Security
Click the sixth tab to open the Security dialog.
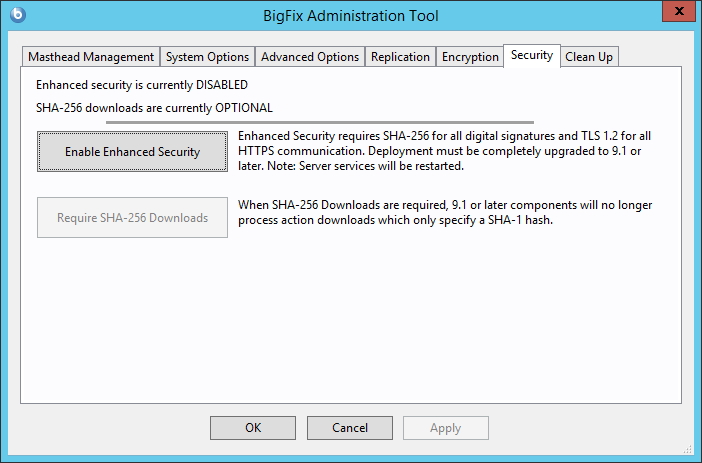
Click the Enable Enhanced Security button to adopt the SHA-256 cryptographic digest algorithm for all digital signatures as well as for content verification and to use the TLS 1.2 protocol for communications among the BigFix components.
- The updated license was gathered.
- Unsubscribe from all external sites that do not support SHA-256.
BESRootServer service
fails to restart automatically. To solve the problem, restart the
service manually.To enable enhanced security on a Disaster Server Architecture (DSA) server in Linux environments:
You must enable it only on the primary server by running the command ./BESAdmin.sh -securitysettings -sitePvkLocation=<path+license.pvk> -enableEnhancedSecurity -requireSHA256Downloads.
You do not have to enable it on the replica servers. You might be requested to run the command ./BESAdmin.sh syncmastheadandlicense -sitePvkLocation=<path+license.pvk> [-sitePvkPassword=<password>] on the replica servers to ensure that the updated action site is propagated to the replica servers as well.
To enable enhanced security on a Disaster Server Architecture (DSA) server in Windows environments:
You must enable it only on the primary server by following the procedure described in On Windows Systems.
You must run the .\BESAdmin.exe command on the replica servers to ensure that the updated action site is propagated to the replica servers as well.
If you click Enable Enhanced Security without selecting Require SHA-256 Downloads, the SHA-256 algorithm will be used to for digital signatures and for content verification, TLS 1.2 protocol will be used for communications among the BigFix components but you will still be able to download SHA-1 content from external sites.
For more information about the BigFix Enhanced Security feature, the supported security configuration and enhanced security requirements evaluation, see Security Configuration Scenarios.