Installing HashiCorp Vault
This section provides a step-by-step guide to installing HashiCorp Vault.
HashiCorp Vault, a powerful tool secures secrets management and key management services (KMS). HashiCorp Vault ensures robust encryption, secure access to sensitive data, and centralized management of secrets across your applications and infrastructure. The page covers the installation process, initial configuration, and integration with your deployment environment to enhance security and compliance.
Prerequisite:
Make sure to assign required privileges in the security context (scc) to the below service accounts on the namespace, where the vault will be deployed.
- vault-cluster-agent-injector
- vault-cluster
In case of anyuid scc, add the below sections under user:
oc edit scc anyuid
- system:serviceaccount:vault-cluster-agent-injector:vault-server
- system:serviceaccount:vault-cluster:vault-serveInstalling HashiCorp Vault
To install HashiCorp Vault, follow the steps below:
-
As a first step in installation, add the HashiCorp value repository using the below helm command.
helm repo add HashiCorp https://helm.releases.hashicorp.com helm repo update - Create a vault-values-override.yaml file to deploy the vault in HA mode and vault data
persistence mode. A sample yaml file along with configuration is shown
below.
# Vault Helm Chart Value Overrides global: enabled: true tlsDisable: true resources: requests: memory: 256Mi cpu: 250m limits: memory: 256Mi cpu: 250m server: # Use the Enterprise Image # image: # repository: "hashicorp/vault-enterprise" # tag: "1.16.1-ent" # These Resource Limits are in line with node requirements in the # Vault Reference Architecture for a Small Cluster resources: requests: memory: 8Gi cpu: 2000m limits: memory: 16Gi cpu: 2000m # For HA configuration and because we need to manually init the vault, # we need to define custom readiness/liveness Probe settings readinessProbe: enabled: true path: "/v1/sys/health?standbyok=true&sealedcode=204&uninitcode=204" livenessProbe: enabled: true path: "/v1/sys/health?standbyok=true" initialDelaySeconds: 60 # extraEnvironmentVars is a list of extra environment variables to set with the stateful set. These could be # used to include variables required for auto-unseal. extraEnvironmentVars: # VAULT_CACERT: /vault/userconfig/tls-ca/ca.crt # extraVolumes is a list of extra volumes to mount. These will be exposed # to Vault in the path `/vault/userconfig/<name>/`. extraVolumes: # - type: secret # name: tls-server # - type: secret # name: tls-ca # - type: secret # name: kms-creds # This configures the Vault Statefulset to create a PVC for audit logs. # See https://www.vaultproject.io/docs/audit/index.html to know more auditStorage: enabled: true standalone: enabled: false # Run Vault in "HA" mode. ha: enabled: true replicas: 2 raft: enabled: true setNodeId: true config: | ui = true cluster_name = "vault-cluster-with-integrated-storage" listener "tcp" { tls_disable = 1 address = "[::]:8200" cluster_address = "[::]:8201" } storage "raft" { path = "/vault/data" retry_join { leader_api_addr = "http://vault-cluster-0.vault-test-internal:8200" } retry_join { leader_api_addr = "http://vault-cluster-1.vault-test-internal:8200" } autopilot { server_stabilization_time = "100s" last_contact_threshold = "10s" min_quorum = 5 cleanup_dead_servers = false dead_server_last_contact_threshold = "10m" max_trailing_logs = 1000 disable_upgrade_migration = false } } # Vault UI ui: enabled: true serviceType: "LoadBalancer" serviceNodePort: null externalPort: 8200In case, if there are more that 2 vaults replica, you can adjust and update the below properties, accordingly:- retry_join
- replicas
- After configuring the yaml file, you can install the Vault using Helm chart as shown
below.
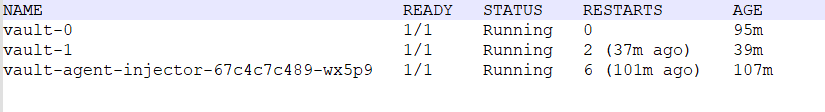
helm upgrade --install vault hashicorp/vault --namespace vault --set "global.openshift=true" --set "server.image.repository=docker.io/hashicorp/vault" --set "injector.image.repository=docker.io/hashicorp/vault-k8s" -f /<path-to-your-vault-override-values-file>/vault-override-values.yaml --debug - On successful installation of the vault, you can verify the installation using the below
command.
oc get pods --namespace vaultNote: After installation, make sure to unseal the vault as shown below. Otherwise, the pods will keep restart.