Enabling mandated NRPC port encryption
Enable and enforce encryption of NRPC traffic by default for increased security.
Before you begin
About this task
Procedure
- Upgrade the server address book design to 14.5.
-
In the server address book, sign and enable the scheduled agent
"CheckPortEncryption".
Note: The signer needs to have permission to run unrestricted agents on the server.The agent runs on all servers once a day, but you change the schedule based on your needs:
- On servers prior to 14.5, the agent checks the mandated encryption settings in the directory profile and modifies the server's encryption level if needed.
- On servers running 14.5 or later, the agent does nothing, as there is code in 14.5 that manages encryption level.
- Enables encryption in NRPC port ini, if needed. The change does not have an impact until port is initialized.
-
Updates "PORT_ENC_ADV" ini to have the right settings. The value is read dynamically and does not require a server restart.
-
Create a server group for servers that you want to exclude from mandated
encryption checking.
If you create one, add the excluded server group to the directory profile. You can also exclude individual servers in the directory profile.
The excluded server list serves the following purposes:- When the target server is on the excluded server list, outbound check is skipped on a 14.5 client.
- The primary administration server checks the encryption level of all servers in the domain, unless they are excluded. Results of these checks are used as basis for marking the mandated encryption state as either "Compliant" or "Non-compliant". For the actual check to happen, the state needs to be Compliant.
Note: If a Domino 14.5 server is in the excluded server list, the server will still initialize the port settings from the Directory Profile document in the Domino Directory. To avoid any conflicts with what an administrator might have set for port encryption notes.ini parameters, it is best to set DISABLE_MANDATED_ENCRYPTION=1 and DISABLE_OUTBOUND_MANDATED_ENCRYPTION=1 so that the server ignores the overrides coming from Directory Profile document.If servers are down, they need to be excluded or brought up for primary admin server checks to succeed. If servers are down for maintenance or upgrade, there's no need to update if already reached once.
Passthru and ADPWSync utility servers are automatically skipped.
If there are no other servers to exclude, you can skip this step. -
Create a server group or use
* - [All Servers]for servers 14.5 or later.If you want to manually manage server-side ini's, this step is not necessary.
-
Enable server ini's using a server configuration document.
Configure the following:After these are set in your notes.ini, you need to restart Domino servers.
Setting Description DEBUG_MANDATED_ENCRYPTION=1 Enables debug logging, which is useful for troubleshooting. MANDATEDENC_ACTIVE_REFRESH_TIME=<# of seconds> Defines how often mandated port encryption configuration is refreshed on the server. The default is every 24 hours, and server polls every 60 minutes.
DEBUG_PORT_ENC_ADV=1 Enables port encryption debug, which is useful for troubleshooting. - Edit desktop policy in tab and set "DISABLE_MANDATED_ENCRYPTION" & "DISABLE_OUTBOUND_MANDATED_ENCRYPTION" ini values to 0.
-
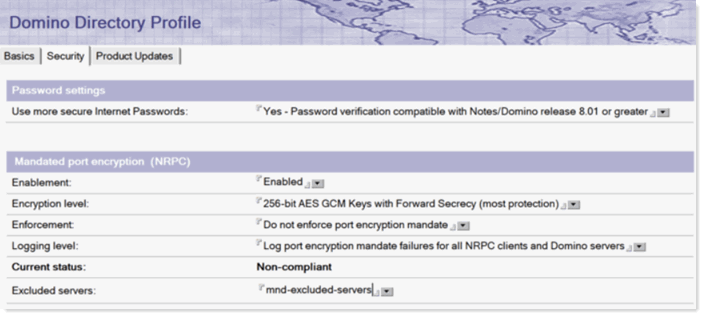
Edit the directory profile and enable logging for mandated port encryption
checks. This allows you to ensure things are working before enabling the actual
checks.
-
On the primary admin server, refresh PortEncrypt by running the
portenc refresh command.
This triggers the process of updating the configuration cache on the primary administration server, followed by checking encryption level on all servers. If all server encryption levels are compliant with the defined mandated port encryption level, then the "Mandated port encryption state" in directory profile will be marked as Compliant.
To verify the state, you can run the command portenc show on the primary admin server.
- Wait a few days to confirm no connection failures are logged.
- If there are no issues, enable the mandated port encryption to "Enforce port encryption mandate. Then, repeat step 7.