Preparing endpoints to accept ESU patches
After subscribing the endpoints in your deployment to a BigFix Extended Security Updates (ESU) patch site, you can use the content in the site to prepare the endpoints to accept the ESU patches.
About this task
Before you start applying ESU patches through BigFix, it is important to first ensure that your endpoints are properly configured to accept and deploy these updates. This includes verifying that your endpoints are enrolled in the BigFix ESU patch site.
Options for Accessing Extended Security Updates (ESUs)
You can access Extended Security Updates (ESUs) through the following options depending on your environment.
Procedure
-
Non-Azure Physical and Virtual Machines
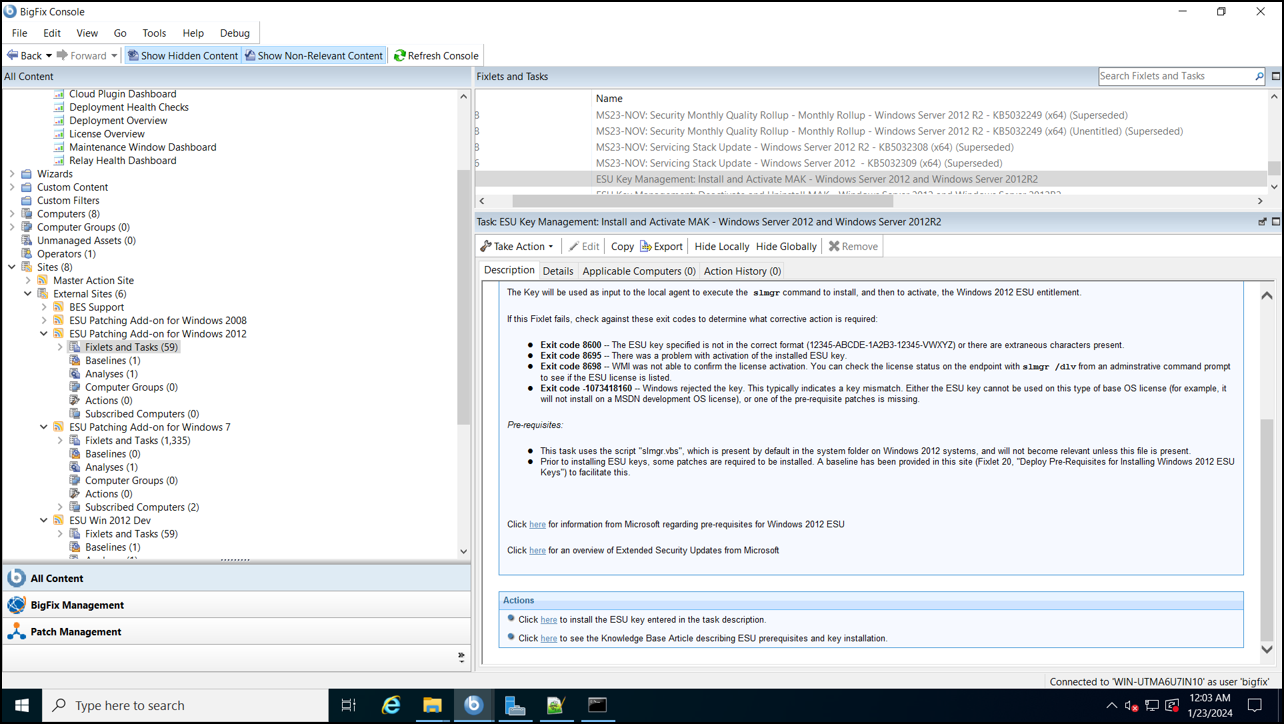
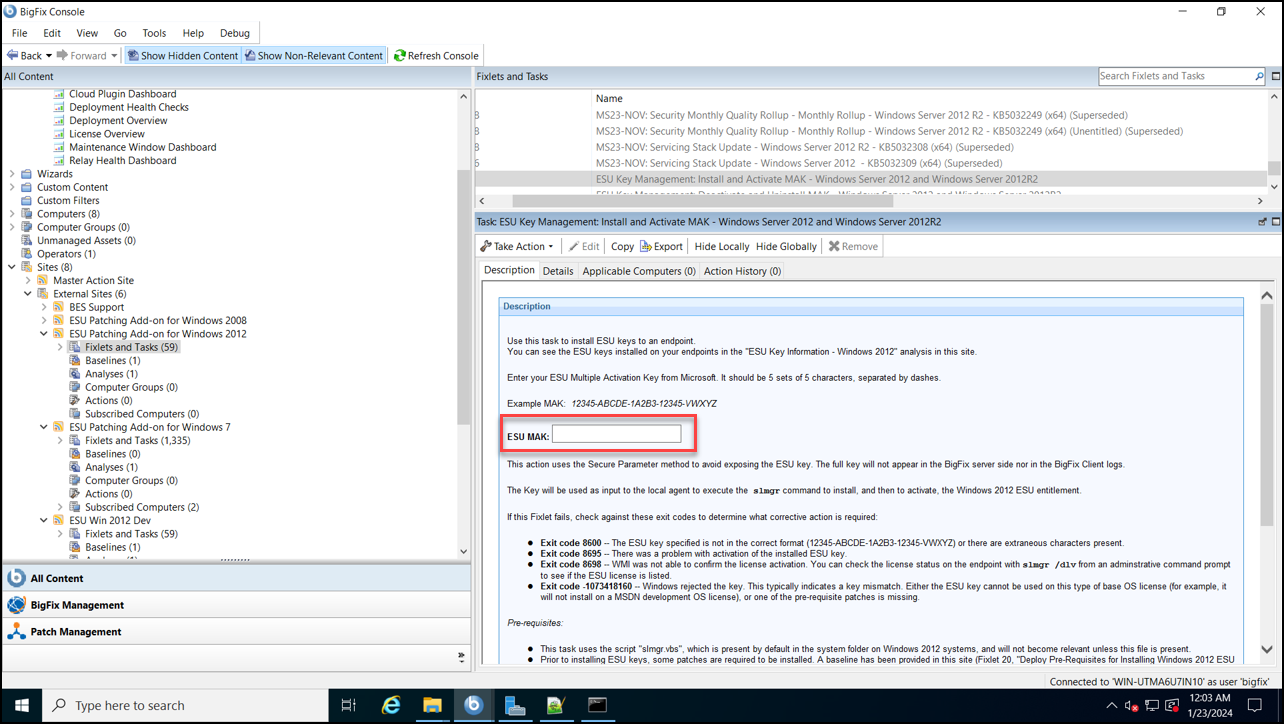
The ESUs on non-Azure virtual machines are obtained by applying a MAK to the relevant servers. This MAK key enables Windows Update servers to continue providing critical security updates beyond the standard support period.
-
Azure Virtual Machines
Applicable Virtual Machines (VMs) hosted in Azure are automatically enabled for ESUs, and these updates are provided free of charge. There is no need to deploy a Multiple Activation Key (MAK) key or take any additional action. Learn more about this option by visiting the Extended Security Updates on Azure.
-
Azure Arc-Enabled Servers
For servers located on-premises or in a hosted environment, you can enroll your Windows Server 2012 and Windows Server 2012 R2 machines for ESUs through the Azure portal. By connecting through Azure Arc, you will be billed monthly via your Azure subscription, and ESUs will be delivered automatically without the need for a MAK key.
Learn more about enrolling your servers through Azure Arc by visiting Extended Security Updates enabled by Azure Arc.