V11 Overview
BigFix Platform 11 introduces the following major changes in the security area:
- OpenSSL has been upgraded to 3.1.1
- TLS 1.3 protocol for HTTPS communications is now supported
- SHA-384 is now available as cryptographic hash function for all digital signatures.
- SHA-256 and TLS 1.2 are the minimum security levels used for digital signatures and HTTPS communications respectively
- SHA-384-only and/or TLS 1.3-only modes can be optionally enforced
- SHA-1 and SHA-256 are still used for validation of downloaded files in prefetch statements
- BigFix 10.0.7 is the minimum version supporting the upgrade of the BigFix Server components to Version 11.
Considerations on the upgrade of the BigFix Platform to v11
- BigFix 10.0.7 is the minimum version supporting the upgrade of the BigFix server components to Version 11.
- “Enhanced Security” must be enabled (Security Configuration Scenarios).
Note: Plan to enable the "Enhanced Security" well in advance of the upgrade because the feature takes time to propagate through the deployment. For detailed information and guidance, please read carefully Guidance on Enabling Enhanced Security prior to enabling "Enhanced Security".
On Windows, you can enable the "Enhanced Security" using the relevant button of the graphical BigFix Administration Tool, as shown in the following picture:
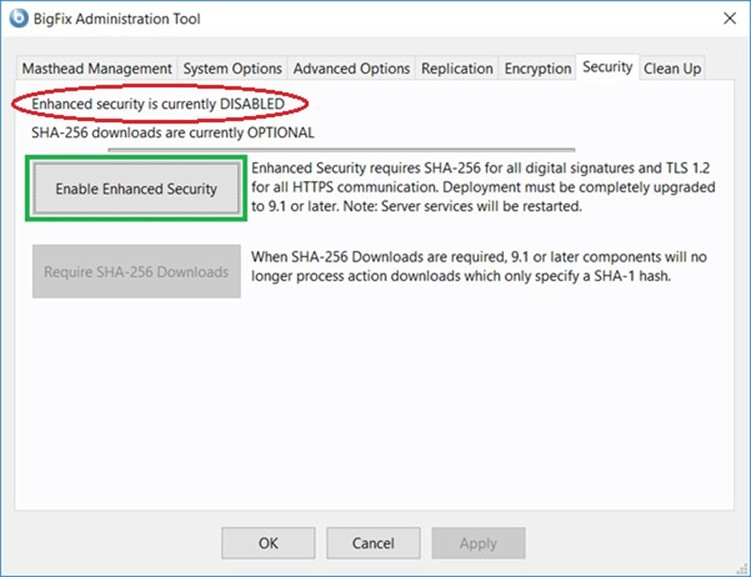
/opt/BESServer/bin/BESAdmin.sh -securitysettings -enableEnhancedSecurity
-sitePvkLocation=<path+license.pvk> [ -sitePvkPassword=<password> ]- findinvalidsignatures on Linux platforms
- findinvalidsignatures on Windows platforms.
Results of the upgrade to BigFix v11
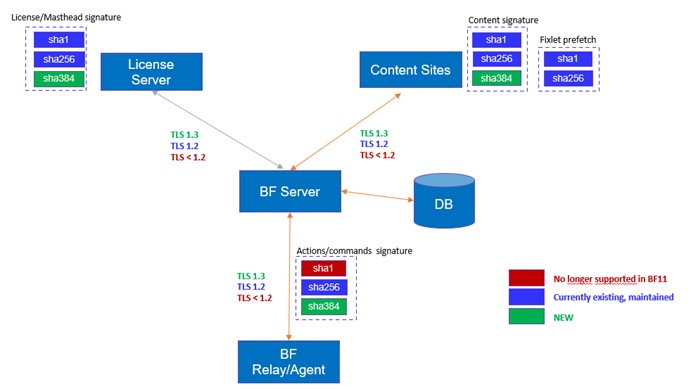
- TLS handshakes will use SHA-384 certificates whenever they are available. After
upgrading the BigFix Server to v11, SHA-384 certificates will be available to:
- All Agents/Relays at Version 11
- Agents and Relays at 10.0 patch 7 (or later patch) that have had their certificates refreshed, either automatically for expiration of the 13-month validity period, or manually with the “client certificate refresh” actionscript command (see Client certificate)
- All Agents and Relays installed after upgrading the BigFix Server to Version 11, regardless of their version.
- Content generated by MOs and NMOs like sites, Fixlets, analyses, actions, etc. will be signed with both SHA-256 and SHA-384. To validate such content, BigFix components at v11 will rely on both, while BigFix components at earlier versions will rely on the SHA-256 signature.
- The BigFix Server will validate external site content using either the SHA-256 or the SHA-384 signature.
- The BigFix Server will process Agent reports that are signed using either SHA-256 or SHA-384.
- BigFix Platform 11 will support both TLS 1.2 and TLS 1.3 (with TLS 1.3 being always the first attempted option), while it will no longer support TLS 1.1 or below in ANY scenario requiring HTTPS.
Note: Because of the above, BigFix Platform components at Version 11 will no longer be backward compatible with BigFix components at version 9.0 or lower.
Note: SHA-1 and SHA-256 are still used for validation of downloaded files in prefetch statements.
The communications with the BigFix Database are not affected by the version change but depend on the database configuration.
The following picture provides a summary of what is described above.
Enforcing SHA-384-only for signatures
You can optionally require the usage of SHA-384 as the only allowed cryptographic hash function for all digital signatures.
Note: This requires the whole deployment to be at Version 11. BigFix components at earlier versions will be no longer manageable (e.g. Agents and Relays will no longer be able to gather, validate and process content propagating from the BigFix Server).
- Any content generated by MOs and NMOs like sites, Fixlets, analyses, actions, etc. will be signed only with SHA-384. Therefore, only Agents and Relays at Version 11 will be able to validate and process it.
- The BigFix Server will validate external site content relying only on the SHA-384 signature.
- The BigFix Server will only process Agent reports that are signed using SHA-384.
Enforcing TLS 1.3-only for HTTPS communications
You can optionally require the usage of TLS 1.3 as the only allowed protocol for HTTPS communications.
Note: This requires the whole deployment to be at Version 11. BigFix components at earlier versions will be no longer manageable (e.g. Agents and Relays will no longer be able to communicate via HTTPS with BigFix components of Version 11).
- Internal HTTPS communications between BigFix components
- HTTPS communications where a BigFix component plays as HTTPS Server (e.g. a REST API client connecting to the BigFix Server, or a browser connecting to the Relay Diagnostics page)
- External site gathers performed by the BigFix Server.
Libraries upgraded in V11
For a full list of libraries upgraded in BigFix Platform V11, see What is new in BigFix 11 Platform.
Updated system requirement matrix in V11
In BigFix Platform 11 the system requirement matrix has been updated. For more information, see BigFix Support Matrix.