CISA KEV Report
The CISA Known Exploited Vulnerabilities (KEV) Catalog is a curated list maintained by the Cybersecurity and Infrastructure Security Agency (CISA). It includes vulnerabilities actively exploited in the wild and requiring immediate remediation. Organizations can use this intelligence to prioritize patching efforts and reduce exposure to cyber threats.
Key Benefits of CISA KEV
- Identifies vulnerabilities with confirmed exploitation in real-world attacks.
- Provides mandated patching deadlines (for U.S. federal agencies).
- Helps organizations prioritize security patches effectively.
Use Cases
- Security Teams: Helps in vulnerability management by focusing on critical threats.
- Compliance: U.S. federal agencies must comply with KEV patching deadlines.
- Threat Intelligence: Organizations can proactively monitor and defend against known exploited vulnerabilities.
Accessing CISA KEV report
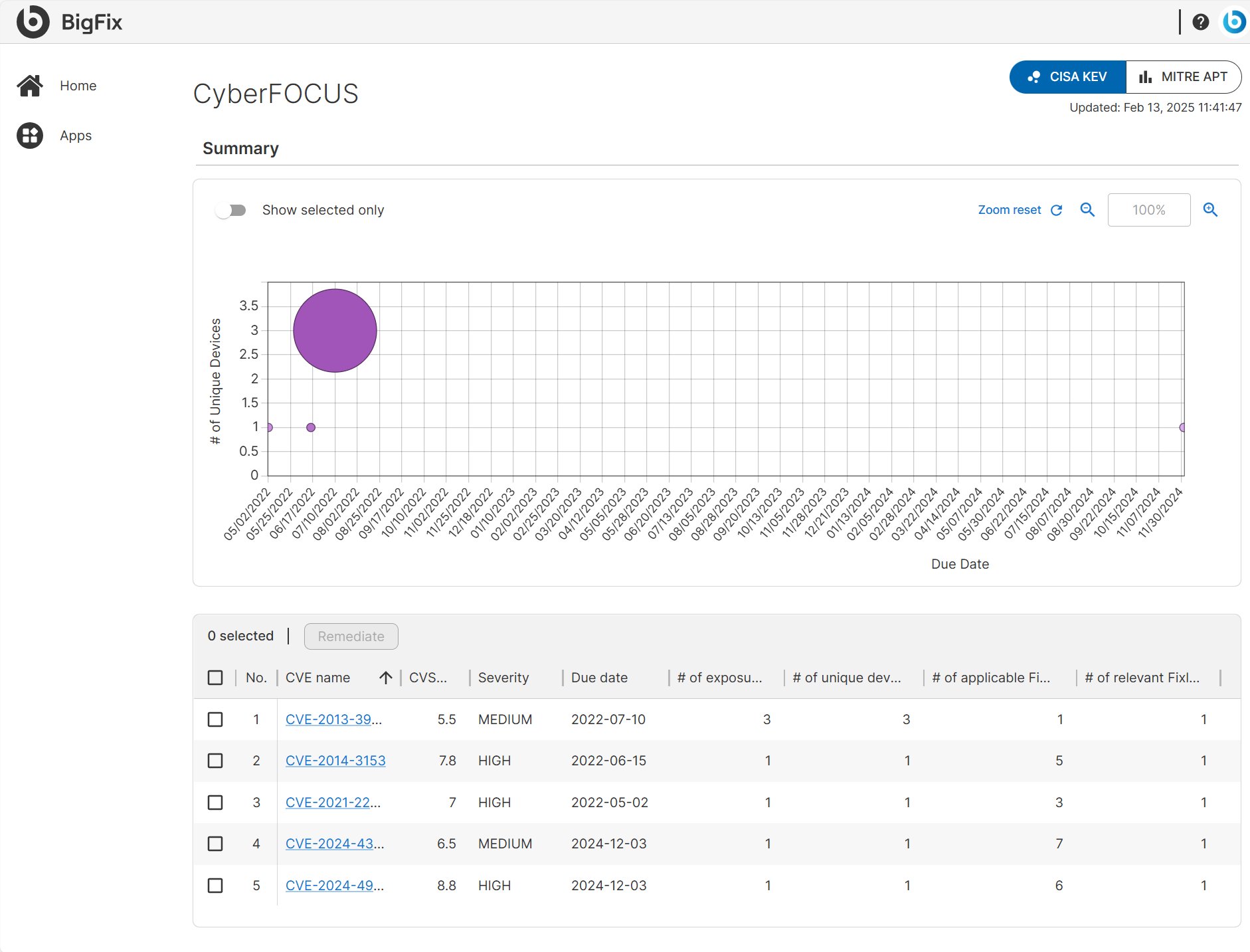
CISA KEV Report Data Representation and Interactions
CyberFOCUS displays CISA KEV data in an interactive table and chart, offering insights into an organization’s exposure to known threats and take actions.
- CISA KEV Chart Representation
-
-
CyberFOCUS uses a bubble chart to visualize CISA KEV data:
-
X-axis: Due date of the CVE.
-
Y-axis: Number of unique affected devices.
-
Bubble Size: Exposure count (larger bubbles indicate higher exposure).
-
Bubble Color: CVSS3 severity (darker color = higher severity).
-
Behavior:
-
Shrinking bubbles indicate that the vulnerabilities are partially remediated.
-
Fully remediated vulnerabilities disappear from the chart.
-
-
-
- CISA KEV Chart Interactions
-
- Hover for Details: Hover over a bubble in the graph to view additional details about the associated CVE and its impact on the applicable environment below the chart.
- Show Selected Only: Filter the chart to display only the CVEs selected from the table.
- Zoom Controls: Zoom in or out to focus on specific data points, with an option to reset the zoom level.
- Detailed CVE Insights: Click on any bubble in the chart to view specific information, such as CVE details, Fixlet details, and other relevant content.
- CISA KEV Table Representation
- The table provides a structured list of vulnerabilities with key details:
- CISA KEV Table Interactions
-
- Click for More Information: Click on a CVE in the table to access in-depth details, including a description, applicable Fixlets, and affected devices. A direct link to the National Vulnerability Database (NVD) is available on the details page for further reference.
- Sort Functionality: Sort vulnerabilities by any column in the table to quickly identify and prioritize threats.
- Start Remediation: Select one or more CVEs from the table and click the Remediate button to initiate the CyberFOCUS remediation flow.
Prescriptive Guidance for CISA KEV Scanner
Prescriptive Guidance on the CyberFOCUS app helps identify and remediate endpoints that are missing the required CISA KEV scanner and/or not actively running the KEV scanner.
- Deploy the scanner to devices that do not have it installed.
- Execute the scanner on applicable devices.
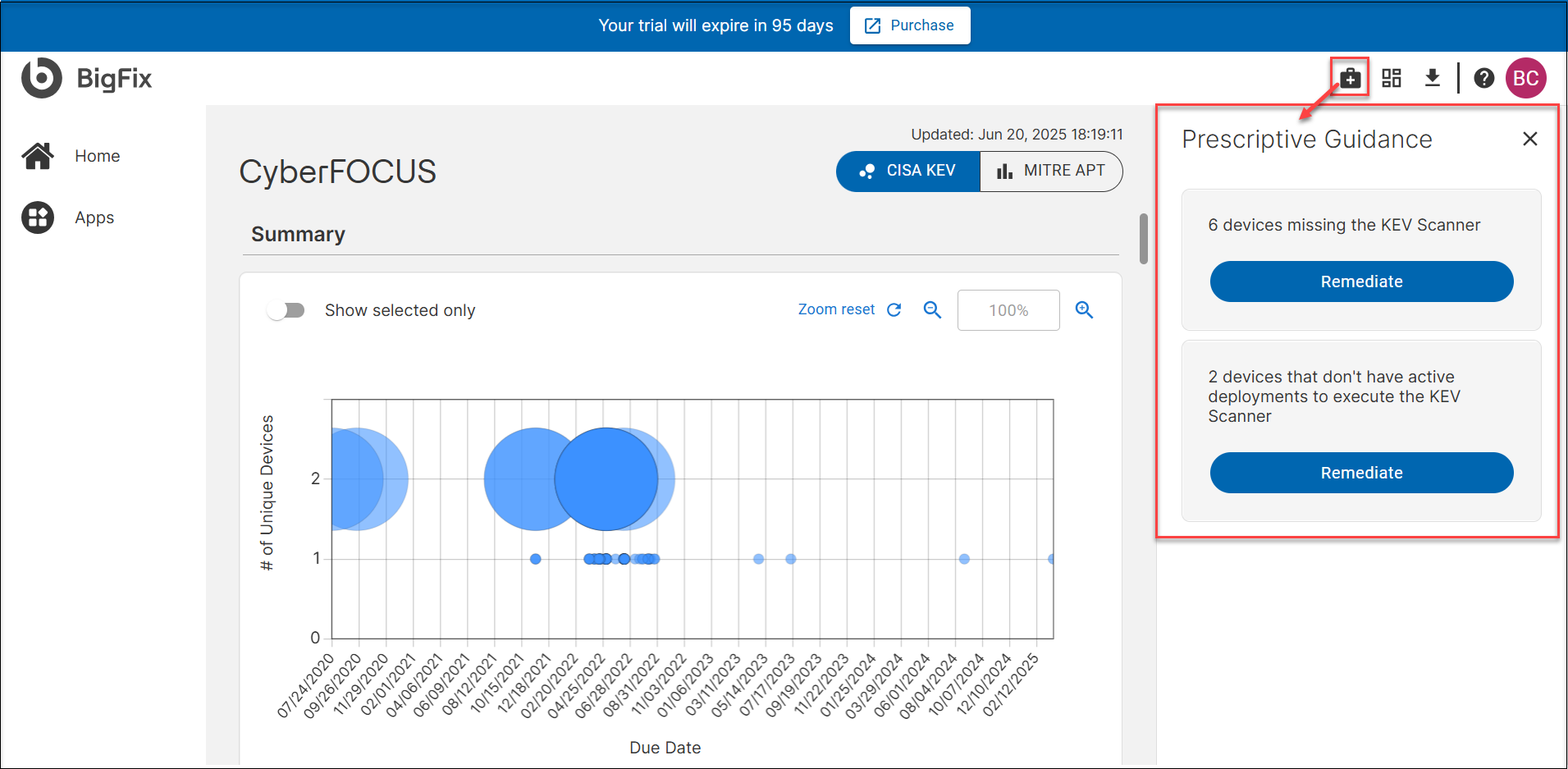
- How the Remediation Flow Works
-
Each remediate action is tied to a specific Site ID and Fixlet ID.
With this, you can easily install and run the KEV scanner across your deployment, ensuring continuous vulnerability assessment and compliance.