A Basic installation
The most basic installation requires the Remote Control target and controller components. Use the two components to start a peer to peer remote control session, for which the policies are defined only at target level.
The port to be used for target to controller communication is configurable at installation time. The default is port 888.
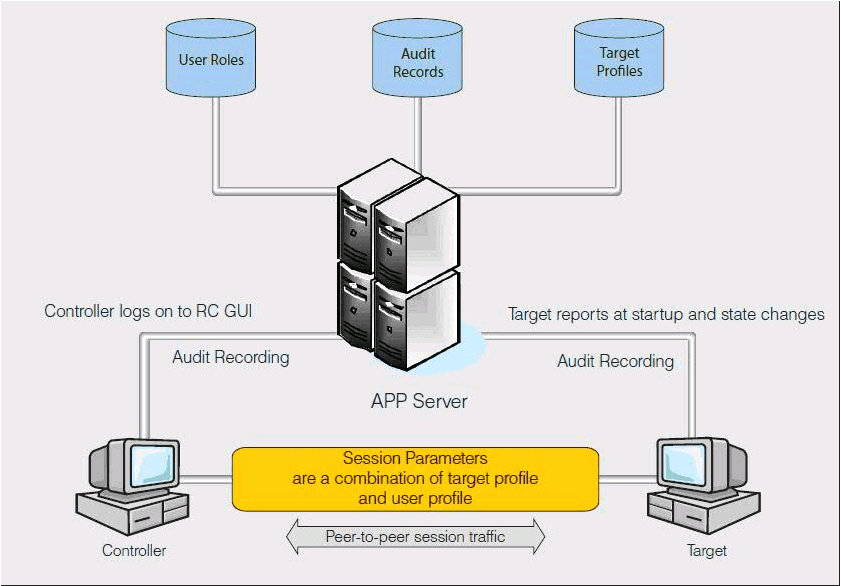
Such an installation provides basic audit information. This information is accessible from the BigFix® console. It is also stored in the application event log, in a Windows operating system, or system log, in a Linux operating system. However, if centralized auditing and management of users and computers is required, install the server component.
The server component provides a single interface where controller users can easily search for targets. They can also organize the targets that are most frequently accessed and view their session history. For an administrator, a managed environment provides the following extra capability.
- Centralized management of users and targets: Users can be organized into groups with similar profiles. They can be organized manually, by using the Remote Control server interface, or by importing users and groups from LDAP or from Microsoft Entra ID. Similarly, targets can be organized into groups manually or by setting target membership rules to automatically assign a target to a specific group. For more information about target membership rules, see the BigFix® Remote Control Administrator's Guide.
- Centralized policy management: When a session is started from the server interface, the permissions that are set for the session are derived from the target and controller properties. Provides more flexibility to define different levels of access, against a single target, for different users in your organization.
- Centralized auditing and recording repository: Administrators can use the Remote Control server interface to browse and examine audit information. They can also view recordings that are associated with a specific remote control session. Administrators can search the existing session history. For example, by user ID or computer name.
- Access request management: Administrators can grant temporary access, or increase the level of access, to a target or group of targets. Temporary access can be granted to Remote Control registered and unregistered users.
- Reporting capabilities