Access control interactions
The access control policy framework controls how access control works in HCL Commerce.
The following syntax diagram shows access control policy interactions. The details are described below the diagram.
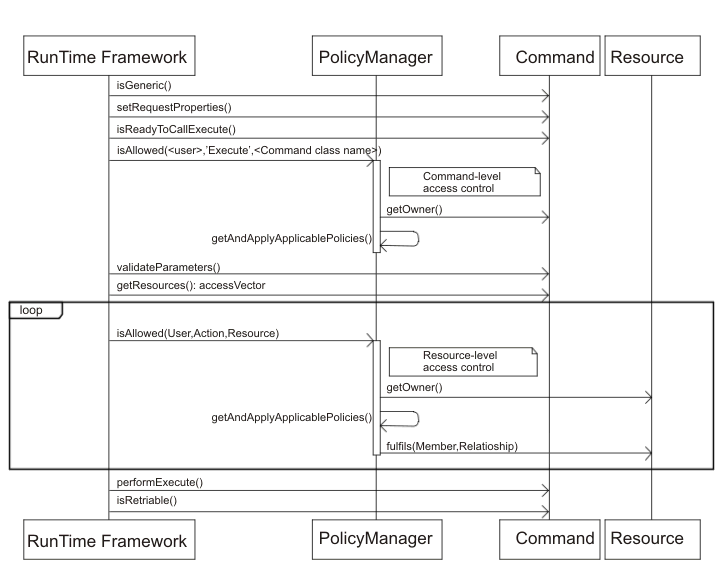
The preceding diagram shows actions that are performed by the access control policy manager. The access control policy manager is the access control component that determines whether the current user is allowed to perform the specified action on the specified resource. It determines access by searching through the policies in groups to which the resource owner subscribes. If the resource owner does not subscribe to any policy groups, it searches through the policies in groups to which the resource owner's closest ancestor subscribes. If at least one policy grants access, then permission is granted.
The following list describes the actions from the preceding interaction diagram. They are ordered from the top of the diagram to the bottom.
- isGeneric()
- Determines whether a generic user needs to be converted to a guest user. If the current user is generic, the conversion to a guest user takes place before any of the remaining methods are invoked.
- setRequestProperties()
- Passes in the request parameters to the command. The request parameters can be used in subsequent access control calls (for example, by returning request parameter-specific data from getOwner() or getResources()).
- isAllowed() [command-level]
- The runtime components determine whether the user has command-level access for either the
controller command or view.Note: The parameters for a controller command are fixed to the current user's ID, the action string
Execute, and the resource class. The resource class is the fully qualified implementation class for the controller command. - getOwner() [command-level]
- The access control policy manager determines the owner of the command-level resource. The
default implementation returns the member identifier (
memberId) of the owner of the store (storeId) that is in the command context. If there is no store identifier in the command context, then the root organization (-2001) is returned. You can return other values that make sense from the perspective of ownership in the command-level access control for your command. - getAndApplyApplicablePolicies() [command-level]
- The access control policy manager finds and processes the applicable policies, based on the specified user, action, resource, and current store. If a policy involves a role, and you specify a store, the policy manager evaluates whether the current user has the specified role in the specified store's organization. When a policy involves a role, and you do not specify a store, the policy manager evaluates whether the current user has the specified role in any organization. If at least one applicable policy grants access, the command-level access check passes, and the policy manager continues to the next step to begin checking for resource-level authorization. Conversely, if none of the applicable policies grant command-level access, the policy manager returns and denies access.
- validateParameters()
- Checks and resolves the initial parameters.Note: Since this method is called after command-level access control, but before the getResources() call, the logic in validateParameters() can be used to resolve data used in getResources().
- getResources()
- Returns an access vector that is a vector of resource-action pairs.
If nothing is returned, resource-level access control checking is not performed. If there are resources that should be protected an access vector (consisting of resource-action pairs) should be returned.
Each resource is an instance of a protectable object (an object that implements the
com.ibm.commerce.security.Protectableinterface). In many cases, the resource is an access bean.An access bean cannot implement the
com.ibm.commerce.security.Protectableinterface, however, the access control check can still occur if the corresponding enterprise bean is protected, according to the information included in Implementing access control in enterprise beans.The action is a string that represents the operation to be performed on the resource. In most cases, the action is the interface name of the command, which is assumed if no action is specified when adding resources to the vector.
- isAllowed() [resource-level]
- The runtime components determine if the user has resource level access to all of the
resource-action pairs specified by
getResources(). - getOwner() [resource-level]
- The resource returns the
memberIdof its owner. ThememberIDdetermines which policies apply. - getAndApplyApplicablePolicies() [resource-level]
- The access control policy manager searches for applicable policies and then applies them. If at least one policy per resource-action pair that grants the user permission to access the resource is found, then access is granted. Otherwise, access is denied.
- fulfils()
- If an applicable policy has a relationship or relationship group specified, a check is done on the resource to see whether the member satisfies the specified relationship, with respect to the resource.
- performExecute()
- The business logic of the command.
- isRetriable()
- Checks whether the command can be tried again in case an ECSystemException is thrown by the performExecute() call.