Integrated Backup Encryption
These topics provide information about Integrated Backup Encryption.
Although it is possible to encrypt backups since version 11.10.xC1 using Backup Filters, the process of setting up encryption keys and keeping track of all the elements necessary for the encryption and decryption of backups is neither short or easy, and so, the Backup filter functionally has been mostly relegated to compress/decompress backups, which can be achieved more easily.
Although there is a way to encrypt the backups using a local encryption key provided by the operator, Integrated backup Encryption was designed to work mainly with Remote Key Servers because they offer the flexibility and reliability needed to minimized the likelihood of rendering backups unusable due misplaced/missing encryption keys.
Integrated Backup Encryption does not reuse the encryption keys used for Storage Space Encryption. When a backup is performed, the engine decrypts the pages before sending them to the backup client and the On-Bar/ontape utilities receive a stream of unencrypted pages.
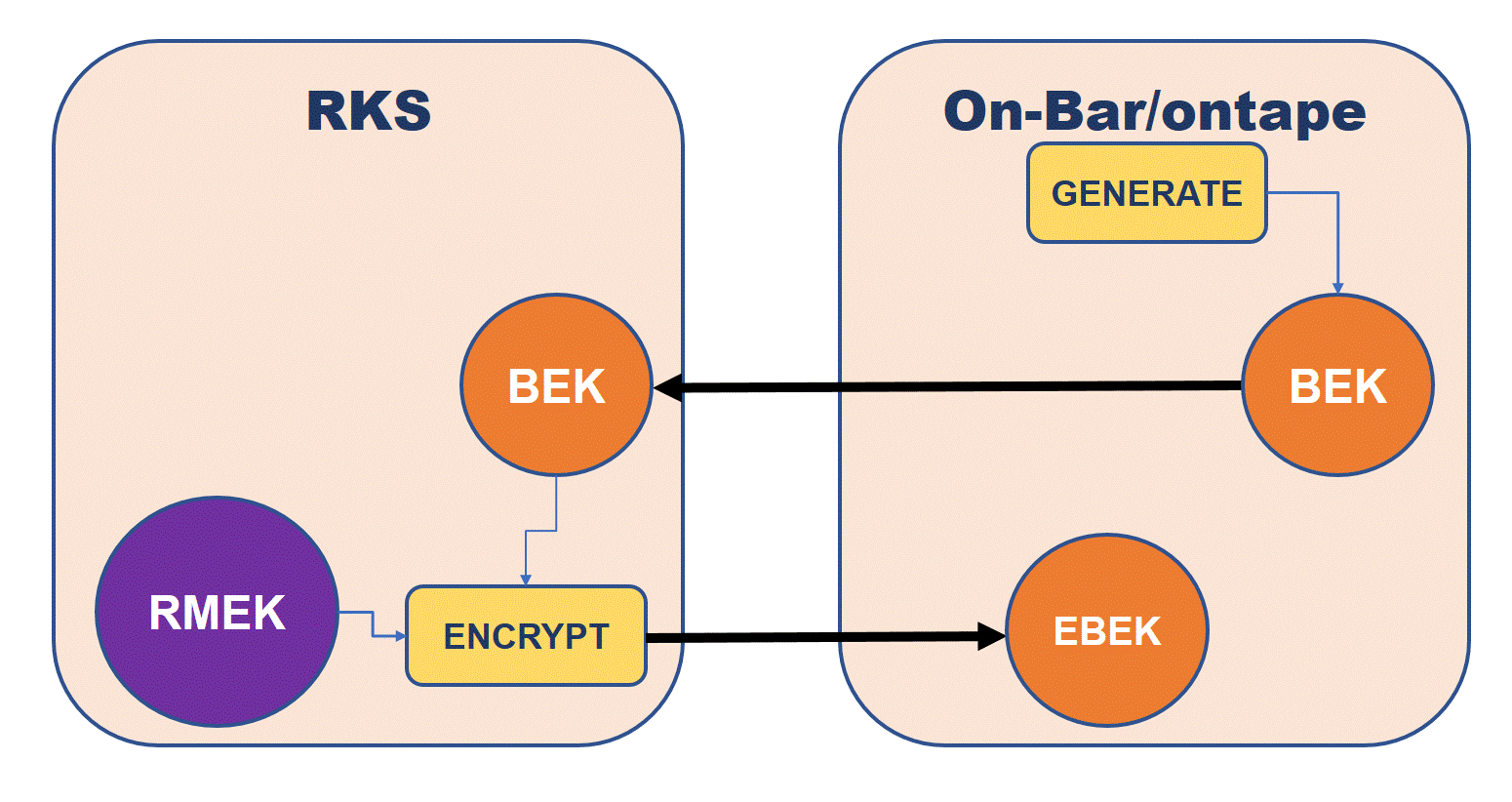
The backup client then generates an encryption key called Backup Encryption Key (Depending on the capabilities of the RKS, the backup encryption key can be generated locally, or at the RKS). The backup encryption key is then used to encrypt the backup data.
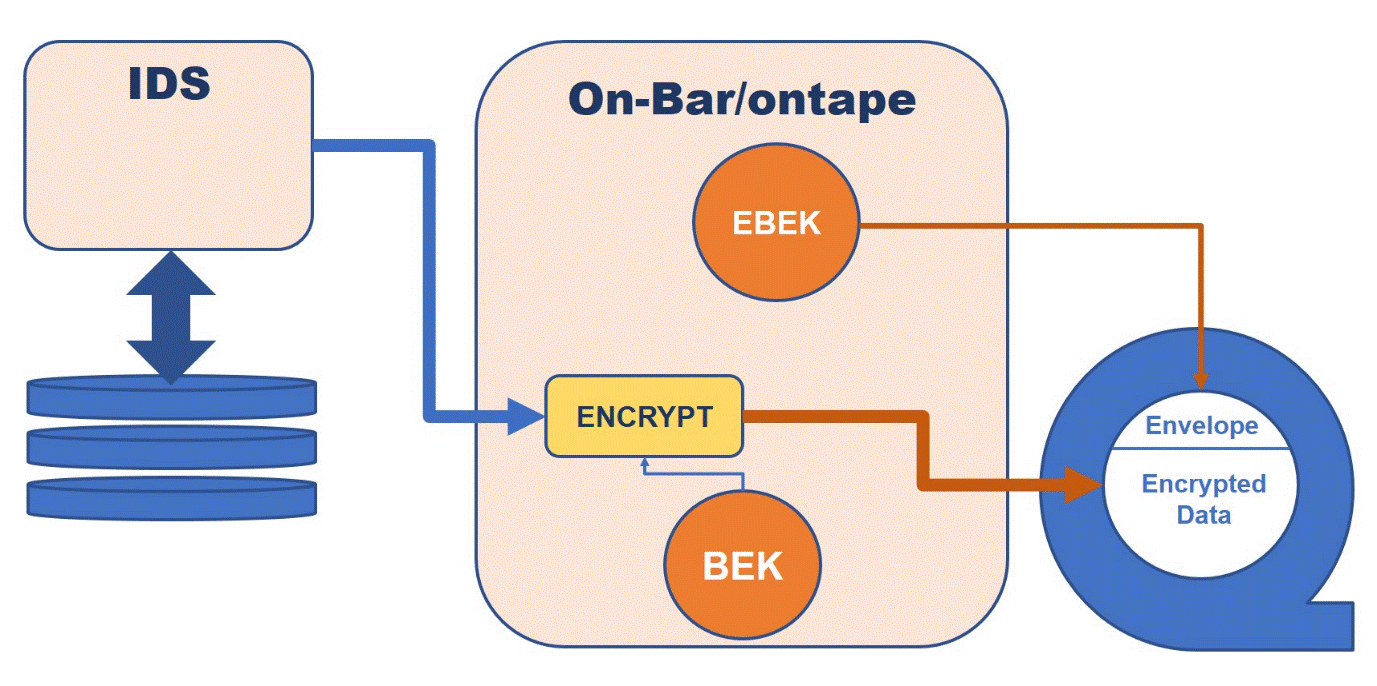
The backup client also encrypts the backup encryption key using a Remote Master Encryption Key (RMEK) to generate an Encrypted Backup Encryption Key (EBEK) and stores the identification of the Remote Master Key, the Encrypted Backup Encryption Key, and other relevant information necessary to decrypt the data in a structure called the Encryption Envelope (envelope for simplicity). The envelope structure is stored together with the encrypted backup data and therefore it is impossible to lose or misplace the backup encryption key since it is always stored together with the data that it protects.
As long as there is access to the RKS and the Remote Master Encryption Key is not deactivated, the backup will be decryptable.
The process of encrypting a backup, as already described above, requires the generation of a backup encryption key for each backup session. All backup objects generated in that session will share the same BEK (For On-Bar, this means that each storage space and log file backed up will share the same BEK.).
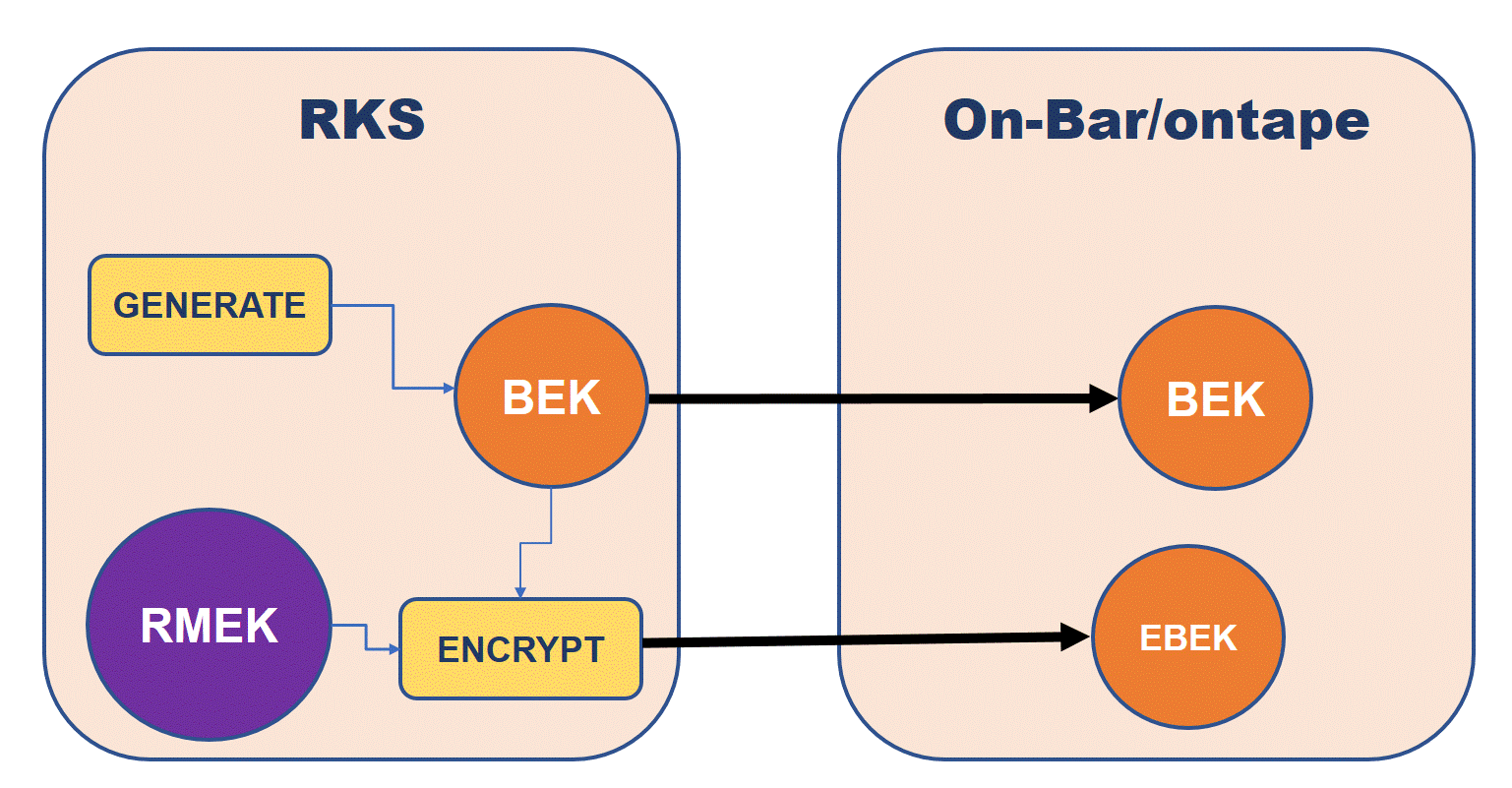
- Method 1: The RKS is capable of generating symmetric encryption keys. In this case the RKS will generate the BEK and provide the backup client with both the BEK and the product of encrypting the BEK with the Remote Master Encryption Key (EBEK).
The BAR_ENCRYPTION configuration parameter
In order to use Integrated Backup Encryption, you must setup either a local key file or access to a remote keys server. Then you need to set the BAR_ENCRYPTION configuration parameter to let know the backup client that you want to use Integrated Backup Encryption and which method you want to use.