How to identify on which targets to apply content
BigFix helps you identify on which targets to apply content.
One of the main strengths of BigFix is its ability to determine which targets the content applies to, in other words, which computers need that content. This is accomplished using Relevance expressions. Relevance expressions are part of the content definition and their scope is to interrogate the hardware and software properties of your managed clients to ensure that a patch or a maintenance activity, for example, is applied to only those computers that need it, and to no others.
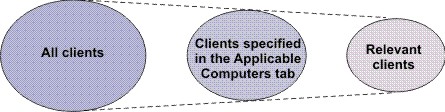
When you define a content, you specify in the Applicable Computer tab a set of computers that can be targets for that content. Relevance evaluation narrows down this set of computers and selects only those computers that really must apply that content.
- Relevant action
- It represents a violation to be remediated by running the instructions stated in the action description using the Action script language. Actions incorporate relevance clauses that can be customized at run time in the Take Action dialog.
- Relevant Fixlet
- It means that the computer is out-of-compliance with a policy
rule. When the Fixlet is relevant, the actions that are contained
in the Fixlet definition can be run to remediate the issue. After
the actions run, the relevance is evaluated again to check if the
vulnerability is fixed.
For example, a Fixlet can be used to install Symantec Endpoint Protection. This Fixlet is relevant for those computers where Symantec Endpoint Protection is not installed. After the Fixlet is installed on all the relevant computers, it is no longer marked as relevant. If, later, Symantec Endpoint Protection is uninstalled on one or more computers specified in the Applicable Computers tab, the Fixlet is marked as relevant again.
- Relevant task
- It indicates that the computer has a violation of a configuration
standard or requirement or it must run maintenance activities.
For example, a task can be used to start Symantec Endpoint Protection. This task is relevant for those computers where Symantec Endpoint Protection is not active.
When the task is relevant, the actions that are contained in the task definition can be run to remediate the issue. After all the steps of the actions have completed, the task is marked as not relevant on the computer. The relevance expression is not evaluated again. As a best practice, success criteria can be used to determine whether the actions completed successfully to ensure that the remediation efforts succeeded in solving the problem.
- Relevant baseline
- It informs that one or more of the Fixlets that it contains is relevant for one or more
computers that satisfy the criteria of both relevance expressions, those specified in the Fixlet
description and those specified in the baseline Applicable Computers tab. If nothing is specified in
the baseline Applicable Computers tab, then no restriction applies to the Fixlet or task
applicability.
For example, a baseline might contain Fixlets and tasks for both Windows and Linux operating systems, however, if the baseline Applicability Computers states that only Windows computers are relevant then only the Fixlets and tasks that are applicable for Windows are considered.
Note: Even though the baseline contains tasks, the Fixlet behavior is applied. - Relevant analysis
- It runs property queries, according to their query intervals, and sends the results back to the server. The results are then displayed on the BigFix console.
When a computer evaluates relevance of a newly-gathered document, for example a Fixlet or an analysis, it posts the results, and these results are then displayed on the BigFix console. After the initial evaluation, the computer only reports changes, because there is no benefit in using network bandwidth to report the same result.
Relevance expressions are written in a human-readable proprietary language called Relevance Language.
If you have Custom Content authorization, you can write a new relevance expression or modify existing expressions, to tailor content delivery to your needs. For more information about assigning authorizations to operators, see Mapping authorized activities with permissions.