Relationship between certificates and keys
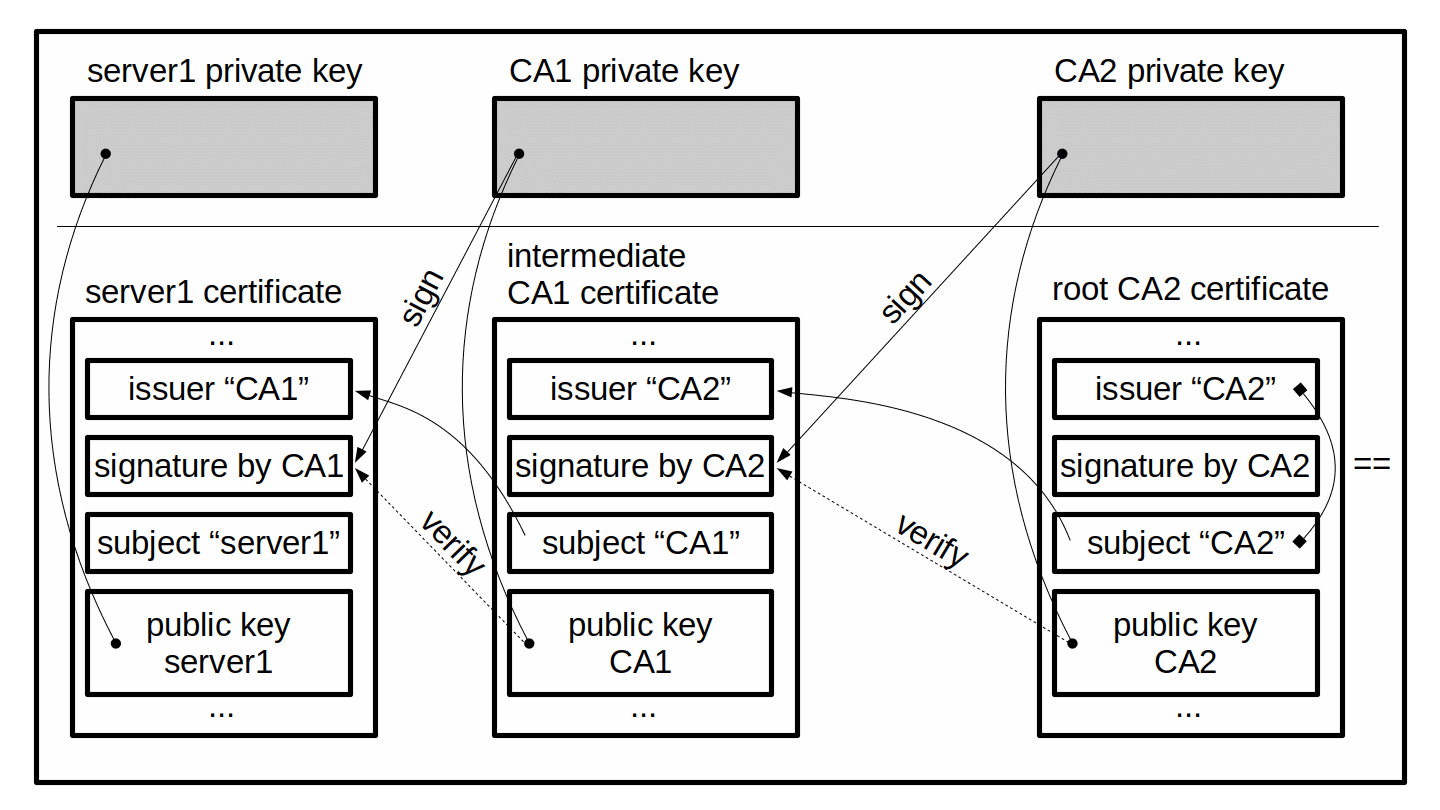
For authentication purposes as in the TLS handshake, certificates and keys are pairs. The private key is kept separate, as it must remain private to its owner. The corresponding certificate not only contains information about the owner (subject) and issuer (as distinguished names), but also the public part of the private-public key pair, as well as a signature. The signature in the certificate is created by the issuer of the certificate. To create the signature, the issuer must use its own private key. This signature then can be verified using the public key of the issuer.
Normally, the server uses a certificate that is issued by a trusted third party, a certificate authority (CA). The certificate used by the server therefore is called a user certificate, or also server certificate. The CA certificate is the certificate of the CA that issued and signed the server certificate. The CA certificate contains the CA's public key needed by the client to verify the CA's signature in the server certificate. With that, the server owns its private key and the server certificate, whereas the client only possesses a copy of the CA certificate.
If the CA is trusted by all parties, then the CA certificate is issued and signed by the CA itself. In such a certificate the issuer name and the subject name are the same, and the certificate is called a root CA certificate. The client therefore only needs this root CA certificate to authenticate a server.
In some cases, a client may not directly trust the CA that issued a server certificate. In this case, the client possesses a copy of the CA certificate that in turn is issued and signed by yet another CA. The client sees that in the CA certificate the issuer and subject names are different. As the client does not trust this intermediate CA, the client also needs to find a root CA certificate that issued and signed the intermediate CA certificate. It becomes obvious, that this can recursively repeat itself for a couple of times, until the client finds a trusted root CA certificate. The certificates involved therefore build a so called certificate chain, with the server certificate at one end, the root CA certificate at the opposite end, and a varying number of intermediate CA certificates in the middle.
It is possible, that a server itself issues its own server certificate. Such a certificate is called a selfsigned (server) certificate. In this case, there is no CA involved, and the client does not need any CA certificate to authenticate the server. Instead, the client possesses an exact copy of the server's selfsigned certificate (received by "other means"). To authenticate a server, the client checks that the copy of the self-signed certificate in its own possession exactly matches the server certificate received during the TLS handshake.