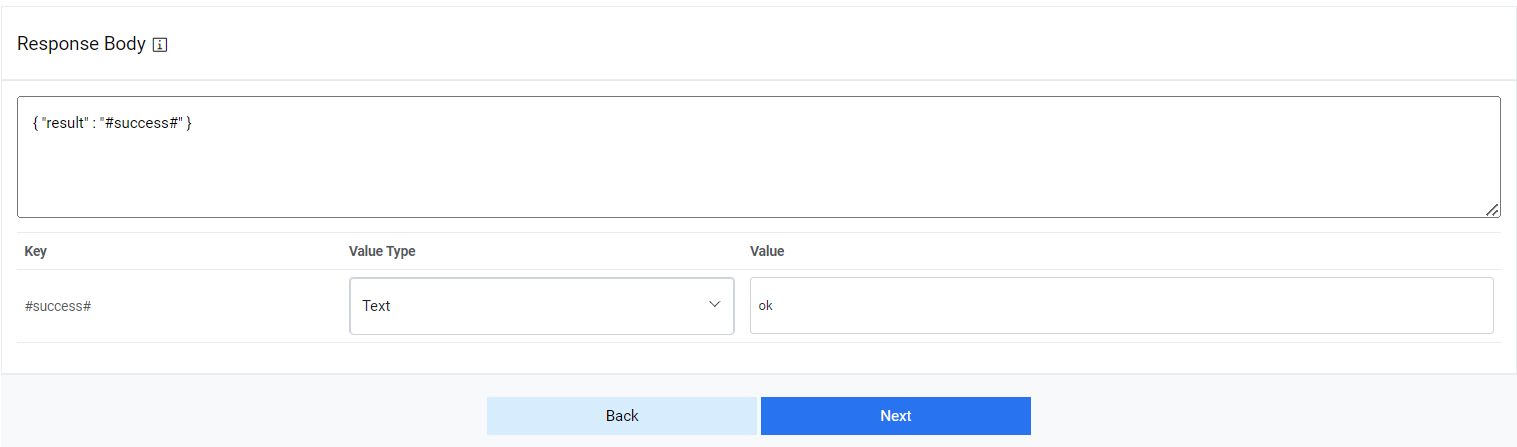
- Click Submit to create the Data Source.Note:All fields marked with an asterisk (*) are mandatory.
Close Rules Configuration
Users can configure the method for Closing the ticket from iAutomate queue by performing the following steps.
- On the Close Rules Configuration page, click on Same as Release if similar configurations as mentioned in “Release Rules Configuration” are required, else proceed ahead.
- Type the URL of the selected service type in the URL field to release data.
- This URL contains the placeholders that display the
parameters based on the applied clause. It depends on the URL or API provided by the
tool.
Figure 30. Close Rules Configuration 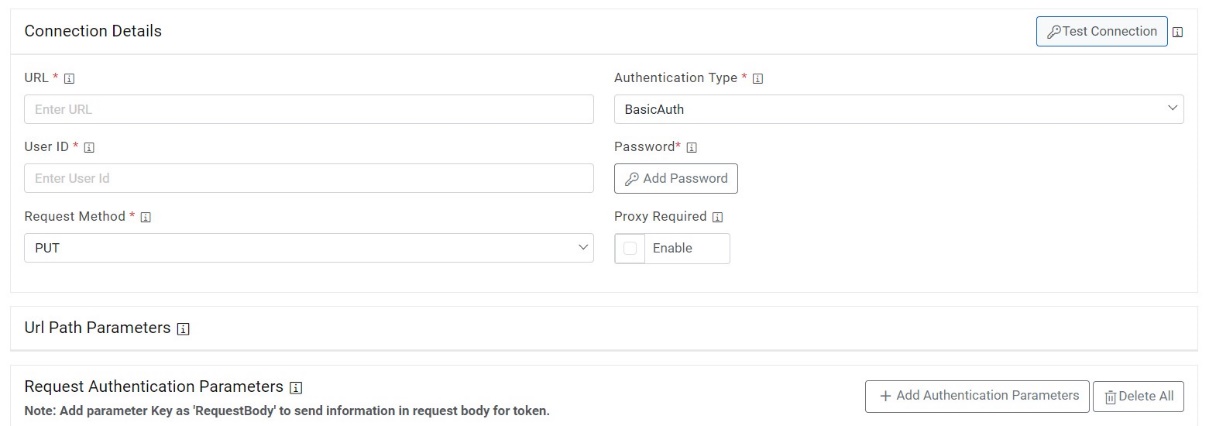 Note:User can apply multiple clauses into the URL to display only the required parameter into the placeholder. Once you hit the URL, only the placeholders with a hashtag will be displayed with the associated parameters in the URL Path Parameters column. Whenever user wants to change the data to be filtered, always change the logic in the URL to get the specific parameters.
Note:User can apply multiple clauses into the URL to display only the required parameter into the placeholder. Once you hit the URL, only the placeholders with a hashtag will be displayed with the associated parameters in the URL Path Parameters column. Whenever user wants to change the data to be filtered, always change the logic in the URL to get the specific parameters. - Select the Authentication Type. iAutomate supports the following types of
authentications:
- WindowsAuth
- OAuth2
- BasicAuth
- Certificate Based Auth
Figure 31. Authentication Types 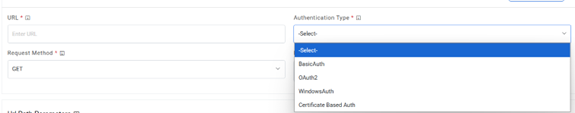
- Selection of Windows / Basic authentication requires only Username and
Password.
Figure 32. Authentication Type (Windows / Basic) 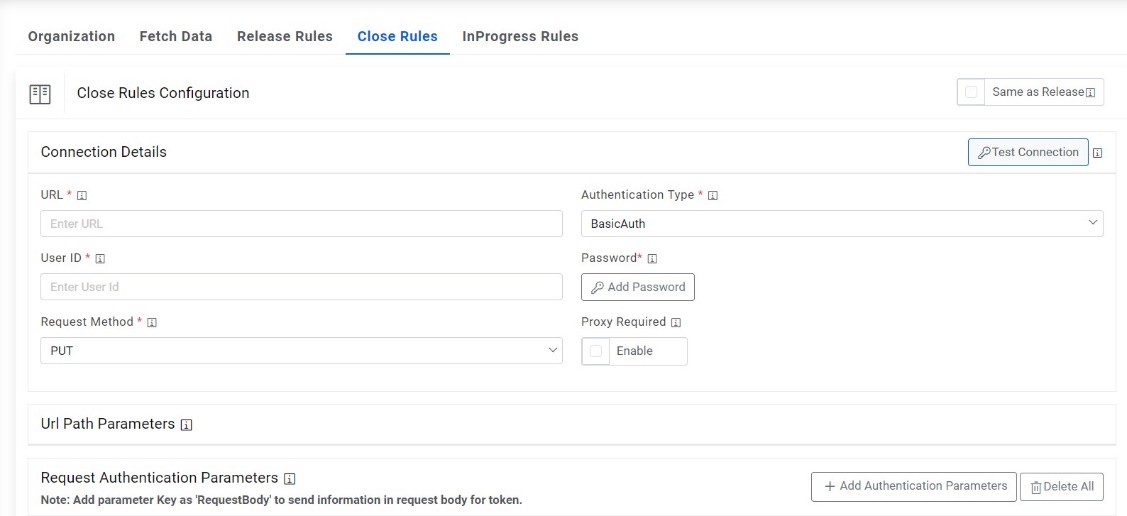
- Selection of Certificate based Auth requires CRT file location and Key file location
of the certificate.
Figure 33. Authentication Type (CRT and Key file location) 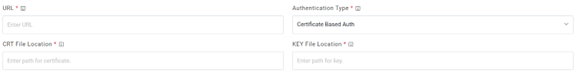
- Selection of OAuth2 authentication type, users needs to provide the below
details.
- Type the Authentication URL.
- Type the Username and Password.
- For password, click on Add Password button next to it. If the password is available
in plaintext, then select Input type as Input Text and enter the password in
Value field. Else if it is available in any Key Vault such as CyberArk or
Secret Manager then select Input Type as CyberArk or Secret Manager respectively and
then select any of the configured details from the Value field.
Figure 34. Password in Plaintext .jpg)
Figure 35. Password from Key Vault (CyberArk) .jpg)
Figure 36. Password from Secret Manager .png)
Figure 37. Password from Azure Key Vault .jpg)
Figure 38. Authentication Type (OAuth 2.0) .png)
- Select Request Method as GET, PUT, POST or PATCH.
- Select Proxy Required if the environment needs access to content from data sources outside the firewall.
- Click on Test Connection to check accessibility of URL from service. Testing the connection is not mandatory, you can still create Data source.
- To test connection, the URL of ITSM should be whitelisted else it will throw alert stating ‘Use only WhiteListed URL ‘. To whitelist the URL kindly refer ‘HCL iAutomate KRS Guide’.
- If a user has additional parameters, click Add Authentication Parameters under the tab
Request Authentication Parameters.
Figure 39. Authentication Type (Windows / Basic) 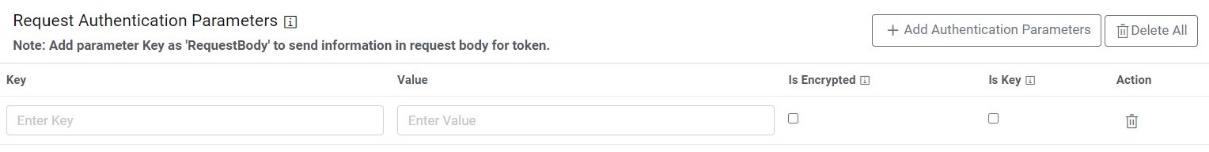
- Type the Request Header Parameter.
Figure 40. Request Header Parameter .jpeg)
- Type the Request Body in JSON format.
Figure 41. Request Body 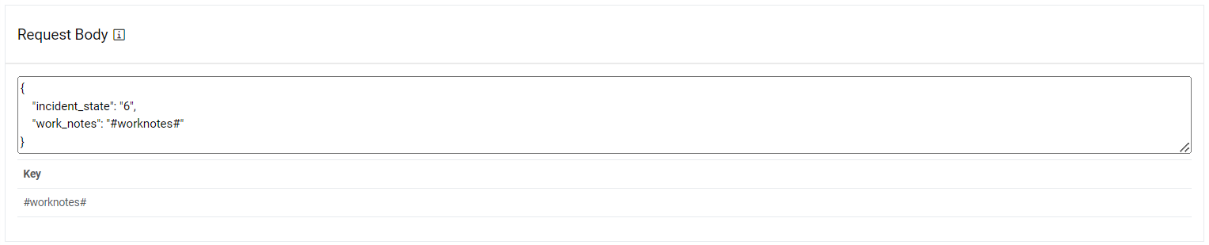 Note:
Note:The values for the parameters will be set in the Mange Rules section.
- Type the Response Body in JSON format.
Figure 42. Response Body 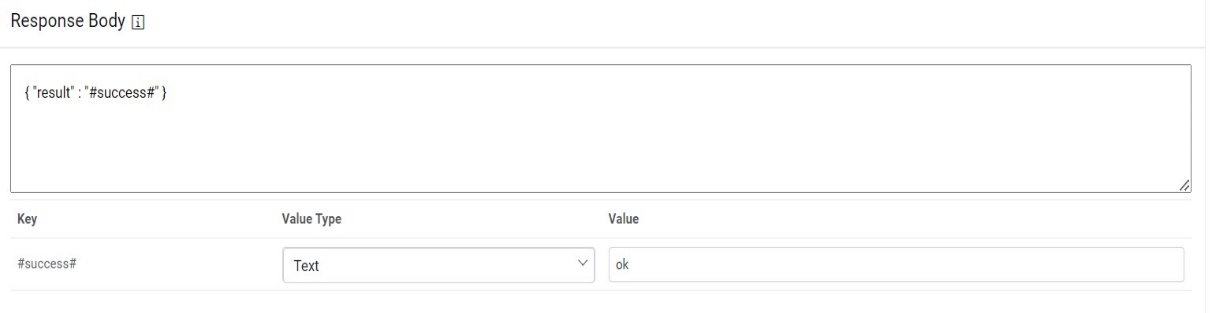
- Click Next to move to the next section.
Figure 43. Request Header Parameter 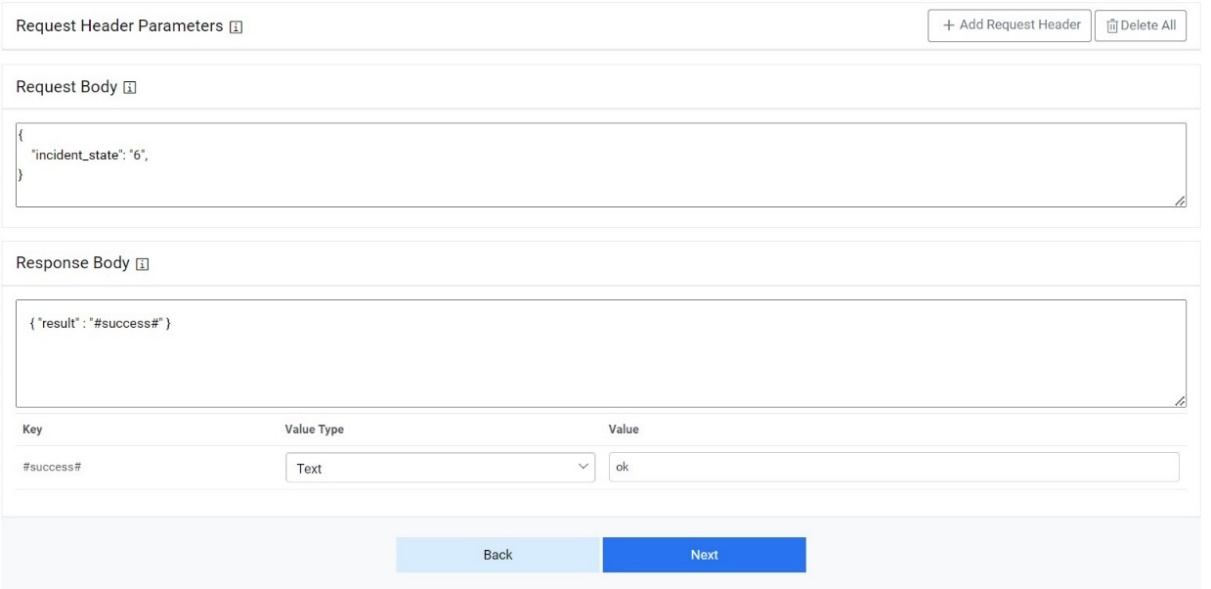
InProgress Rules Configuration
User can configure a method for releasing the ticket from iAutomate queue performing the following steps.
- On the InProgress Rules Configuration page, click on Same as Release if similar configurations as mentioned in “Release Rules Configuration” are required, else proceed ahead.
- Type the URL of the selected service type in the URL field to release data.
- This URL contains the placeholders that display the
parameters based on the applied clause. It is dependent on the URL or API provided by the
tool.
Figure 44. InProgress Rules Configuration 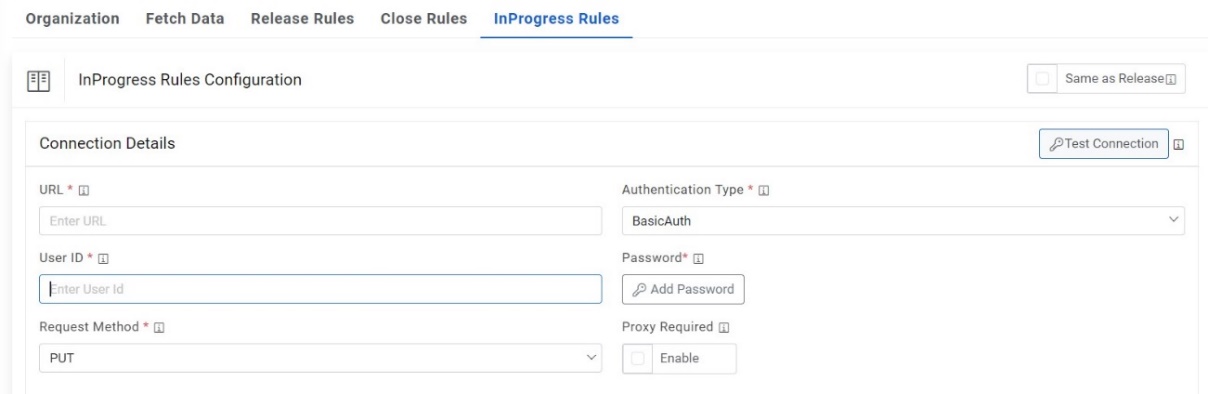 Note:User can apply multiple clauses into the URL to display only the required parameter into the placeholder. Once you hit the URL, only the placeholders with a hashtag will be displayed with the associated parameters in the URL Path Parameters column. Whenever user wants to change the data to be filtered, always change the logic in the URL to get the specific parameters.
Note:User can apply multiple clauses into the URL to display only the required parameter into the placeholder. Once you hit the URL, only the placeholders with a hashtag will be displayed with the associated parameters in the URL Path Parameters column. Whenever user wants to change the data to be filtered, always change the logic in the URL to get the specific parameters. - Select the Authentication Type. iAutomate supports the following types of
authentications:
- WindowsAuth
- OAuth2
- BasicAuth
- Certificate Based Auth
Figure 45. Authentication Types 
- Selection of Certificate based Auth requires CRT file location and Key file location
of the certificate.
Figure 46. Authentication Type (CRT and Key file location) 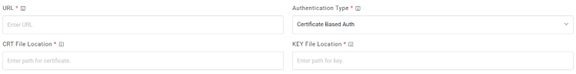
- Selection of OAuth2 authentication type, users need to provide the below
details.
- Type the Authentication URL.
-
Type the Username and Password.
- For password, click on Add Password button next to it. If the password is available in plaintext, then select Input type as Input Text and enter the password in Value field. Else if it is available in Azure Key Vault then select Input Type as Azure Key Vault and then select any of the configured details from the value field. Else if it is available in any Key Vault such as CyberArk then select Input Type as CyberArk and then select any of the configured details from the value field.
Figure 47. Password in Plaintext .jpg)
Figure 48. Password from Key Vault (CyberArk) .jpg)
Figure 49. Password from Secret Manager .png)
Figure 50. Password from Azure Key Vault .jpg)
Figure 51. Authentication Type (OAuth2) 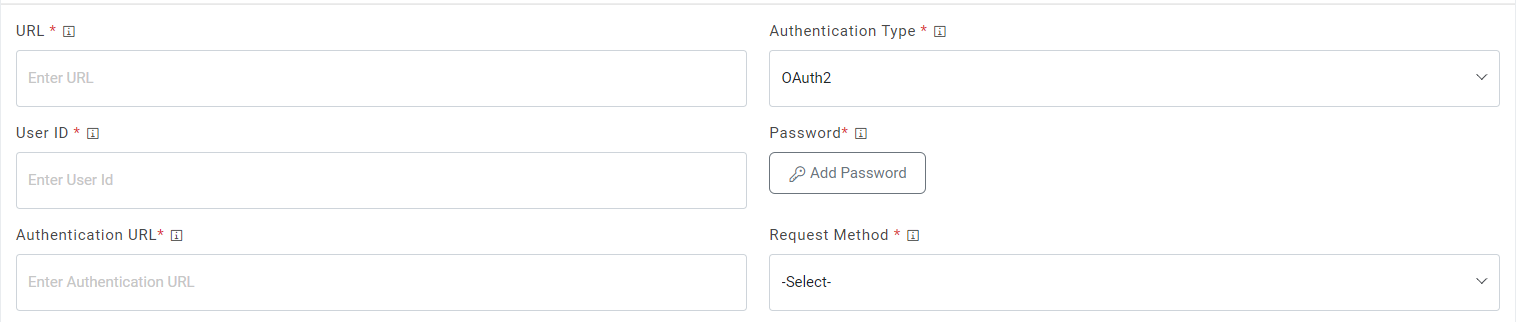
- Select Request Method as GET, PUT, POST or PATCH.
- Select Proxy Required if the environment needs access to content from data sources outside the firewall.
- Click on Test Connection to check accessibility of URL from service. Testing the connection is not mandatory, you can still create Data source.
- To test connection, the URL of ITSM should be whitelisted else it will throw alert stating ‘Use only WhiteListed URL ‘. To whitelist the URL kindly refer ‘HCL iAutomate KRS Guide’.
- If a user has additional parameters, click Add Authentication Parameters under the tab
Request Authentication Parameters.
Figure 52. Authentication Type (Windows / Basic) .jpeg)
- Type the Request Header Parameter.
Figure 53. Request Header Parameter .jpeg)
- Type the Request Body in JSON format.
Figure 54. Request Body 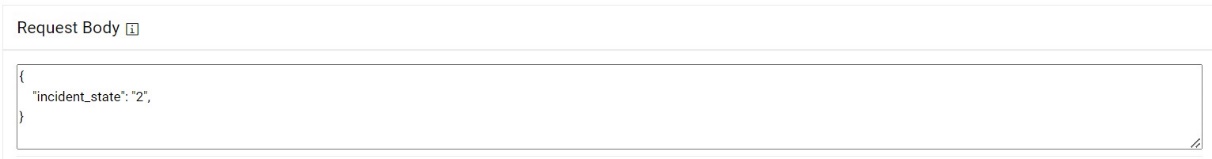 Note:The values for the parameters will be set in the Mange Rules section.
Note:The values for the parameters will be set in the Mange Rules section. - Type the Response Body in JSON format.
Figure 55. Response Body 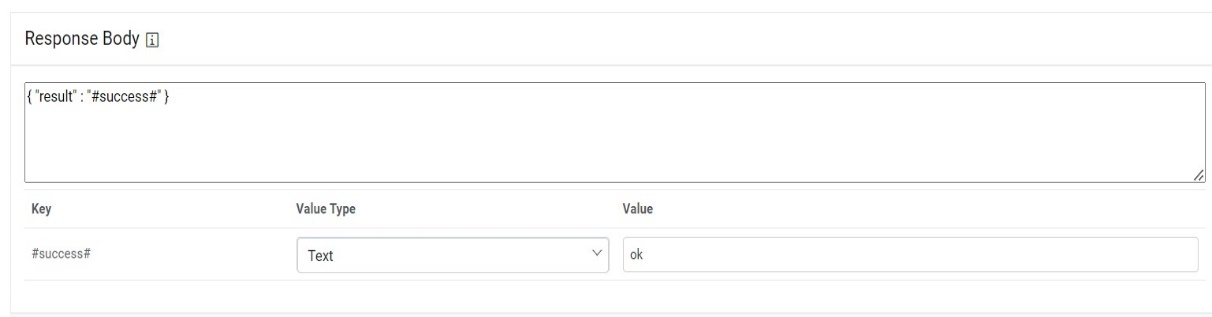
- Click Submit to create the Data Source.
Figure 56. Success Message 
View Data Sources
Users can view and manage the data sources configured within an organization.
To view and manage data sources, perform the following steps:
- On the main menu bar, click Configuration Manage Data Sources.
- The Manage Data Sources page appears.
Figure 57. View Data Source 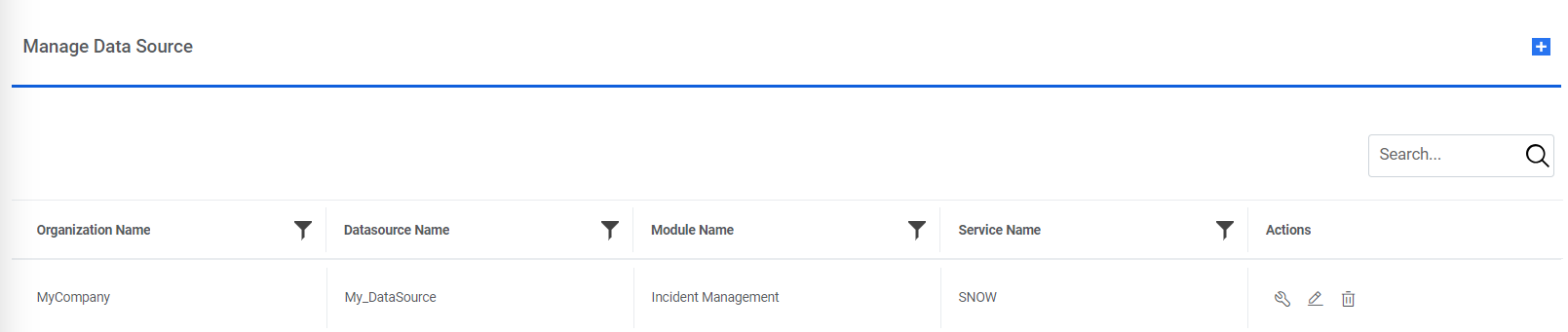
This lists the available data sources in a tabular view with their associated organization, module, and service type. Users can create a new data source by clicking Manage Data Sources. Users can also edit or delete the data source and manage the entry criteria for the data source.
Edit Data Source
Users can open a data source, review the available information, and change the data source details.
To edit the existing data source, perform the following steps:
- On the Manage Data Sources page, click on
 next to the data source user wants to edit.
next to the data source user wants to edit.Figure 58. Edit Data Source .png)
- This redirects you to the Manage Data Sources. Edit the details as required.
- Click Update to commit the changes or click Cancel to discard all changes.
Manage Entry Criteria
Entry criteria are a set of conditions or requirements that must be fulfilled to fetch the data from the data source.
To manage entry criteria, perform the following steps:
- On the Manage Data Sources tab, click
 next to the data source user wants to manage.
next to the data source user wants to manage.Figure 59. Manage Entry Criteria .png)
- The Manage Entry Criteria page appears. You will be prompted to apply the
following conditions:
- Column
- Operator
- Value
- Clause
- Sub-Clause
- Click Save to go to the next screen.
Figure 60. Manage Entry Criteria (Cont.) 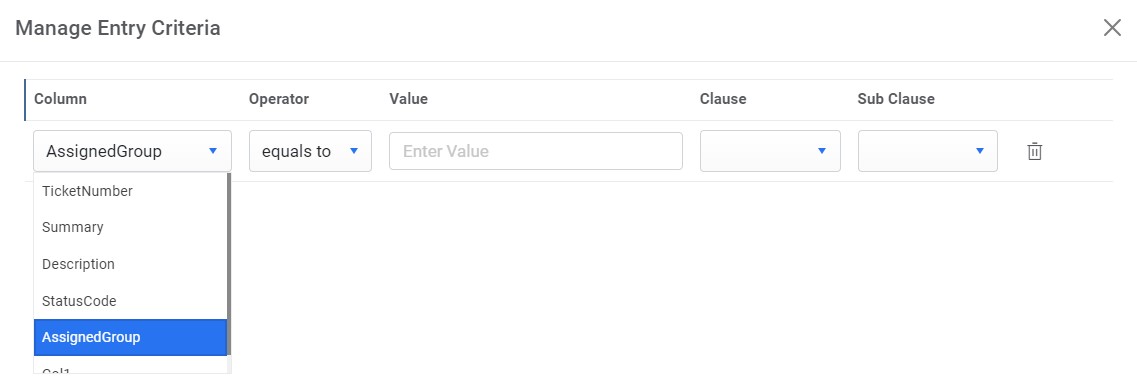
Figure 61. Manage Entry Criteria (Cont.) .jpg)
Figure 62. Manage Entry Criteria (Cont.) 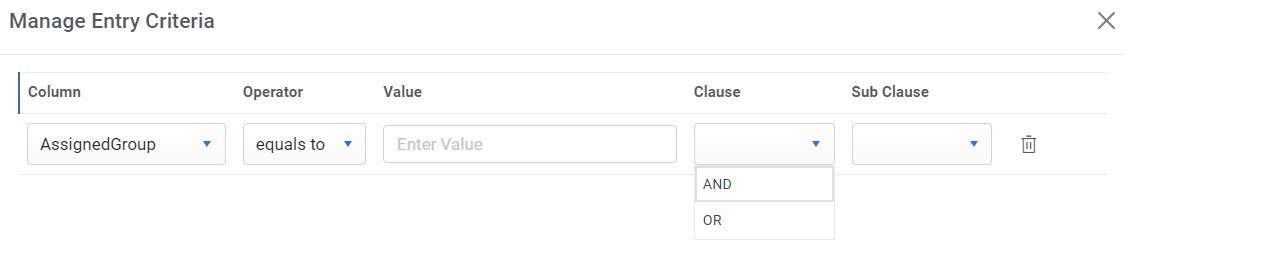
Figure 63. Manage Entry Criteria (Cont.) .jpg)
Delete Data Source
If a data source in an organization is no longer required, the user can delete it by performing the following steps:
- On the Manage
Data Sources tab, click
 to delete the Data
Source.
to delete the Data
Source.Figure 64. Delete Data Source .png)
- Click OK to confirm.
- A confirmation dialog box appears on the screen.