Adding Microsoft Entra ID as Identity Provider
You can add Microsoft Entra ID as Identity Provider as follows.
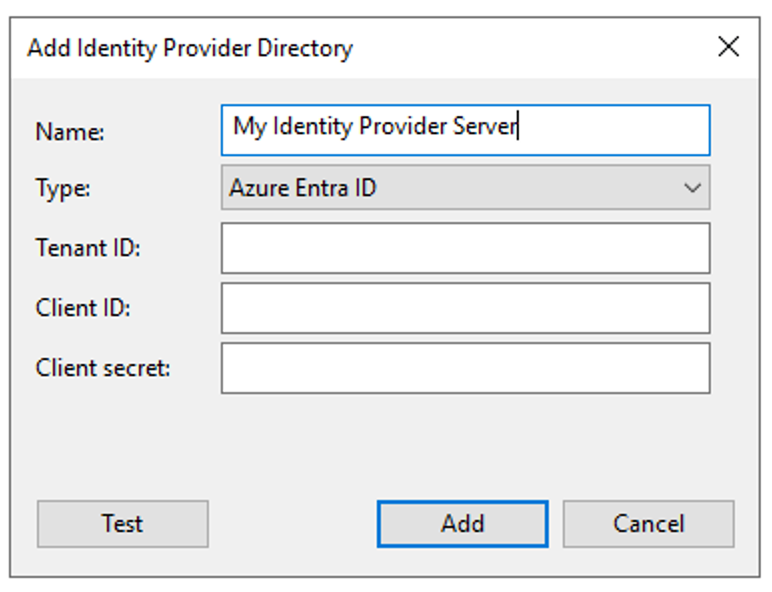
In the new dialog, the following information are required to set up Microsoft Entra ID:
- Tenant ID: A tenant ID is a unique identifier for a Microsoft Entra ID tenant. It is used to identify the tenant when communicating with Microsoft services.
- Client ID: A client ID is a unique identifier for an application that has been registered with Microsoft Entra ID. It is used to identify the application when communicating with Microsoft Entra ID.
- Client secret: A client secret is a secret key that is associated with a client ID. It is used to prove the identity of the application when communicating with Microsoft Entra ID.
The description page with general information about the newly added identity provider now displays the new details, as shown below:
If you want to use a certificate instead of the client secret, select the Use JWT
certificate check box and insert the following information:
- Path: The path to the file containing both the private key and the public
certificate. They must be included in a single file with a
.pemextension. - Password: The password for the private key if it is password-protected. Leave the text field empty if no password is set.
The description page with general information about the newly added identity provider now displays the new details, as shown below:
Note: The certificate path and private key password are not shown in the
general description. Instead, the "New Cert Path" and "New Password" text fields are
displayed to allow you to update the certificate.
After adding the new identity provider from the Console, you can now add Azure users to create BigFix operators. You can then also associate Azure groups to BigFix roles.
Scenario 1: Creating a specific BigFix Operator from an Azure User
Prerequisites to satisfy before running this scenario:
- The application has been registered in Microsoft Entra ID.
- The identity provider has been successfully added to BigFix.
Perform these steps:
- Add the user to the application in the Azure portal. You can either add the user individually or add a group that the user belongs to.
- Create the BigFix operator in the Console as follows:
- Go to the "Operators" dialog.
- Right-click and select "Add Identity Provider Operator".
- Locate and select the user from the previously added tenant.
- Assign the desired permissions to the new operator. The master operator can assign them.
- The new operator account is now ready to be used.
Scenario 2: Creating BigFix Operators from an Azure Group
Prerequisites to satisfy before running this scenario:
- The application has been registered in Microsoft Entra ID.
- The identity provider has been successfully added to BigFix.
Perform these steps:
- Add the group to the application in the Azure portal.
- Assign the identity provider group to a BigFix role as follows:
- Go to the "Role" dialog.
- Create or select a role for which you want to assign permissions to the Azure group.
- Click the "Identity Provider Groups" section within the role configuration.
- Select the Azure group you added in step 1 from the available list.
- Save the changes to the role configuration.
Note:
- Initially, no operator account is created.
- When an Azure user from the added group logs in for the first time, a BigFix operator account associated with that user will be automatically created. This account will inherit the permissions assigned to the role in step 2.