Configuring Domino as an OIDC provider
To prepare a Domino server to be an OIDC identity provider, you must configure it in Domino's IdP Catalog application and in the Domino Directory's Internet Site document. You can then configure Domino as a clustered OIDC provider.
Preparing the OIDC provider's Internet Site document
- Open the Domino Directory (names.nsf).
- Open the Internet Site document for the site hosting the Domino OIDC provider.
- Under the Domino Web Engine tab and the HTTP
Sessions section, click the drop-down arrows next to
Session Authentication and select Single
Server, and then set all of the TLS-related options in that section
to Yes. The OIDC and OAuth specifications mandate use of TLS to
encrypt all network traffic. We also highly recommend setting the notes.ini
variable DominoSessionCookieUniqueNames=1 to prevent clustered Domino servers
hosting the same website from over-writing each other's session cookies.

- On the Security tab, in the TCP Authentication section, set Redirect TCP to TLS to Yes and the other circled fields to No.
- In the TLS Authentication section, set
Anonymous to No and enable at least
one form of authentication to this internet site.

- On the Basics tab, click the drop-down next to the
Domino OIDC provider hostname field and select the
DNS hostname for the Domino OIDC provider. Setting this value to "None" and
rebooting the Domino HTTP task will disable the Domino OIDC provider. The
Domino servers that host this site field must contain
one or more Domino server names, as the OIDC provider cannot be configured to
run on all servers in the domain.

- Save and close the document.
- Restart the Domino server.
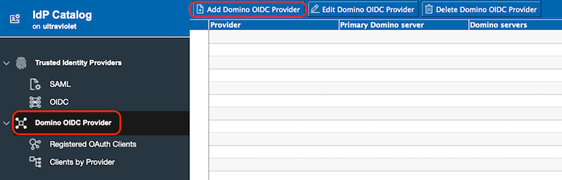
Create a Domino OIDC provider
- Open the IdP Catalog application (idpcat.nsf).
- Select the Domino OIDC Provider tab in the navigation,
and then click the Add Domino OIDC Provider button in the
header.
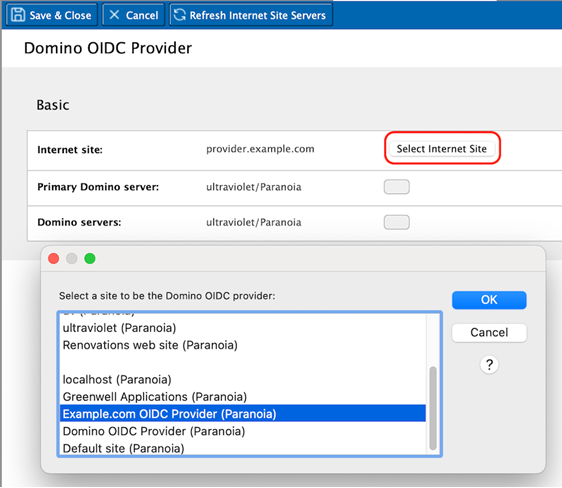
- Click Select Internet Site button beside the
Internet site field, and select the internet site
that will host the Domino OIDC provider. This will also pre-populate the Primary
Domino server and Domino servers fields.
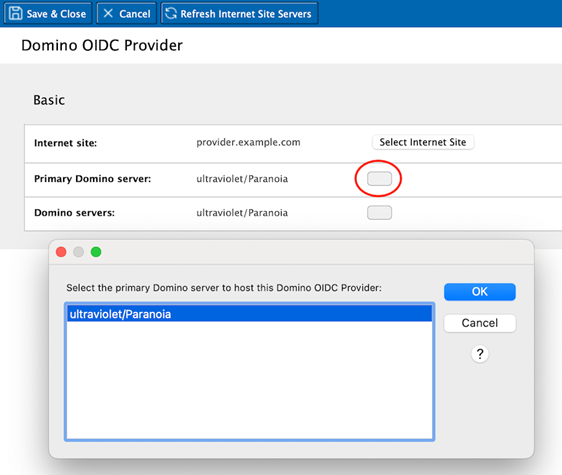
- If you want to change which Domino server will be the primary OIDC provider
server, click the button beside the Primary Domino server
field and select the desired server.
- If you want to change the set of Domino servers that will host the OIDC provider, click the button beside the Domino servers field and select the desired servers.
- Save and close the document.