Getting started with application security management
Depending on your role, you can get started with different areas of the product.
About this task
- Read workflow examples to learn how you can start to work with applications: one for customers that are using AppScan Enterprise for the first time, and one for current customers who want to create applications and associate their existing scans with them. Pick the one that best suits your needs, or use parts of them as a starting point to create your own workflow. See Workflow examples for managing application security.
- Get started with a role that closely matches your goals:
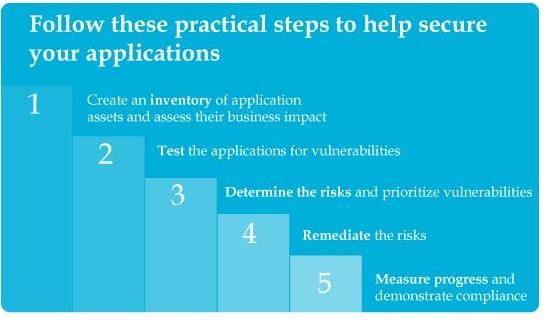
Role Description System Administrator Your goals might include installing, configuring, and administering the Server, Database, and Enterprise Console. Security Analyst Your goals might include: - Audit a large number of applications and triage results
- Monitor a large number of applications on an ongoing basis
- Create and communicate test policies to Development and QA
- Present application security risk reports to Management
Management/Compliance Officer Your goals might include: - Assess the security risk to your organization that your web applications present
- Identify the most problematic applications and take action
- Assess if the security of your web applications is improving
- Identify compliance risk related to various industry guidelines
Application Security Champion Your goals might include: - Configure and run scans on the web applications assigned to you
- Communicate the identified issues to Development for remediation
- Assess the scan findings and verify that they are real vulnerabilities
- Identify the most problematic applications and take action
- Identify the types of issues that are most prevalent to create appropriate education programs
Web Developer Your goals might include: - Fix issues discovered by Information Security, QA and automated build regression tests
- Test the code that you develop (ad-hoc and as part of build regression testing)
QA Tester Your goals might include: - Test applications for security issues based on policies specified by the Information Security team
- Communicate the identified issues to Development for remediation
