Nomad federated login
Nomad federated login avoids users being prompted for their HCL Notes ID passwords when they set up the HCL Nomad. Instead, they are prompted only for credentials from a SAML identity provider (IdP) that is accessed through the Nomad server (SafeLinx); the users don't need to enter their Notes ID passwords.
With Nomad federated login, a Domino ID vault server acts as a SAML service provider. It requests and obtains an authentication assertion from your IdP that allows it to trust a user's identity and obtain their Notes ID from the vault. The Nomad (SafeLinx) server is used for SAML communication between the Domino server and the IdP.
For information about Nomad, see the Nomad administration documentation. Also, refer to the Nomad for web browsers user documentation and the Nomad for iOS user documentation.
The following diagram illustrates the steps that occur to obtain a user's Notes ID file from the vault when a user first sets up Nomad and Nomad federated login is configured:
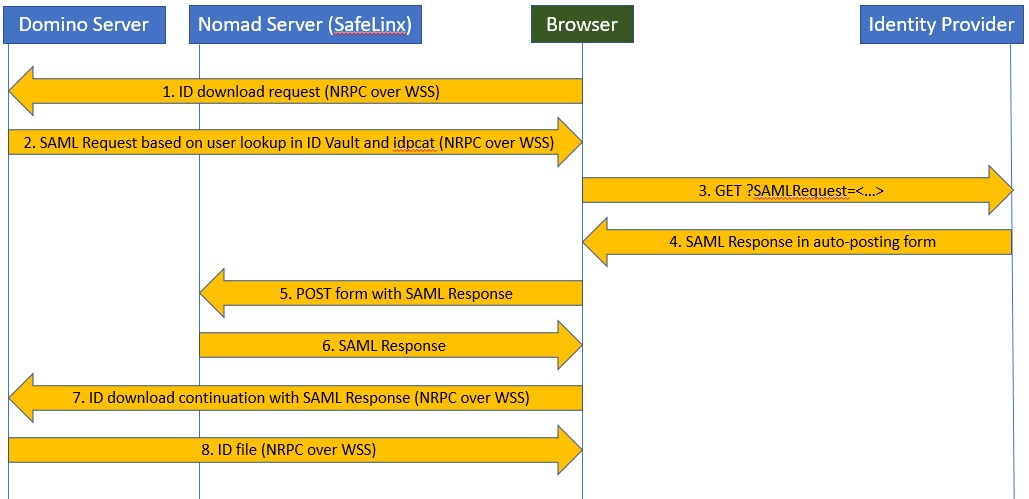
- The browser requests an ID download from the vault via the Nomad server (SafeLinx).
- The Domino ID vault server looks up the user in the vault database. It uses an IdP configuration document in idpcat.nsf to return a signed SAML request to the browser via the Nomad server.
- The browser sends the signed SAML request to the IdP with a previously-established session cookie.
- The IdP authenticates the user via the cookie and returns a SAML response to the browser in an auto-posting form.
- The browser posts the SAML response to the Nomad server.
- The Nomad server reflects the SAML response back to the browser.
- The browser continues the ID download request with the SAML response via the Nomad server.
- The ID vault server verifies the SAML assertion and returns the user’s ID file.