z/OS and DCAS host authentication
In a z/OS and DCAS environment, Web Express Logon supports two different models—one in which users are identified via client certificates (called Certificate-based Web Express Logon) and one in which users are identified via a network security application. Since both of these models have their own requirements for user identification, the Web Express Logon configuration steps are different for each model. In a certificate-based environment, you must configure your HTTP server as well as the browser and Java 2 keystore on each Z and I Emulator for Web client. In a non-certificate-based environment, you must configure your network security application and create your HCM database. Both models require you to configure the Digital Certificate Access Server (DCAS).
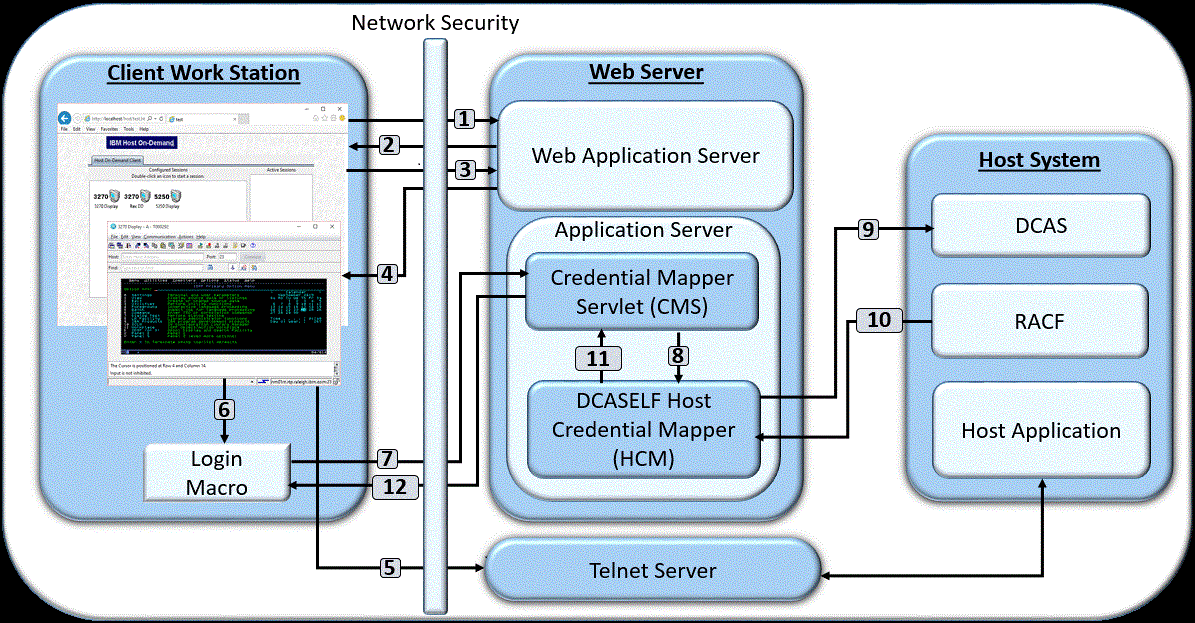
- The user clicks a link to launch the Z and I Emulator for Web desktop, which sends an HTTP request to the Web server.
- The server requests a client certificate to perform client authentication. The client certificate must be stored in the browser's keyring.
- The user sends the client certificate to the server.
- The Web server returns the HTTPS request, and the Z and I Emulator for Web desktop displays.
- The user launches a host session.
- The login macro executes.
- The macro sends an HTTPS request to the CMS to obtain the host credentials.
- The CMS passes the application ID to the DCASELF HCM plug-in.
- The DCASELF HCM retrieves the user's certificate from the Web application server.
- The host (RACF) identifies the client, checks the client's authorization, and returns the passticket to the DCASELF HCM plug-in.
- The DCASELF HCM plug-in returns the host ID and passticket to the CMS.
- The CMS returns the host credentials to the client as an XML document.
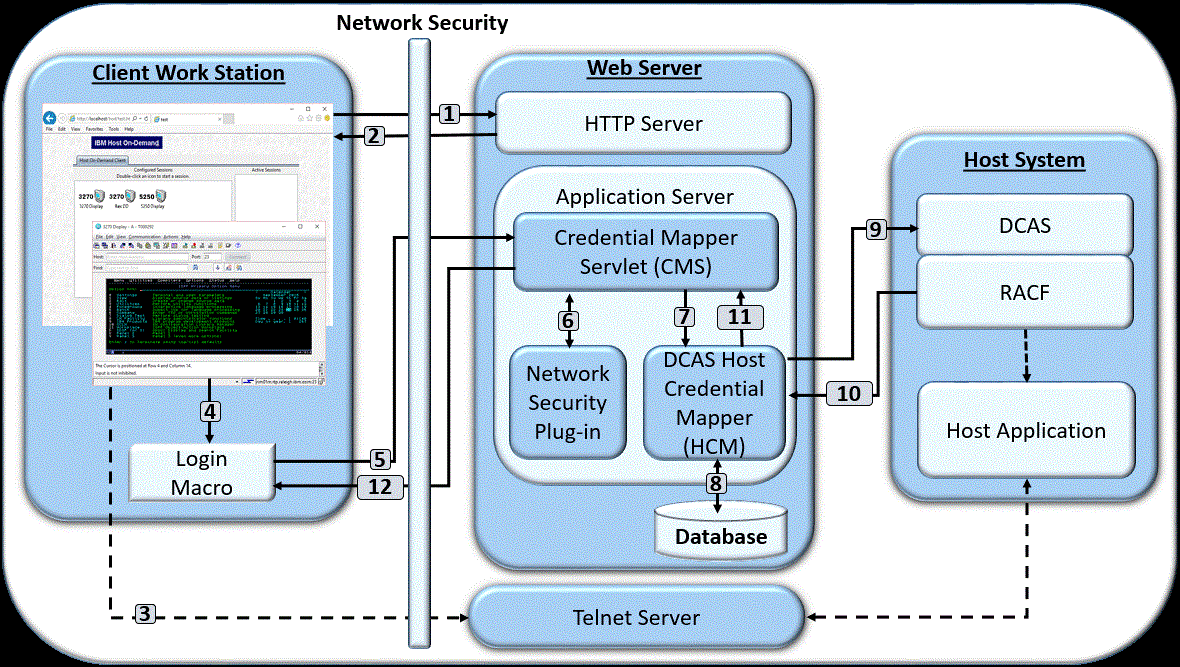
- The user clicks a link to launch the Z and I Emulator for Web desktop, which sends an HTTPS request through the network security application to the HTTP server.
- The Web server returns the HTTPS request, and the Z and I Emulator for Web desktop displays.
- The user launches a host session.
- The login macro executes.
- The macro sends an HTTPS request to the CMS to obtain the host credentials.
- The CMS retrieves the user's network ID from the Network Security plug-in.
- The CMS passes the network ID and application ID to the DCAS HCM plug-in.
- Using the network ID and application ID, the DCAS HCM plug-in calls upon a database, such as IBM DB2, to map the user's host ID.
- The DCAS HCM plug-in passes the user's host ID and application ID to Digital Certificate Access Server (DCAS) and requests a passticket.
- The host (RACF) identifies the client, checks the client's authorization, and returns the passticket to the DCAS HCM plug-in.
- The DCAS HCM plug-in returns the host ID and passticket to the CMS.
- The CMS returns the host credentials to the client as an XML document.
The login macro automatically inserts the user's credentials in the logon screen fields without user intervention. Now the user is fully authenticated and can proceed with the session.
For more information, refer to Configuring macro-based automation in a z/OS and DCAS environment.