Dynamic custom claims and limiting access to OAuth clients
With Domino as OIDC provider, you can configure any number of custom claims that can use @functions to dynamically build claim values. Additionally, the Domino provider can perform access checking and deny unauthorized users the ability to even acquire an authorization grant for their application.
Dynamic custom claims
You configure dynamic custom claims in the Custom Claims field in the Registered OAuth Client document in idpcat.nsf.
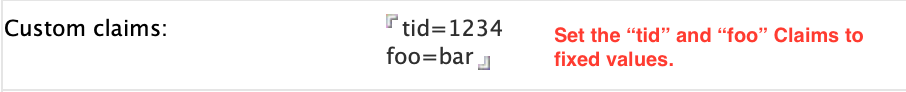
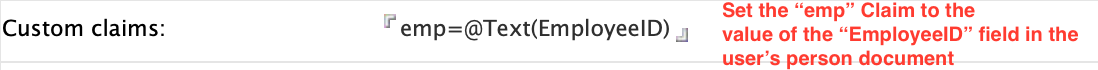
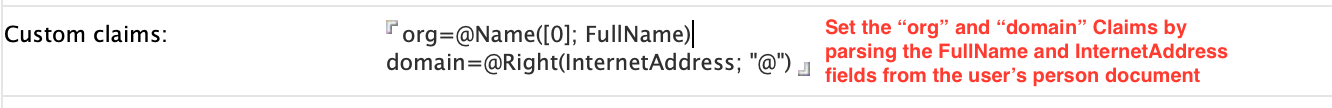
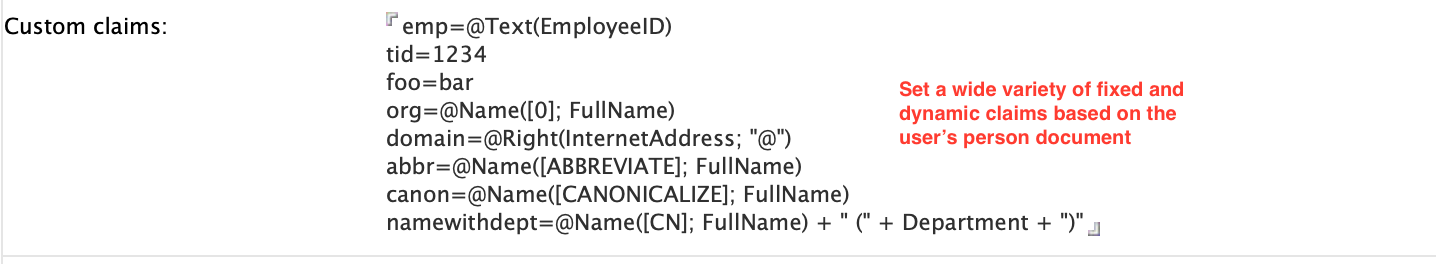
- Individual claims may not include the tilde '~' character.
- The HTTPPassword may not be used in custom claims.
- Excessively long custom claims may be truncated.
Limiting access to registered OAuth clients
Most Domino environments perform access controls at the resource being accessed through ACLs, reader and author fields, and so on. However, some third-party applications prefer to have their OIDC provider perform access checking and deny unauthorized users the ability to even acquire an authorization grant for their application.
To support this scenario, Domino has an "Allowed user group" field in the Advanced section of Registered OAuth Client documents in idpcat.nsf. By default, this field is blank and all authenticated users are allowed to acquire authorization grants for this client.
To limit access, add the name of a group containing the users who are allowed to use this client into the Allowed user group field on the primary Domino OIDC provider server, and save the document. The primary Domino server immediately processes this change and replicates it out to the secondary OIDC provider servers, with no restarts or manual replication required.