Configure a unique password to the cryptographic keystore, and encrypt it with the AES
encryption algorithm.
About this task
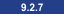 Starting from application update 9.2.7, for all
fresh installations of BigFix Inventory, keystore and database
passwords use AES as a default encryption method. The password encryption schema remains unchanged
for all the application instances upgraded to version 9.2.7.
Starting from application update 9.2.7, for all
fresh installations of BigFix Inventory, keystore and database
passwords use AES as a default encryption method. The password encryption schema remains unchanged
for all the application instances upgraded to version 9.2.7.
To configure SSO keystore passwords and encryption, see: Configuring SSO keystore passwords and encryption.
Procedure
-
Stop the BigFix Inventory server.
- Optional:
If you want to change the keystore password into a custom password, follow the instructions
below. If you only want to change password encryption method from XOR to AES, continue with step
3.
-
To list the contents of the application keystore, run the following command.
Installation_directory/jre/jre/bin/keytool
-list -keystore
<inst_dir>/wlp/usr/servers/server1/resources/security/<keystore_name>
-storetype <type>

Installation_directory\jre\jre\bin\keytool.exe
-list -keystore
<inst_dir>\wlp\usr\servers\server1\resources\security\<keystore_name>
-storetype <type>
When prompted, provide the keystore password. For the default keystore password contact the HCL
Support.
Enter keystore password:
Keystore type: <type>
Keystore provider: IBMJCE
Your keystore contains 1 entry
default, Nov 15, 2013, keyEntry,
Certificate fingerprint (SHA1):
xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx
Note: The list can consist of more than one entry, if Single Sign On is configured for the product.
The underlined element is an alias for the listed entry, and it is required to complete next
steps.
-
Ensure that you change the password for all the listed entries. Run the following command, and
specify the alias at the end of the command line.

Installation_directory/jre/jre/bin/keytool
-keypasswd -keystore
<inst_dir>/wlp/usr/servers/server1/resources/security/<keystore_name>
-storetype <type> -alias default

Installation_directory\jre\jre\bin\keytool.exe
-keypasswd -keystore
<inst_dir>\wlp\usr\servers\server1\resources\security\<keystore_name>
-storetype <type> -alias default
Set up a single password for all the listed entries. For more than one entry, ensure the
passwords are
identical.
Enter keystore password:
Enter key password for <default>:
New key password for <default>:
Re-enter new key password for <default>:
Password change successful for alias <default>
-
To change the keystore password, run the following command.

Installation_directory/jre/jre/bin/keytool
-storepasswd -keystore
<inst_dir>/wlp/usr/servers/server1/resources/security/<keystore_name>
-storetype <type>

Installation_directory\jre\jre\bin\keytool.exe
-storepasswd -keystore
<inst_dir>\wlp\usr\servers\server1\resources\security\<keystore_name>
-storetype <type>
Set up the new keystore password. The password must match the password that you set up for the
listed entries (step
b).
Enter keystore password:
New keystore password:
Re-enter new keystore password:
-
To encrypt your keystore password with AES, run the following command.
-
Set the
JAVA_HOME variable.
 export
JAVA_HOME=Installation_directory/jre/jre
export
JAVA_HOME=Installation_directory/jre/jre
 set
JAVA_HOME=Installation_directory\jre\jre
set
JAVA_HOME=Installation_directory\jre\jre
-
Run the following command

Installation_directory/wlp/bin/securityUtility
encode --encoding=aes

Installation_directory\wlp\bin\securityUtility.bat
encode --encoding=aes
Provide your current keystore password.
Enter text:
Re-enter text:
{aes}xxxxXXXXxxxxXXXXxxxxXXXXxxxxXXXXxxxxXXXX
-
Update the keystore password in the server.xml file. Enter the value
generated in step 3 in the following code line:
<keyStore id='defaultKeyStore' location='<keystore_name>'
password='{aes}xxxxXXXXxxxxXXXXxxxxXXXXxxxxXXXXxxxxXXXX' type='<type>'/>
The
server.xml file is located in the following folder.
 Installation_directory/wlp/usr/servers/server1/server.xml
Installation_directory/wlp/usr/servers/server1/server.xml Installation_directory\wlp\usr\servers\server1\server.xml
Installation_directory\wlp\usr\servers\server1\server.xml
-
Start the BigFix Inventory server.
Note: The
<type> and
<keystore_name> parameters that apply to the
above commands specifies the following:
<type>- Starting from version 10.0.8.0, the type of the certificate is
PKCS12. For earlier versions, it is
JCEKS.
<keystore_name>- Starting from version 10.0.8.0, the name of the keystore file is
key_server.p12. For earlier versions,
it is key_server.jceks.
![]() Starting from application update 9.2.7, for all
fresh installations of BigFix Inventory, keystore and database
passwords use AES as a default encryption method. The password encryption schema remains unchanged
for all the application instances upgraded to version 9.2.7.
Starting from application update 9.2.7, for all
fresh installations of BigFix Inventory, keystore and database
passwords use AES as a default encryption method. The password encryption schema remains unchanged
for all the application instances upgraded to version 9.2.7. Installation_directory/wlp/usr/servers/server1/server.xml
Installation_directory/wlp/usr/servers/server1/server.xml Installation_directory\wlp\usr\servers\server1\server.xml
Installation_directory\wlp\usr\servers\server1\server.xml