Migrating Keystores
Follow these steps to migrate keystores in BigFix Compliance Analytics. A keystore is a database file that stores security certificates, such as authorization or public key certificates.
About this task
The BigFix Compliance Analytics installer will save the following files for your reference under
<BFC_ROOT>\wlp\usr\servers \server1\resources\security\.
- Under <BFC_ROOT>\wlp\usr\servers \server1\resources\security\, a copy of your original keystore file
- Under <BFC_ROOT>\wlp\usr\servers \server1\config\
- A copy of your original jetty.xml file
- The keystore password in deobfuscated_password file
Migrating keystores require the following:
- Java Runtime Environment (installed in <BFC_ROOT>\jre\bin\
- The original keystore file
- The deobfuscated_password file
- Command prompt (Windows) with appropriate PATH set
Procedure
- Convert the keystore from JKS to PKCS12 format.
Table 1. Example command line of converting the keystore format from JKS to PKCS12 Command line example Reference 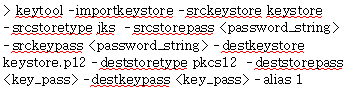
- Input file:
keystore - Output file:
keystore.p12 - <password_string>: The password string saved in the deobfuscated_password file
key_pass: The new password of your choice forkeystore.p12. The password must be a minimum of 6 characters.
- Input file:
- Convert the PKCS12 format keystore into PEM format certificate
and key using OpenSSL.
Table 2. Example command line of converting the keystore format from PKCS12 to PEM Command line example Reference > openssl pkcs12 -in keystore.p12 -out keystore.pem- Input file:
keystore.p12 - Output file:
keystore.pem
You will be prompted to enter the following passwords:
- Password (Import password) for
keystore.p12 - New password of your choice for the private key. The password must be a minimum of 4 characters.
- Input file:
- Open the PEM encoded certificate and key (keystore.pem).
Save it as certificate and a private key file.
- Go to . Apply the following in BigFix Compliance Analytics.
- certificate (server.crt)
- key pair (server.key)
- password (PEM pass phrase entered in Step 2.)