Creating a Directory Assistance document enabled for Directory Sync
The first step to configure Directory Sync is creating a Directory Sync-enabled Directory Assistance document in the directory assistance database.
Before you begin
- Creating and replicating a directory assistance database.
- Setting up servers to use a directory assistance database.
About this task
Procedure
- Using an ldpsearch client or some other tool, test that the HCL Domino® servers can connect to the Active Directory server.
- From the Domino® Administrator, choose to open the Domino® administration server for the domain. Click OK.
- Click the Configuration tab.
-
In the navigation pane, expand . If you see
Server Error: File does not exist, the administration server is not set up to use the directory assistance database. - Click Add Directory Assistance.
-
On the Basics tab, complete these fields:
Table 1. Basics tab Field
Enter
Domain type
Select LDAP.
Domain name
A domain name of your choice that is different from the domain name specified for any other Directory Assistance document (HCL Notes® or LDAP) in the directory assistance database. For example, Renovations AD.
Make this domain available to
Select Directory Sync.Note: Do not select Notes clients and Internet Authentication/Authorization or LDAP Clientsunless you are also using the LDAP directory for these purposes.Group authorization
Select No.
Enabled
Select Yes
Note: You can also enable and disable directory assistance for this directory from the main view of the Directory Assistance database. Select the directory assistance record for the directory and, on the toolbar, click Enable/Disable. -
(Optional) On the Naming Contexts (Rules) tab, for each rule you want to
define for the directory, complete the following fields. For more information on naming rules, see
Directory assistance and naming rules.
Table 2. Naming Contexts (Rules) tab Field
Enter
N.C. #
Enter a naming context (rule) that describes the user names in the LDAP directory.
Enabled
Choose one:
- Yes to enable a rule
- No (default) to disable a rule
Trusted for Credentials
Choose one:
- Yes to allow servers to use credentials in the LDAP directory to authenticate Internet clients whose distinguished names in the directory correspond to the rule. If you want to add Active Directory users or groups to the ACLs of Notes databases that are accessed over HTTP, select Yes.
- No (default) to prevent servers from using this directory to authenticate Internet clients whose distinguished names in the directory correspond to the rule.
-
On the LDAP tab, complete these fields:
Table 3. LDAP tab Field
Enter
LDAP Configuration section Hostname
The host name for the Active Directory server, for example, ad.renovations.com. A Domino® server uses this host name to connect to the directory server.
Click Suggest to look up the host names of LDAP servers listed in your DNS.
Click Verify to verify that the host name is an active LDAP server.Note: You can specify one host name only.Port values entered in this field override those specified in the Port field. If no port is specified in this field, then the value specified in the Port field is used.
LDAP Vendor Select Active Directory.
Optional authentication credential for search
For Optional Authentication Credential enter a user name and a password for a Domino® server to present when it connects to the Active Directory server. The Active Directory server uses the name and password to authenticate the Domino® server. If you don't specify a name and password, a Domino® server attempts to connect anonymously.
Click Verify to verify that the user name and password you entered is valid on each host name.
This setting may affect change detection for LDAP servers.
Base DN for search
A search base, if the LDAP directory server requires one. For example:
o=Renovationso=Renovations,c=USClick Suggest to search each host name for likely search bases.
Click Verify to verify that the search base is accessible on each host name using the configured credentials.
This setting may affect change detection for LDAP servers.
Connection Configuration section Channel encryption
Choose one:
- TLS (the default) to use TLS when a Domino® server connects to the Active Directory server
- None to prevent TLS from being used.
If you choose TLS, make selections in these associated fields:
- Accept expired TLS certificates
- TLS protocol version
- Verify server name with remote server's certificate
Port
The port number Domino® servers use to connect to the Active Directory server.
- If you choose TLS in the Channel encryption field, the default port is 636.
- If you choose None in the Channel encryption field, the default port is 389.
If the directory server doesn't use one of these default ports, enter a different port number manually.
Advanced Options section Timeout
The maximum number of seconds allowed for a search of the directory; default is 60 seconds.
If the Active Directory server is also configured with a timeout value, the smaller value takes precedence.
Maximum number of entries returned
The maximum number of entries the Active Directory server can return for a name for which a Domino® server searches. If the directory server also has a maximum setting, the smaller value takes precedence. If the directory server times out, it returns the number of names found up to that point.
Default is 100.
Dereference alias on search
Choose one to control the extent to which alias dereferencing occurs during searches of the directory:
- Never
- Only for subordinate entries
- Only for search base entries
- Always (default)
If aliases are not used in the directory, selecting Never can improve search performance.
Preferred mail format
Select Internet Mail Address. Enable name mapping Do not select. Type of search filter to use
Select Active Directory.
- Click Save & Close.
-
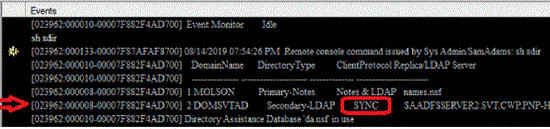
From the server console of the Domino® administration server, run the following command to confirm that the Directory Sync configuration in the Directory Assistance document is set up correctly:
show xdirYou should see console output with the string SYNC similar to the following example: