Key Vault Management
Key vault integration needs to be enabled for AES HMAC to be available for the BOT connect API. Enabling this creates a key vault service that are used to manage keys and these keys are used in BOT connect API.
- Log into Global admin and navigate to Tenants page under Provider tab.
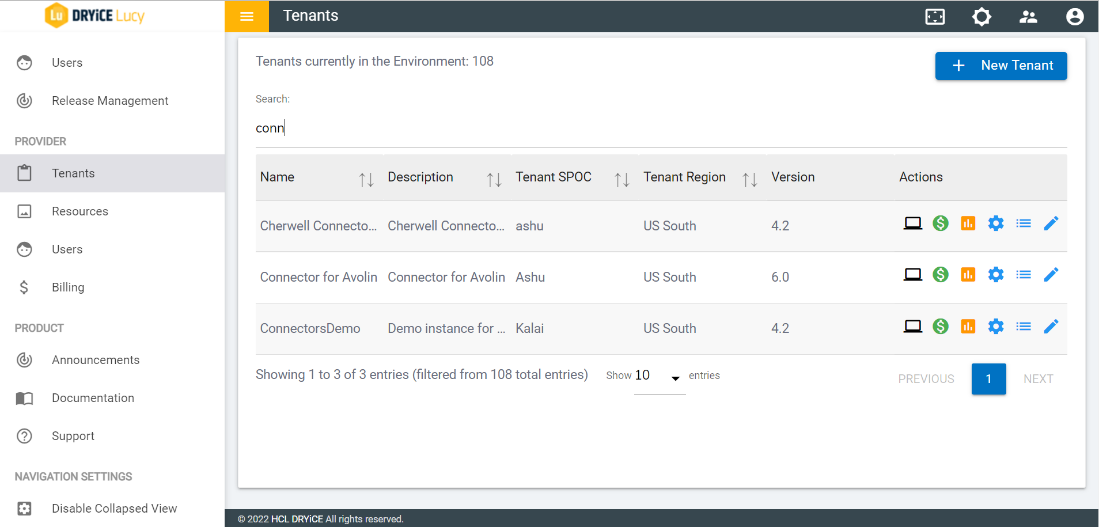
- Click on the Configure button
.png) available in
Actions column.
available in
Actions column. - In tenant’s configuration page, click on Open in “Choose Integrations” card.
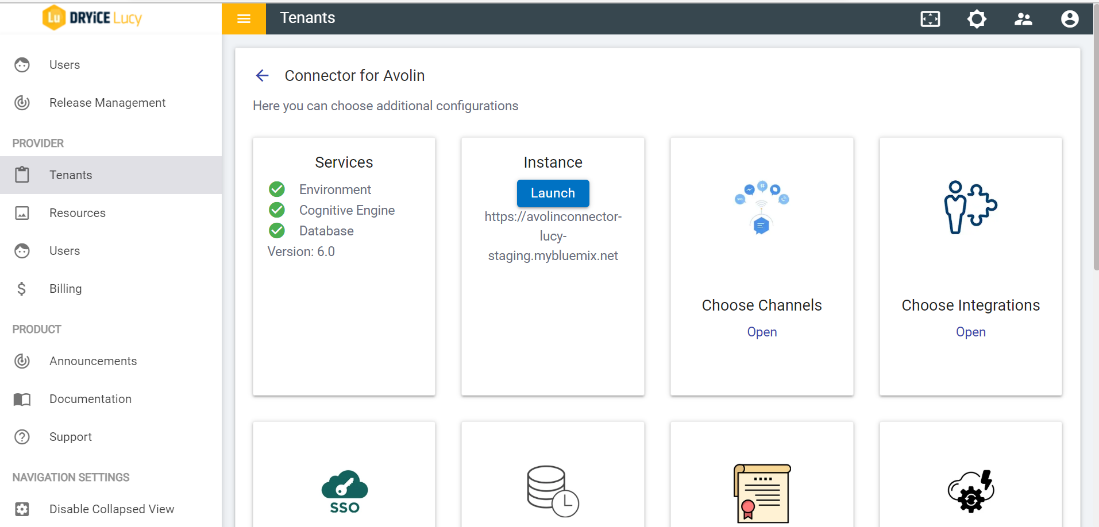
- Click on Open on “Key Vault Services” connector. If it is already enabled, it will have a green check, otherwise it will not have a check at all.
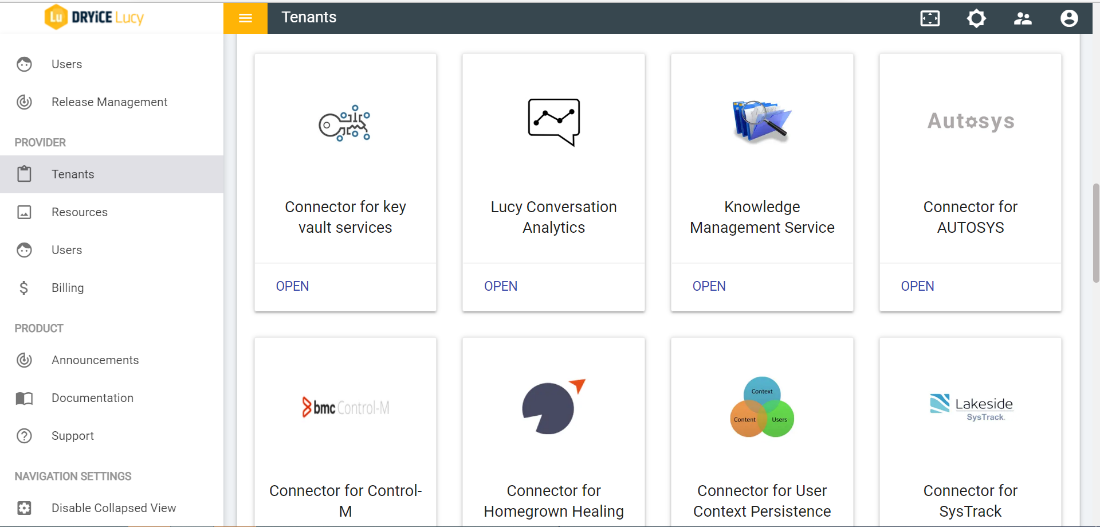
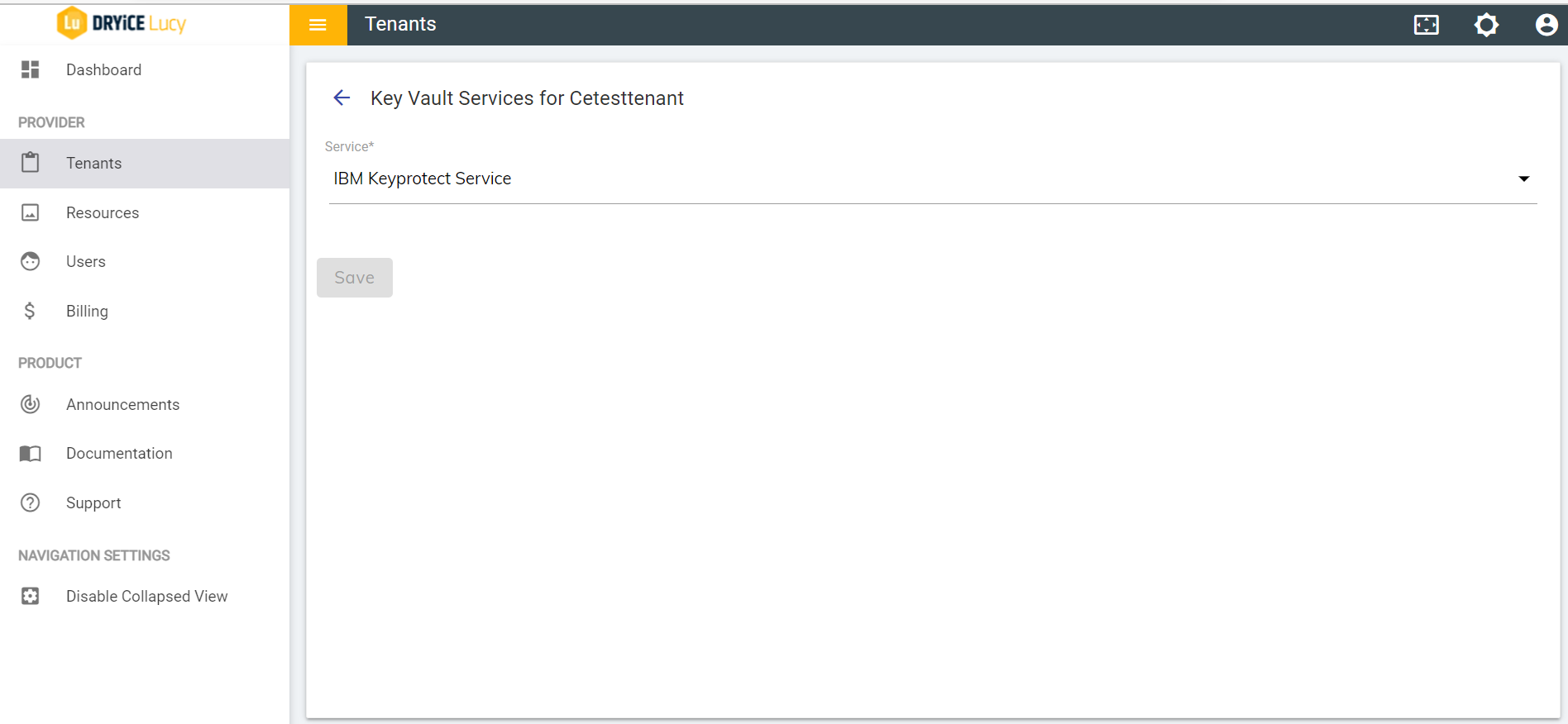
- Click on Open key vault services connector

- The service has a dropdown which has IBM Keyprotect service listed. On choosing the service option SAVE button gets enabled. Save the integration to enable the service.


- On enabling the integration successfully, a success message appears:
-
.png)
Figure 348 – Success Message
- Once the service is enabled it cannot be disabled.
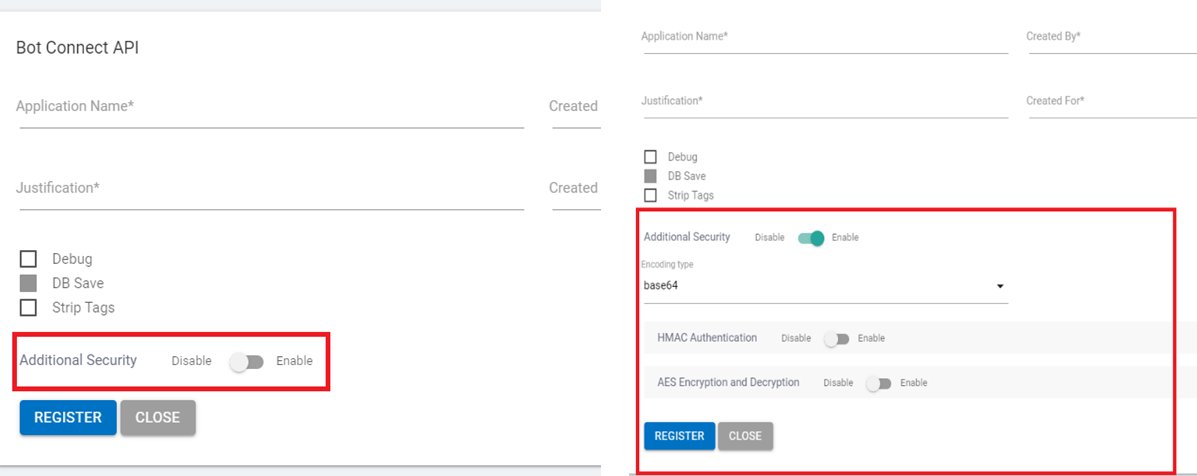
- The following points illustrate how to create a BOT connect API with HMAC and AES encryption.
- If the key vault services integration is enabled in Global Admin there will be an Additional Security toggle that will be visible in the Register your application page for BOT Connect API page. On enabling, other fields related to HMAC authentication and AES encryption are shown below the Additional Security toggle.
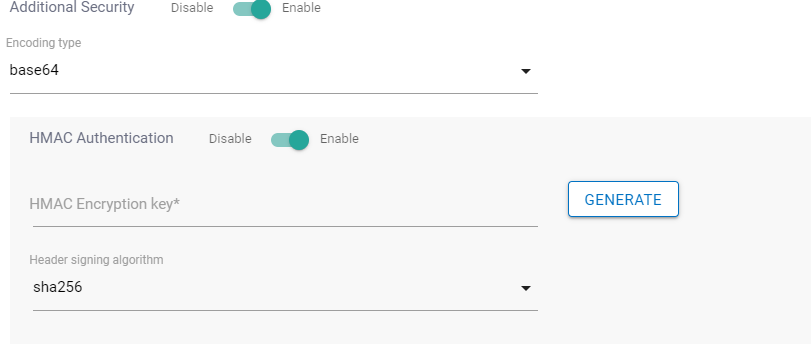
- Encoding type decides the encoding with which HMAC signature is sent, encrypted data is received, and decrypted data is sent.
- User has the option to enable or disable either HMAC Authentication or AES Encryption and Decryption during application registration for BOT connect API. These options are for additional security:
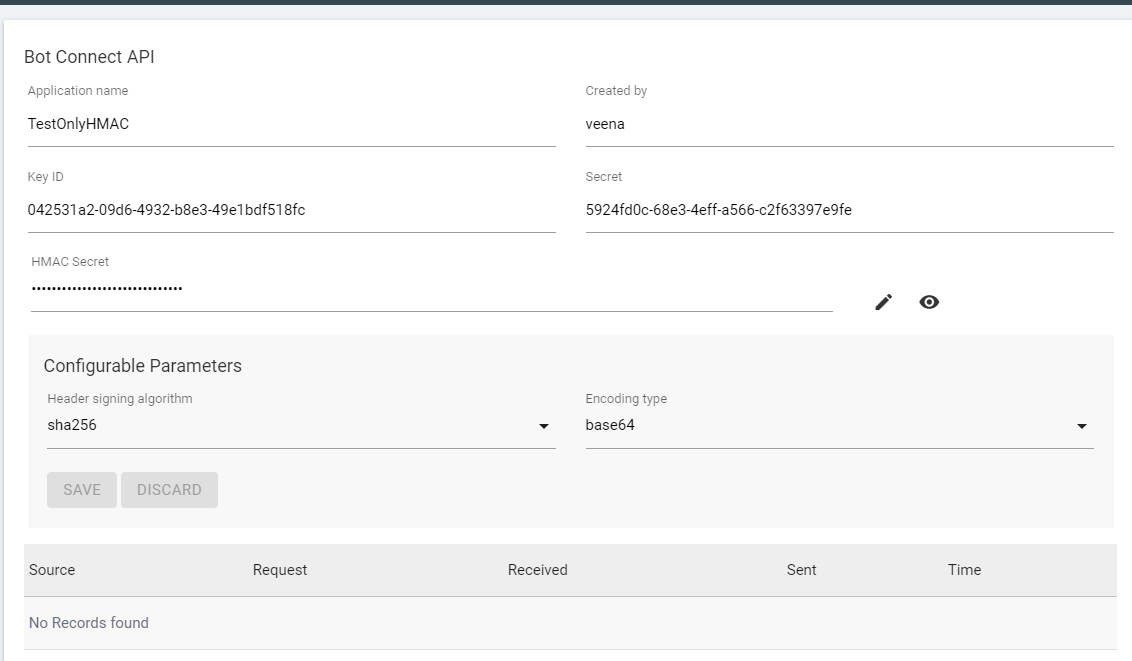
- HMAC Authentication: On enabling HMAC authentication the following fields will be visible:
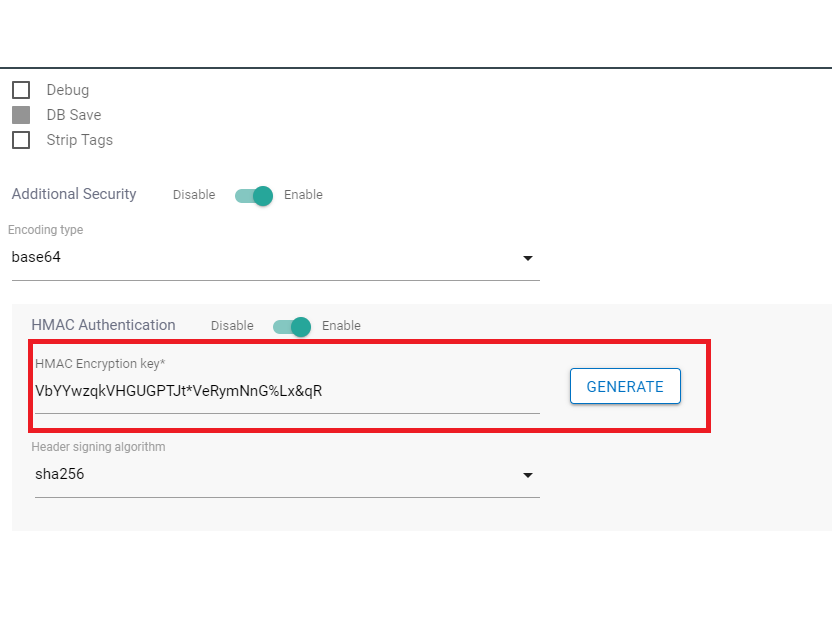
- HMAC Encryption key: It is a mandatory field. It should be of length between 32 and 512.It can contain any alpha numeric character except whitespace.
- Generate: provides user an option to generate an encryption key instead of entering one. On clicking the respective field will have a key generated.
- Header signing algorithm: This will let user choose an algorithm for their HMAC signature. By default, it is SHA256.
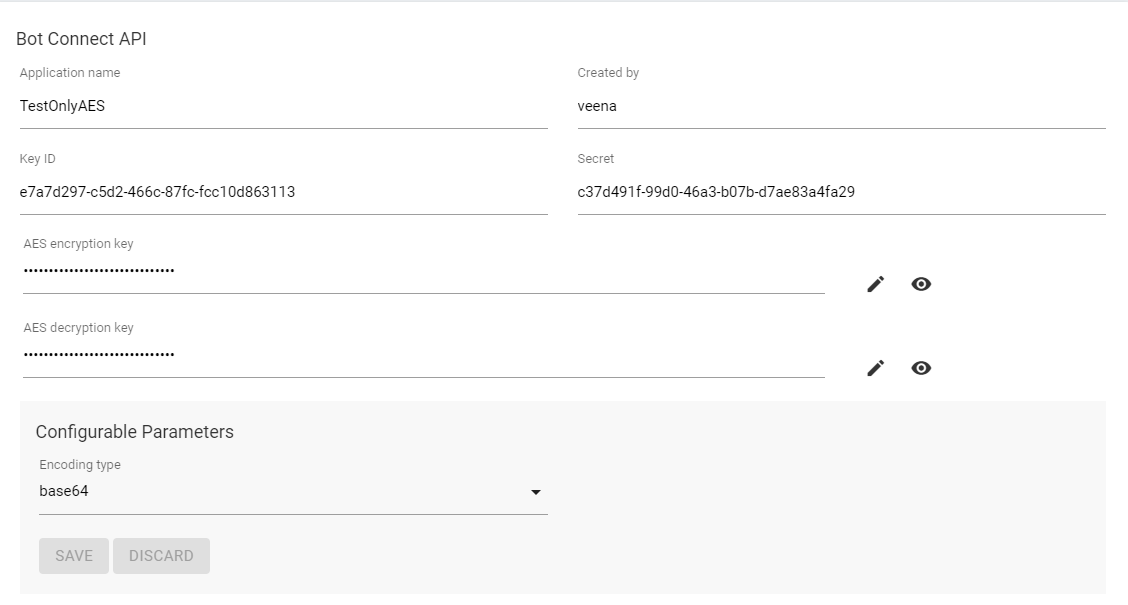
- AES Encryption: On enabling AES Encryption and Decryption fields the following fields will be visible:
- AES encryption key:
- AES decryption key:

- In case of entering key values that doesn’t satisfy the criteria as mentioned, there will be an error on application registration.

- Editing BOT Connect API configurations
- BOT connect API page with both HMAC Authentication & AES Encryption and Decryption

- BOT connect API page with only AES Encryption and Decryption enabled
- BOT connect API page with only HMAC Authentication enabled
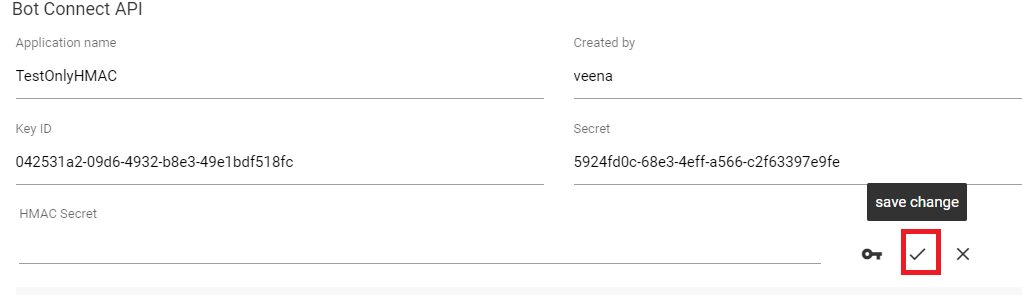
- Editing Keys
- Clicking on view key icon against the Key field displays the value of the key

- On clicking of edit icon against the key, the options to enter a new key are provided

- User can either enter the key manually or can generate a key with Generate key value icon

- Clicking save change icon replaces the old key with the newly generated key
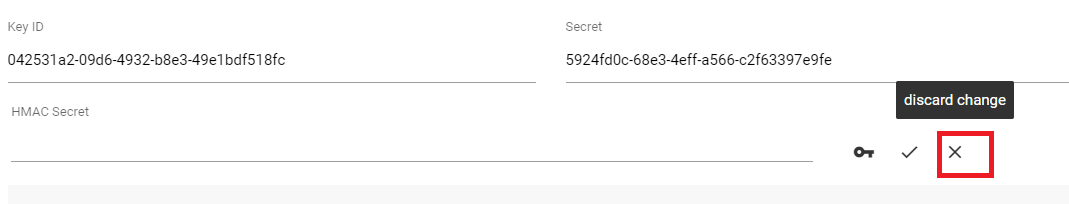
- Discard change value will discard the changes made
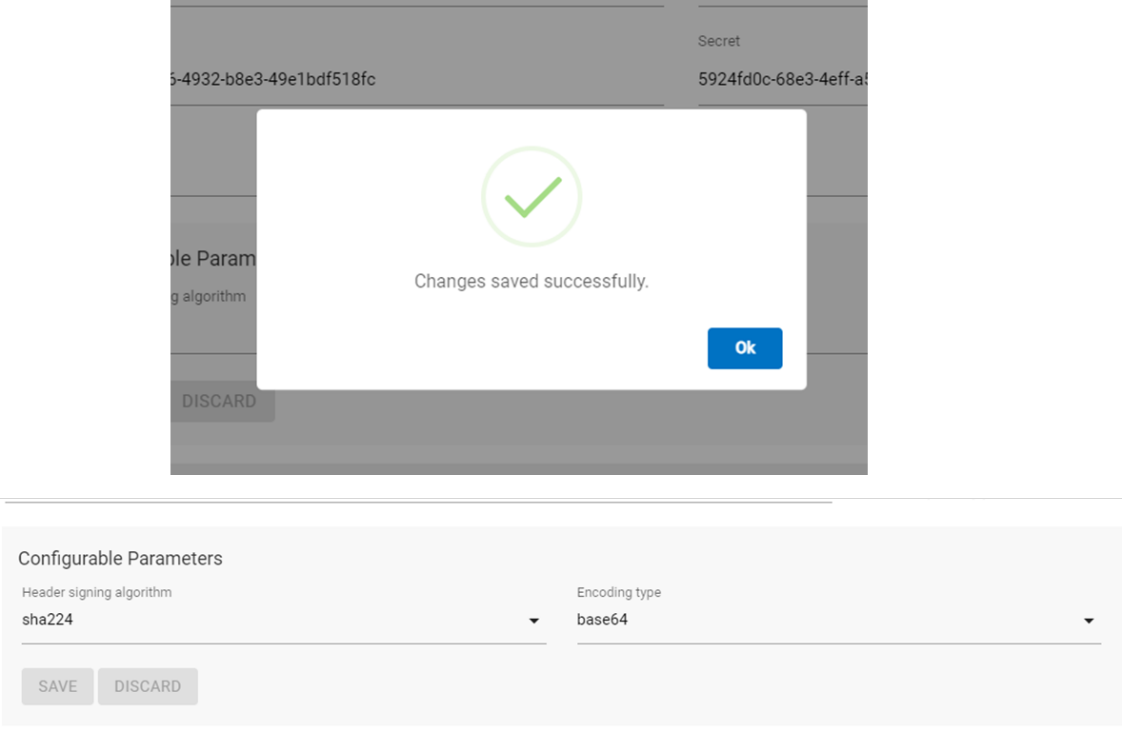
- Configurable Parameters
- Change in any of the configurable parameters will enable SAVE and DISCARD options at the bottom of the page

- Clicking DISCARD, the values of configurable parameters will be set to previous saved value.
- Clicking SAVE changes will be save with confirmation message
.png)