Step 2: Configuring single sign-on settings in BigFix Inventory
Configure single sign-on support in BigFix Inventory. At the point, BigFix Inventory Server has activated the SAML endpoint but the endpoint is not protected with single sign-on. After performing the steps mentioned below, you will be able to check the URLs that is used by BigFix Inventory Server through the SAML metadata.
Before you begin
- Gather the necessary information
- Before you start the configuration, collect the following information:
- URL to the login page of the Identity Provider. It is the URL to which an
unauthenticated request is redirected. After the request is authenticated by the
Identity Provider, the user is redirected to BigFix Inventory. For example:
- ADFS: https://<ADFS_hostname>/adfs/ls/IdPInitiatedSignOn.aspx?LoginToRP=https://BFI_host_name:9081/ibm/saml20/defaultSP
- ENTRA ID: https://launcher.myapps.microsoft.com/api/signin/<APPICATION ID / GUID>?tenantId=<TENANT ID / GUID>
- URL of the Trusted Issuer. It is the URL to the certificate issuer of the Identity
Provider that is needed to establish a trust relationship.For example:
- ADFS: http://ADFS_host_name/adfs/services/trust
- ENTRA ID: https://sts.windows.net/<TENANT ID / GUID>/
- Public certificate of the Identity Provider in the key_name.cer format.
- URL to the login page of the Identity Provider. It is the URL to which an
unauthenticated request is redirected. After the request is authenticated by the
Identity Provider, the user is redirected to BigFix Inventory.
- Enable SSL
- Ensure that SSL is enabled in BigFix Inventory and in the Identity Provider.
- Backup files
- Before you start configuring single sign-on, back up the following files:
- server.xml
 bfi_install_dir/wlp/usr/servers/server1
bfi_install_dir/wlp/usr/servers/server1 bfi_install_dir\wlp\usr\servers\server1
bfi_install_dir\wlp\usr\servers\server1
- web.xml
 bfi_install_dir/wlp/usr/servers/server1/apps/tema.war/WEB-INF
bfi_install_dir/wlp/usr/servers/server1/apps/tema.war/WEB-INF bfi_install_dir\wlp\usr\servers\server1\apps\tema.war\WEB-INF
bfi_install_dir\wlp\usr\servers\server1\apps\tema.war\WEB-INF
- server.xml
- Create users
- Create BigFix Inventory users implement the single sign-on mechanism. During the user
creation, select Single Sign-on as the authentication method.
Ensure that all user names are fully-qualified names that contain the full domain name,
for example: user@domain.example. Also, ensure that at least one user is an
administrator.
 If the BigFix Inventory server is installed on Linux, and users in the Identity Provider use the camel-case
naming convention, create users following the same convention in BigFix Inventory. Otherwise, the users
can not generate the audit snapshots.Note: User token is not available after a single sign-on user is created. If you need the token, for example, to run REST API calls, ask the BigFix Inventory administrator to provide it for you.
If the BigFix Inventory server is installed on Linux, and users in the Identity Provider use the camel-case
naming convention, create users following the same convention in BigFix Inventory. Otherwise, the users
can not generate the audit snapshots.Note: User token is not available after a single sign-on user is created. If you need the token, for example, to run REST API calls, ask the BigFix Inventory administrator to provide it for you.
Procedure
- Log in to BigFix Inventory, and click .
-
Select SAML as the single sign-on method.
The Instance ID field is automatically filled with the
defaultSPvalue. It is the identifier of the BigFix Inventory service. Together with the BigFix Inventory URL, it forms the overall Service Provider ID: https://BFI_host_name:BFI_port/ibm/saml20/defaultSP.Based on this value, the SAML Assertion Consumer Service URL is built: https://BFI_host_name:BFI_port/ibm/saml20/defaultSP/acs. The URL should be used for the configuration of the Identity Provider.
-
Specify the URL to the login page of the Identity Provider that you will use to
single-sign-on to BigFix Inventory.
For example:
- ADFS: https://<ADFS_hostname>/adfs/ls/IdPInitiatedSignOn.aspx?LoginToRP=https://BFI_host_name:9081/ibm/saml20/defaultSP
- ENTRA ID: https://launcher.myapps.microsoft.com/api/signin/<APPICATION ID / GUID>?tenantId=<TENANT ID / GUID>
Important: Ensure that the URL that you specify is correct. The address is not validated. If you make a typo in the URL, you might need to manually revert the SSO configuration. - Provide the public certificate of the Identity Provider. Click Browse to locate the key_name.cer certificate that you created.
-
Provide the URL of the certificate issuer of the Identity Provider. It is the issuer
name of the Identity Provider as it appears in the SAML assertion. Value is case
sensitive!
For example:
- ADFS: http://ADFS_host_name/adfs/services/trust
- ENTRA ID: https://sts.windows.net/<TENANT ID /
GUID>/Note: If you miss to add "/" at the of the line after "<GUID>", it will lead to web URL error, "403 HTTP Forbidden".
Important: Ensure that the URL that you specify is correct and ADFS_host_name matches the case configured in ADFS. The address is not validated. If you make a typo in the URL, you might need to manually revert the SSO configuration.Note: If there is "com.ibm.ws.security.saml.error.SamlException E CWWKS5045E: The value for the Issuer element http://MYAFDSHOST.my.lab/adfs/services/trust in the SAML assertion is not valid." error in the tema.log, check if the trustedIssuer in server.xml matches the case with http://MYAFDSHOST.my.lab/adfs/services/trust as in message. If not, correct and restart BigFix Inventory. - Click Save. This operation changes the server.xml and the server needs to reload the configuration. Please be patient and monitor the tema.log. If the server does not reload configuration property, restart BigFix Inventory server.
- Optional:
Certificate to be used for SSO SAML communication (valid for BigFix Inventory 11.0.2 or
lower:
-
Starting from
 BigFix Inventory the SSL certificate is used for the SSO setup. If you make
configuration on earlier version of BigFix Inventory you can switch to this option
following procedure: Using BigFix Inventory SSL certificate for SSO based on SAML.
BigFix Inventory the SSL certificate is used for the SSO setup. If you make
configuration on earlier version of BigFix Inventory you can switch to this option
following procedure: Using BigFix Inventory SSL certificate for SSO based on SAML.
- To use a custom certificate for the SSO setup, see: <deprecated> Using a CA-signed (custom) certificate for SSO based on SAML. Only valid for BigFix Inventory 11.0.2 or lower.
-
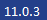
Up to BigFix Inventory 11.0.3 by default new dedicated self-signed certificate was
created as default.
 From BigFix Inventory 11.0.3 this is not longer used, in favor of using already
existing SSL certificate (option a above).
From BigFix Inventory 11.0.3 this is not longer used, in favor of using already
existing SSL certificate (option a above).
-
Starting from
-
After the BFI server has reload the configuration / has been restart, there should
became available option Download Service Provider Metadata.
-
Click on the Download Service Provider Metadata link, and save
the spMetadata.xml file.
Note: When the SAML single sign-on entry is created, only the Delete button, and the Download SP Metadata link are enabled. If the download link is not displayed, restart the BigFix Inventory server.
- Review the URL in downloaded spMetadata.xml. Confirm that the URL matches.