Test Automation in AppScan® Enterprise using AppScan Proxy Server
The AppScan Proxy Server enables you to record traffic to use as Explore data in your AppScan Enterprise (ASE) job. The AppScan Proxy Server is a system for managing recording proxies. Proxy instances can be created on demand to record traffic that will later be used for a DAST scan. This document describes how to set up and use the proxy server.
Overview
- Using the AppScan Proxy Server, you can automatically start a recording proxy. The requests from the automation framework to the web app are then recorded as they are sent through this recording proxy. The traffic is saved in HAR format in a .dast.config file, that you can later upload to be used by AppScan Enterprise (ASE) as Explore data for a scan.
- You can also record traffic manually, through the proxy server, to create a .dast.config file.
- You can also upload your own HAR file directly to ASE, without using the proxy server.
This diagram depicts the automated scan flow with AppScan® Enterprise.
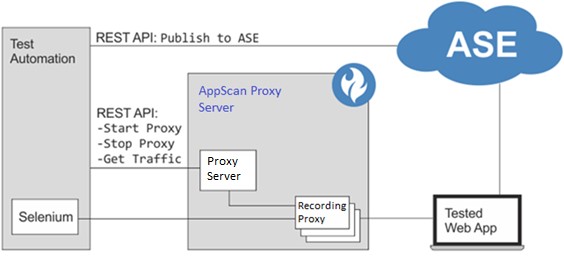
Typical Workflow
Install the AppScan Proxy Server
- Download one of the current versions of Node.js (v12 or later) and install it on your machine. If your service is FIPS compliant, you must use a FIPS compliant Node.js server.
- Unzip DastProxyServerStandalone.zip to a folder on your machine.
- To overwrite a default port for the Proxy Server to run on: Configure the port setting in Settings.json.
Configure the AppScan Proxy Server
FIPS compliant mode
- Locate the file Settings.json in the root folder of the proxy server and open it in a text editor.
- Locate the setting requireFips and change its value from false to true.
- Save the file.
Proxy server connection
- To set a default port for the Proxy Server to run on: Configure the port setting in Settings.json.
- For a secure (SSL) connection to the Proxy Server: Configure your own PEM or PKCS12 certificate
in Settings.json.
- A PEM certificate requires two files (full paths) and a PKCS12 certificate requires one file (full path) and a password.
- Do not forget to escape characters as needed both in file paths and password, for instance a
password such as abc!”123 would become abc!\”123 (the “ is escaped).
Example using openssl to create a PEM certificate:
openssl req -newkey rsa:2048 -new -nodes -keyout key.pem -out csr.pem
openssl x509 -req -days 365 -in csr.pem -signkey key.pem -out server.crt
Example using openssl to convert the PEM certificate to PKCS12 certificate:
openssl pkcs12 -export -out certificate.pfx -inkey key.pem -in server.crt
Example using Java’s keygen tool to convert a JKS certificate to PKCS12 certificate:
keytool -importkeystore -srckeystore certificate.jks -srcstoretype JKS -destkeystore certificate.p12 -deststoretype PKCS12
Root Certificate
If the application you are testing uses SSL (HTTPS), the AppScan recording proxy must act as a man-in-the-middle to record traffic. To do this it must have a root certificate that it can use to sign its communication with the app.
- Install the certificate generated by the AppScan Proxy Server on your machine(s):
- Use the REST API to download the self-signed Root Certificate Authority, used by the AppScan Proxy Server, as a PEM file.
- Install it on the browser used for the Explore, or wherever needed (depending on where the traffic is sent from).
- Import your own root certificate to the AppScan Proxy Server. Supported certificate formats are
PKCS12 (.P12, .PFX), JKS:
- Open a command line window and navigate to the installation folder on the proxy server machine.
- Run the following command:
.\Java\jre\bin\java -jar DastProxy.jar -irc [path to certificate file] -ircp [password]
Note: To see the complete command usage, run the .\Java\jre\bin\java -jar DastProxy.jar command.Important: Since the certificate will be saved on the proxy server, it is recommended that you use a dedicated test certificate.
- Provide your own fixed server certificate (not a root certificate) in the StartProxy command.
Set Proxy Inactivity Timeout
If a recording proxy instance is not closed with a close command after use, it remains open and listening on the port. Recording proxy instances are closed automatically if they are idle for a predefined time.
The default inactivity timeout for recording proxy instances is 60 minutes. You can change this value by changing the value of inactivityTimeoutInMinutes in the Settings.json file saved in the installation folder.
Encrypt Traffic
By default, the traffic (.dast.config) file is not encrypted. To configure the server to encrypt all traffic, change the "encryptDastConfig" value to “true” in the Settings.json file, found in the installation folder.
Chained Proxy
If you need to define more than one chained proxy, or exceptions to the proxy, use the chained proxy rules file (proxy.chain) found in the installation folder. The file includes instructions for use.
Start the Proxy Server
You can simply start the Proxy Server, or run it as a service (below). Note that you can’t do both in parallel.
- Run the command: node app.js [port]
where, *port = the port on which the Proxy Server listens for REST API requests.
- If you do not define the port when starting the Proxy Server, the port set in the Settings.json file is used, if none is defined there, port 8383 is used.
- There is no need to stop the Proxy Server, you can leave it running permanently.
Start as a Service
To start the service, run the command:
node service.js --install
node service.js --start
Additional Service Commands
You can print this list by running the command node service.js --help
| Service commands | Description |
|---|---|
| --start | Start the service |
| --stop | Stop the service |
| --install | Install the service |
| --uninstall | Stop and uninstall the service |
| --h | --help | Output usage information |
Using the Proxy Server
Once the Proxy Server has started, you can start new recording proxy instances, to record the traffic of your application.
- To start a proxy instance, use the REST API request: StartProxy
- Send your traffic to the application you are testing, via the defined recording proxy port.
- When done, send the REST API request: StopProxy.
- Download the .dast.config file, which contains the recorded traffic, by sending REST API request: Traffic. The file is a ZIP file containing one or more .har (HTTP Archive) files. When you download this file, the data is deleted from the AppScan Proxy Server.
- You can use the .dast.config file to update the Explore data of an existing job, using the ASE REST API. See the documentation link: https://<domain>:9443/ase/api/pages/apidocs.html. For more details, see Proxy Server API commands section.
Proxy Server API commands
Once the Proxy Server has started, you can start a recording proxy instance, and send your traffic to your application.
Documentation
To view the complete REST API documentation in Swagger, type in a browser: http(s)://<server>:<port>
All commands point to an endpoint that looks like this:
http(s)://[server]:[port]/automation/
server = IP address of the machine on which the Proxy Server is installed (default is localhost)
port = port on which the Proxy Server listens
"StartProxy"
- URL: http://[server]:[port]/automation/StartProxy/<recordingPort>
- Request type: POST or GET (if using chainedProxy, proxyCertificate, and clientCertificate the request is POST; otherwise it is GET)
"StopProxy"
- URL: http://[server]:[port]/automation/StopProxy/<recordingPort>
- Request type: GET
"StopAllProxies"
Stop all running recording proxies. This command stops all recording proxies on all ports, including those started by other users.
- URL: http://[server]:[port]/automation/StopAllProxies
- Request type: POST
"EncryptDastConfig"
- URL: http://[server]:[port]/automation/EncryptDastConfig
- Request type: POST
"DownloadEncryptedDast"
- URL: http://[server]:[port]/automation/DownloadEncryptedDastConfig/<uuid>
- Request type: GET
"Traffic"
- URL: http://[server]:[port]/automation/Traffic/<recordingPort>
- Request type: GET
"Certificate"
- URL: http://[server]:[port]/automation/Certificate
- Request type: GET
Updating the AppScan Proxy Server
Before dropping the AppScan Proxy Server and moving to a newer version, make sure to copy any configuration files you may have modified into the new folder.
If you installed the Proxy Server as a service, you must uninstall the service before updating (see Additional Service Commands), and reinstall it after wards.