Correlation
AppScan analyzes issues found by IAST, DAST and SAST to identify common weak links in the code (correlations) where multiple vulnerabilities can be resolved with a single or consolidated remediation effort.

Each of the core technologies (IAST, DAST, and SAST) has strengths and weaknesses. Correlation allows us to leverage the strengths of each technology, while overcoming its weaknesses with the advantages of the others.
- Enrich DAST issues with IAST and SAST details.
- Prioritize your SAST findings using the accuracy of your IAST and DAST results.
- Validate SAST fixes from the status updates of your IAST and DAST issues.
- Reduce the number of vulnerabilities and remediation tasks by grouping issues together.
Once you have an IAST subscription, correlation is updated automatically whenever any relevant IAST, DAST or SAST issues are found. Existing correlation groups are automatically updated with the new issues, and new groups are created as necessary. No user action is needed.
How it works
Correlation is based on IAST. IAST has access to the application at runtime (like DAST) and is able to see the source code (like SAST). Our automatic correlation algorithm matches IAST issues with DAST and SAST issues. It extracts data from each issue and then uses a variety of heuristics to identify correlations. This brings optimization of the remediation process to a new level. Adding IAST and correlation to your arsenal can reduce the overall number of issues and/or vulnerabilities to be addressed.
Using correlation
Once you have an IAST subscription, correlation is updated automatically whenever any relevant IAST, DAST or SAST issues are found. Existing correlation groups are automatically updated with the new issues, and new groups are created as necessary. No user action is needed.
Examples
Dashboard
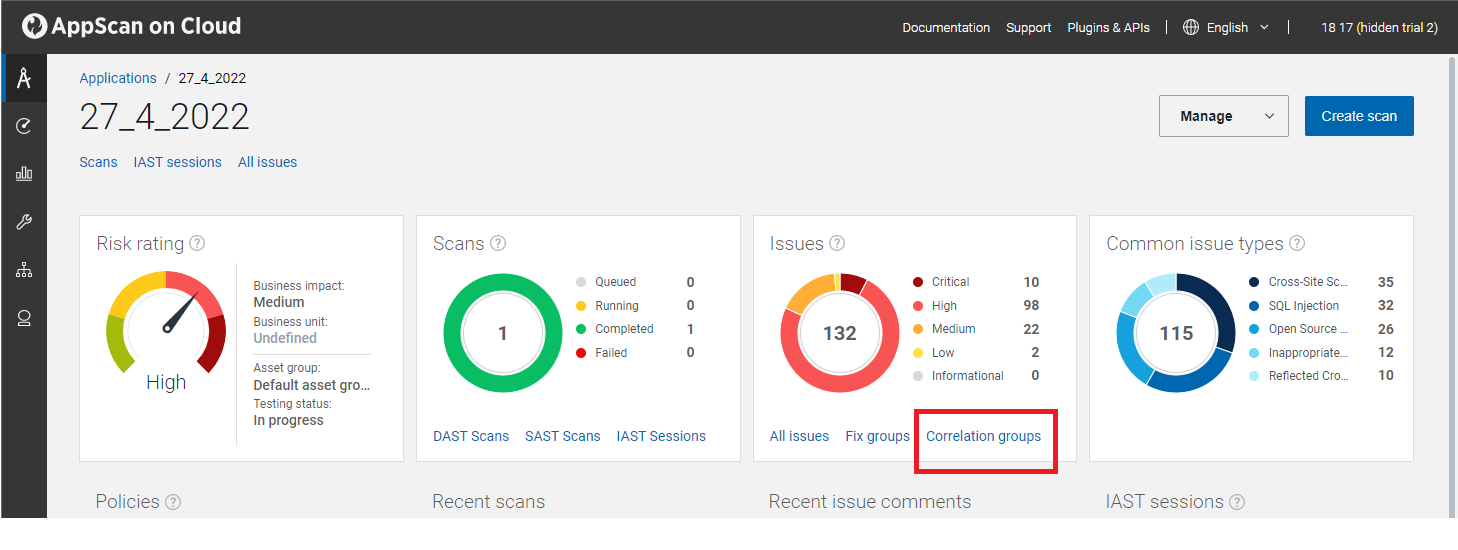
Correlation groups page
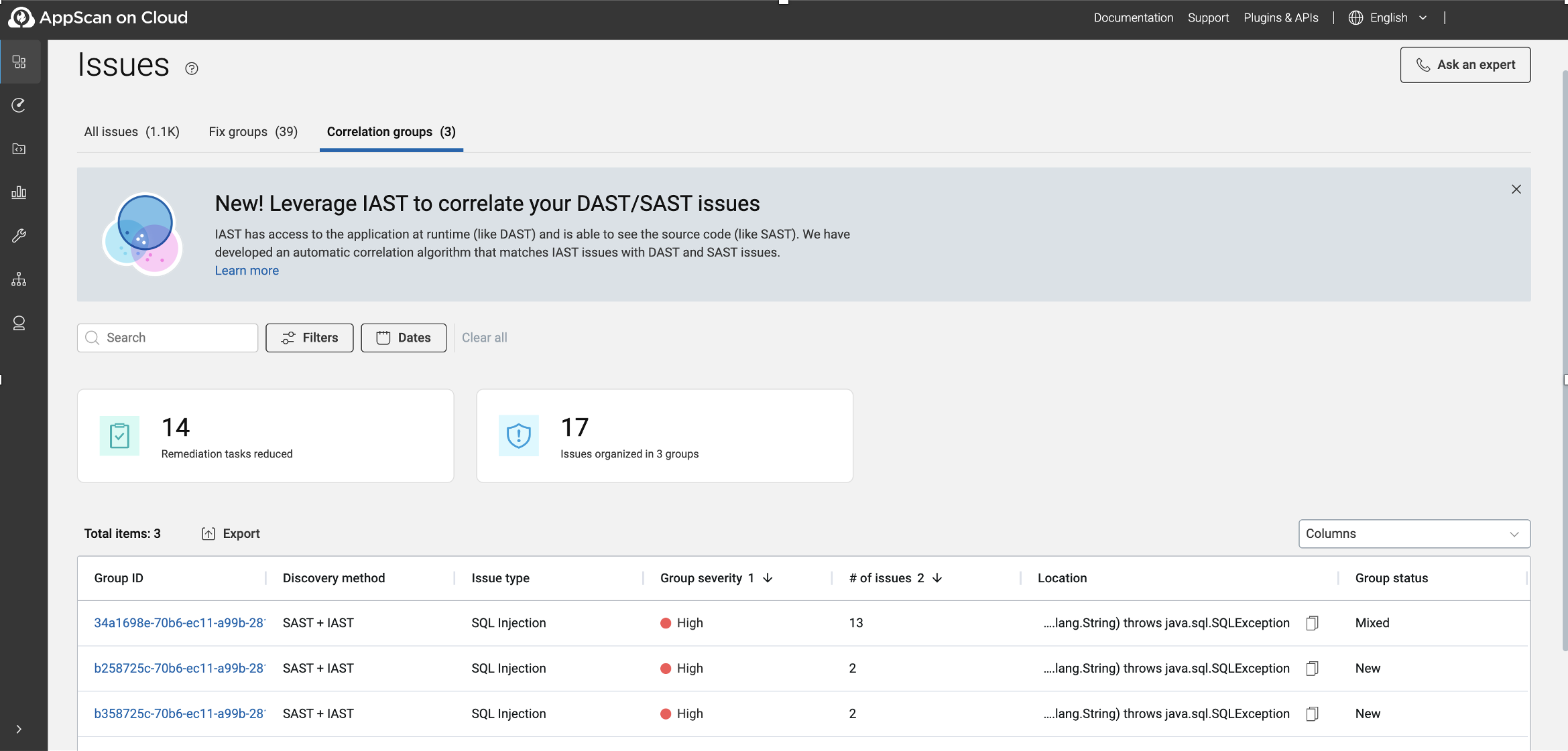
Issues in a group
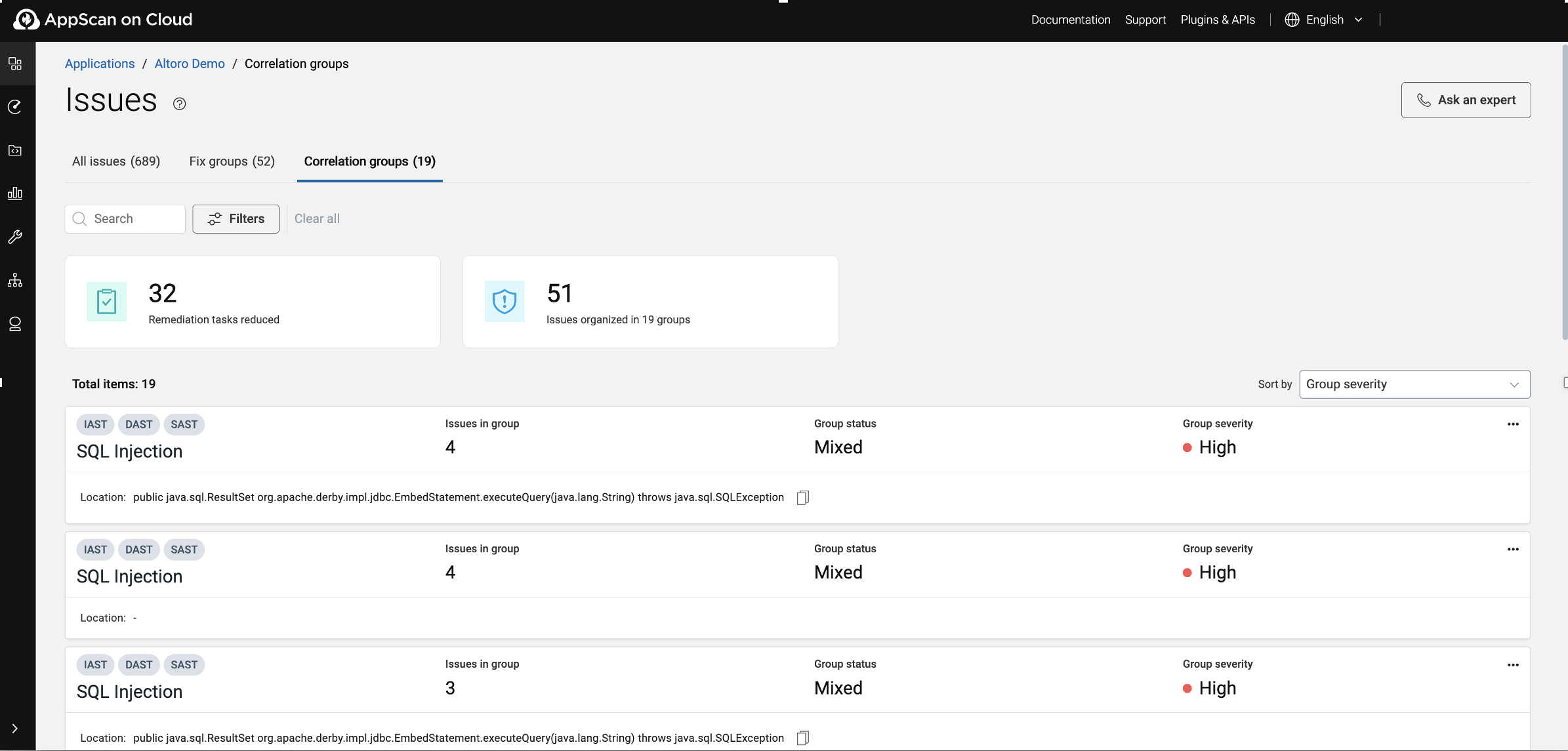
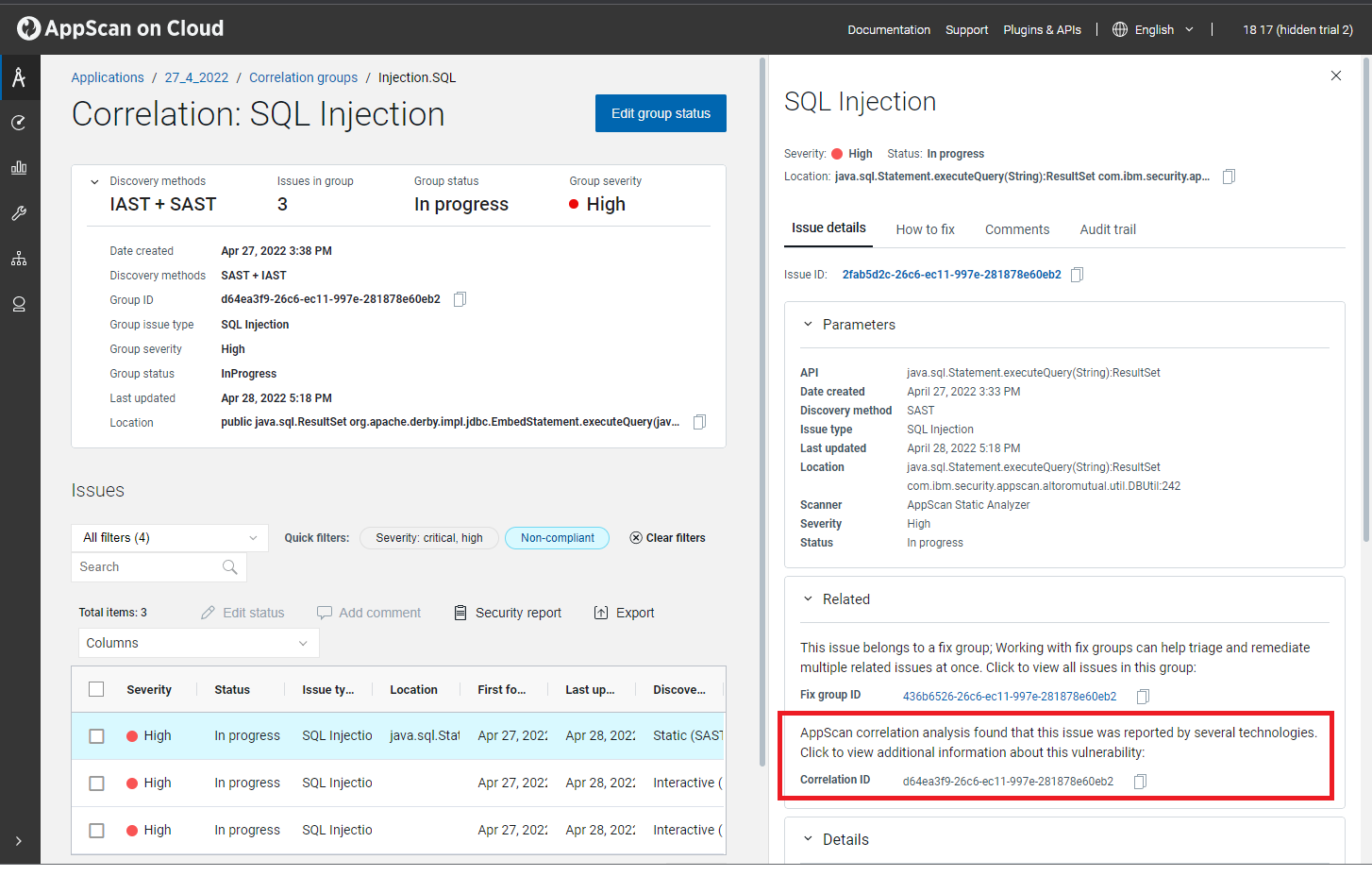
Issue details
Leveraging correlation
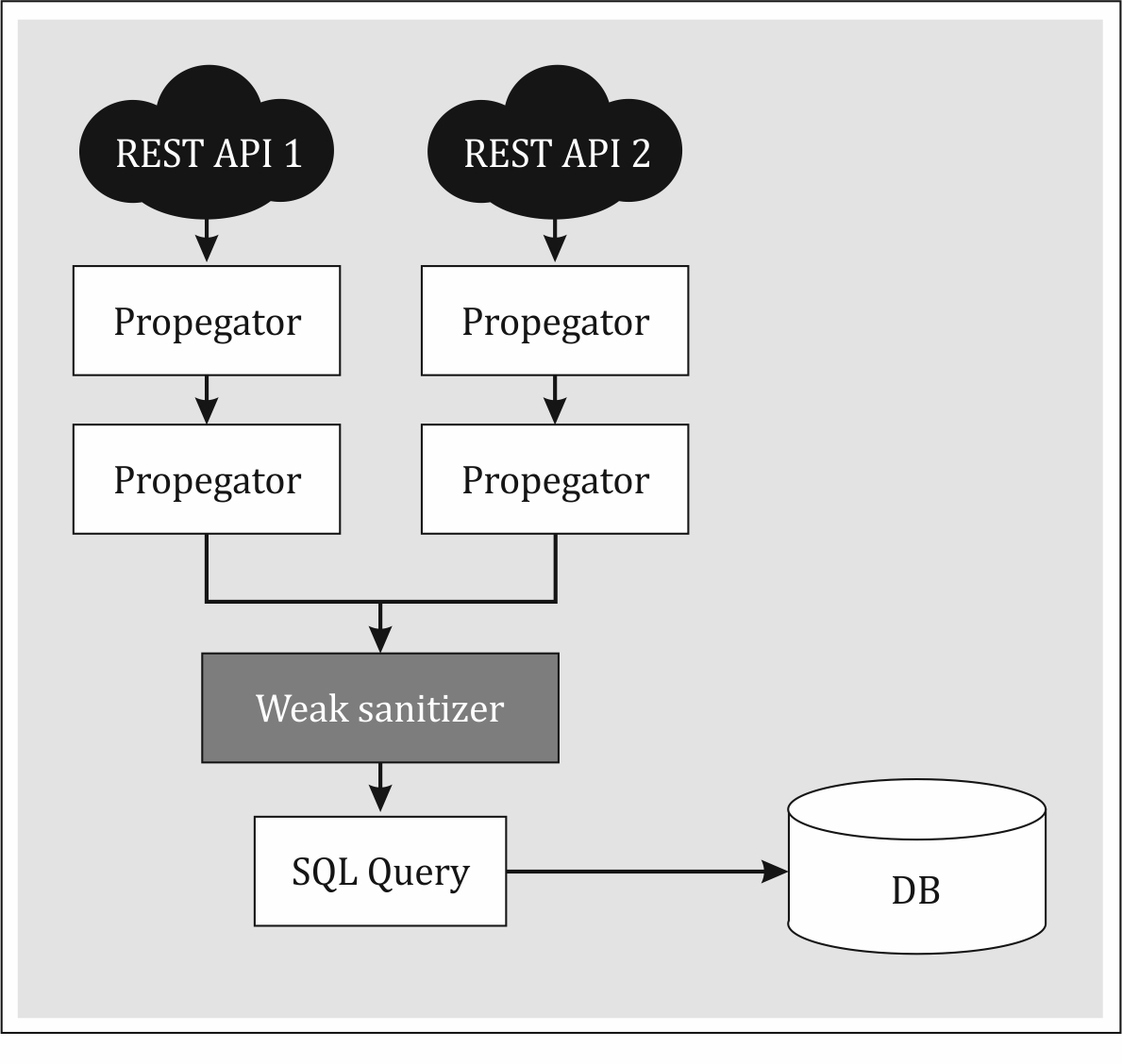
Code reuse is a best practice in software development, but a single weak link can create multiple security vulnerabilities in an application. The diagram below illustrates how a weak sanitizer could cause multiple SQL Injection vulnerabilities. Since REST API 1 has a different route/source to RESP API 2, their vulnerabilities would appear unrelated in scan results.
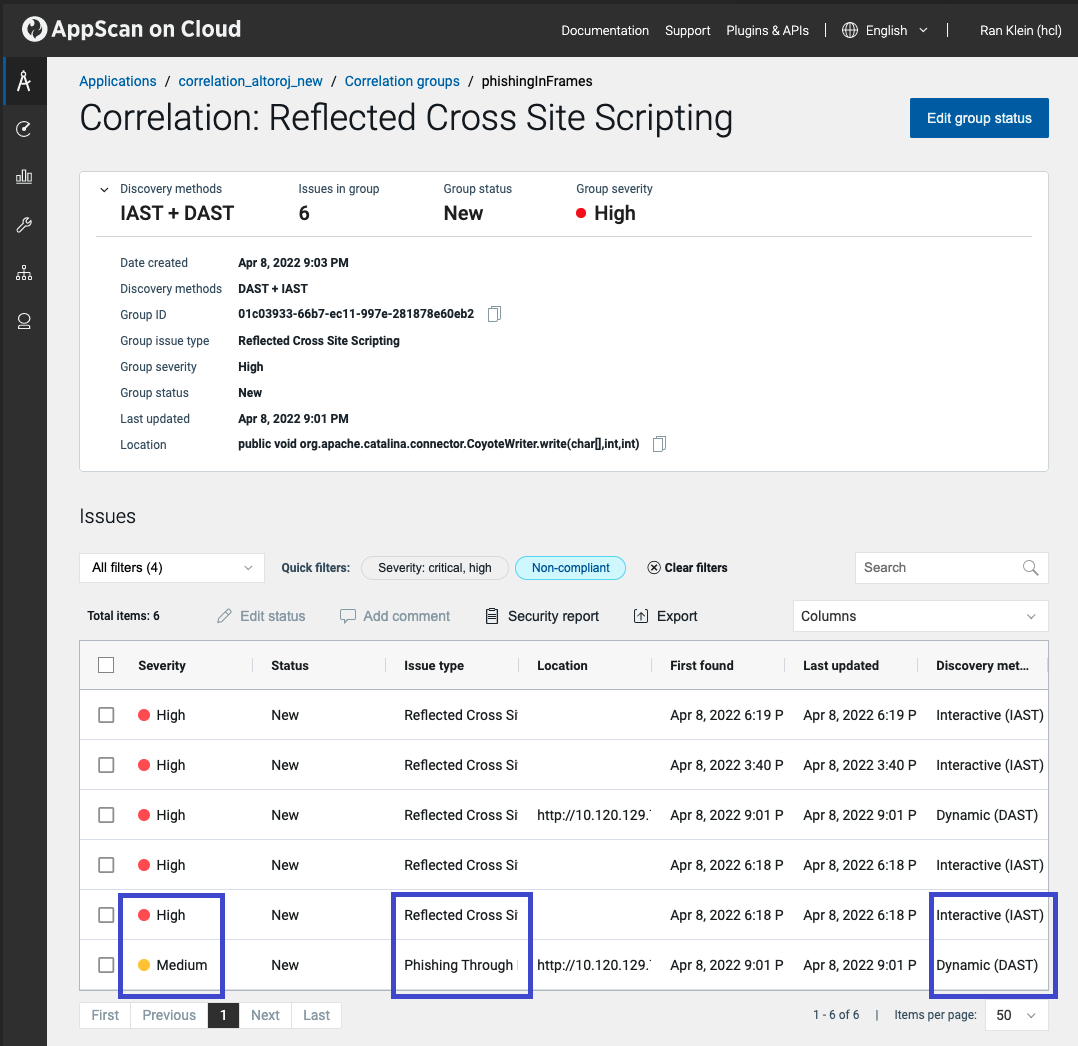
Correlation aggregates vulnerabilities that should be remediated as a single task.
In this example the correlation group includes issues found by different technologies (IAST and DAST), of different issue types, and with different severities. These diverse issues that would not have otherwise been seen as connected can be resolved with a single remediation effort.